This Halloween the MITRE ATTACK team released version 16.0 of the popular framework, including significant changes in the Enterprise, Mobile, ICS techniques, as well as in many CTI entities (campaigns, groups, etc.). You can check out a good overview of the changes in their blog post, and in the release notes.
There were two particular new subtechniques that we really liked so far:
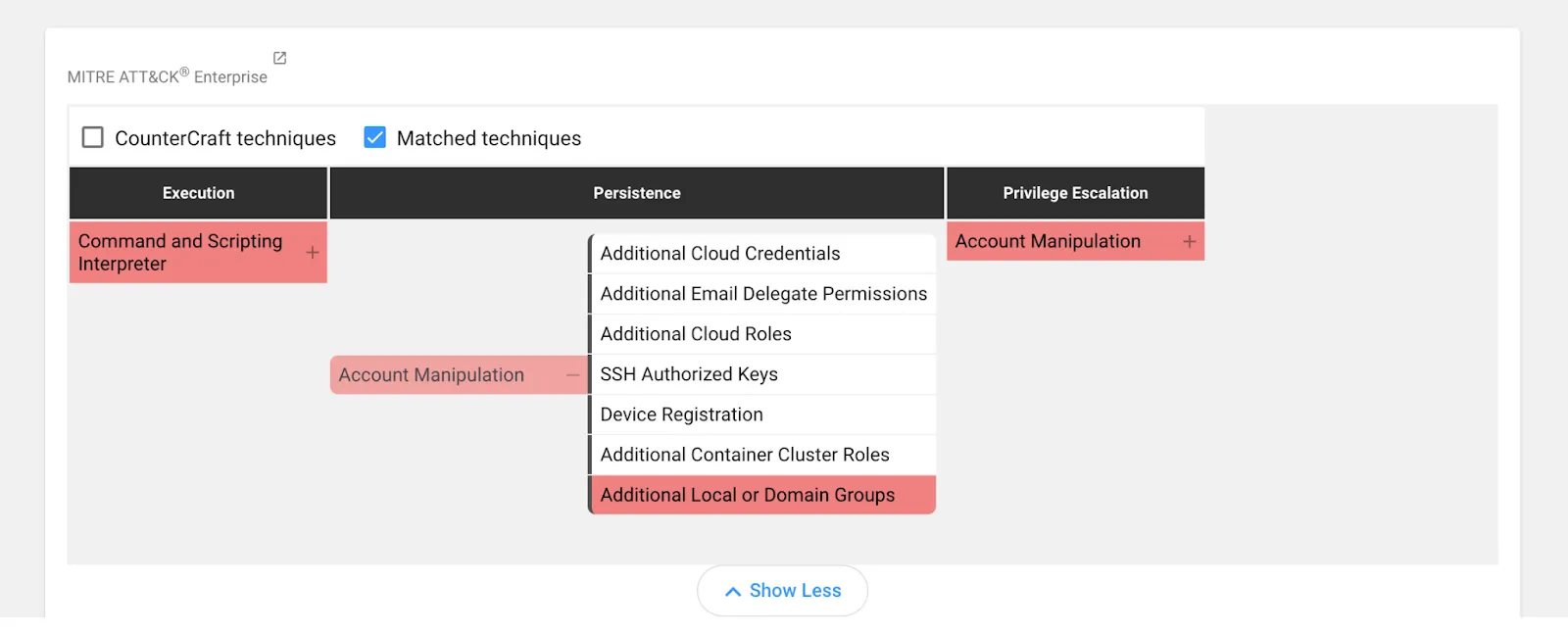
- T1098.007 Account Manipulation – Additional Local or Domain Groups: as it is pretty frequent to see attackers creating new accounts and adding them to some special security groups (like Administrators, or Remote Desktop Users) for persistence or privilege-escalate purposes.
- T1546.017: Event Triggered Execution – Udev Rules the use of Linux udev rules for persistence. Udev is the Linux kernel device manager that dynamically manages device nodes, handles access to pseudo-device files in the /dev directory, and responds to hardware events, such as when external devices like hard drives or keyboards are plugged in or removed.
We immediately started working on supporting the new v16 version in our product, and as you can see in the following images, we’ve turned it around in less than a weekend. All existing customers will automatically start using the v16 of the ATT&CK framework starting today.
Here’s a glimpse of what the new MITRE ATT&CK updates look like in our platform:
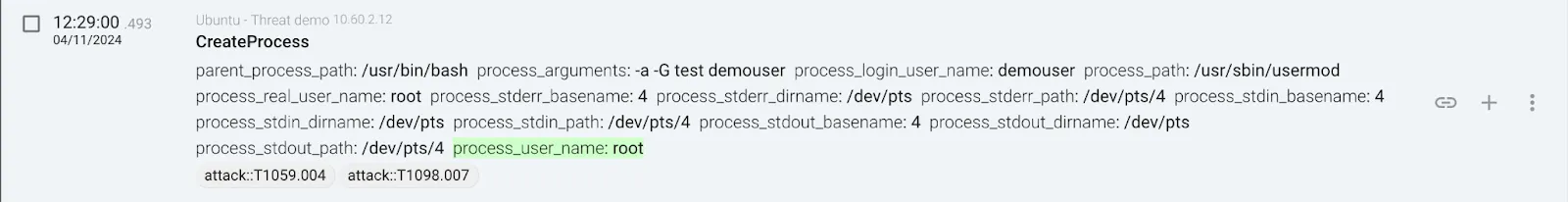
Adding a Linux user to a group (tagging the event as T1098.007)
And the technique as it is shown in the Enterprise Matrix
Adding a Windows user account to the “Administrators” and “Remote Desktop Users” group
As the MITRE ATT&CK framework continues to add subtechniques and keep pace with attackers, staying informed on updates like v16 is crucial for cybersecurity teams. By incorporating the latest techniques, such as those targeting lateral movement and persistence, organizations can better anticipate and defend against sophisticated attacks. Get in touch if you want to see how our platform uses MITRE ATT&CK to bring our clients the best threat detection and remediation via deception technology around.