WHITEPAPER
Is Your Organization Ready for DORA?
Find out how threat intelligence powered by deception can get you there.
Download the whitepaper
With the EU’s Digital Operational Resilience Act (DORA) taking effect in January 2025, financial organizations face a critical milestone.
DORA demands a unified, proactive approach to managing ICT risk, ensuring rapid recovery, and maintaining business continuity under ever-evolving cyber threats. Download the whitepaper Is Your Organization Ready for DORA? How Threat Intelligence Powered by Deception Technology Can Strengthen Operational Resilience now to find out how modern deception technology can help you navigate DORA’s complexities, enhance operational resilience, and achieve compliance before the deadline.
Download now and gain insights that can help you strengthen your defenses, meet regulatory requirements, and protect your reputation and bottom line.

Get it now.
Fill out this form to download the whitepaper and find out how deception addresses DORA’s key requirements.
If you don’t have DORA covered, the cost to your financial organization could be huge—up to 2% of annual turnover.
DORA is meant to address resilience in ICT systems and outlines critical operational resilience strategies—and incorporating deception technology into your security stack addresses compliance.
This whitepaper explains how deception technology fills the gaps in your organization’s compliance. By integrating deception into your DORA strategy, you can proactively detect and thwart advanced threats, ensuring both regulatory compliance and stronger security.
What you will learn

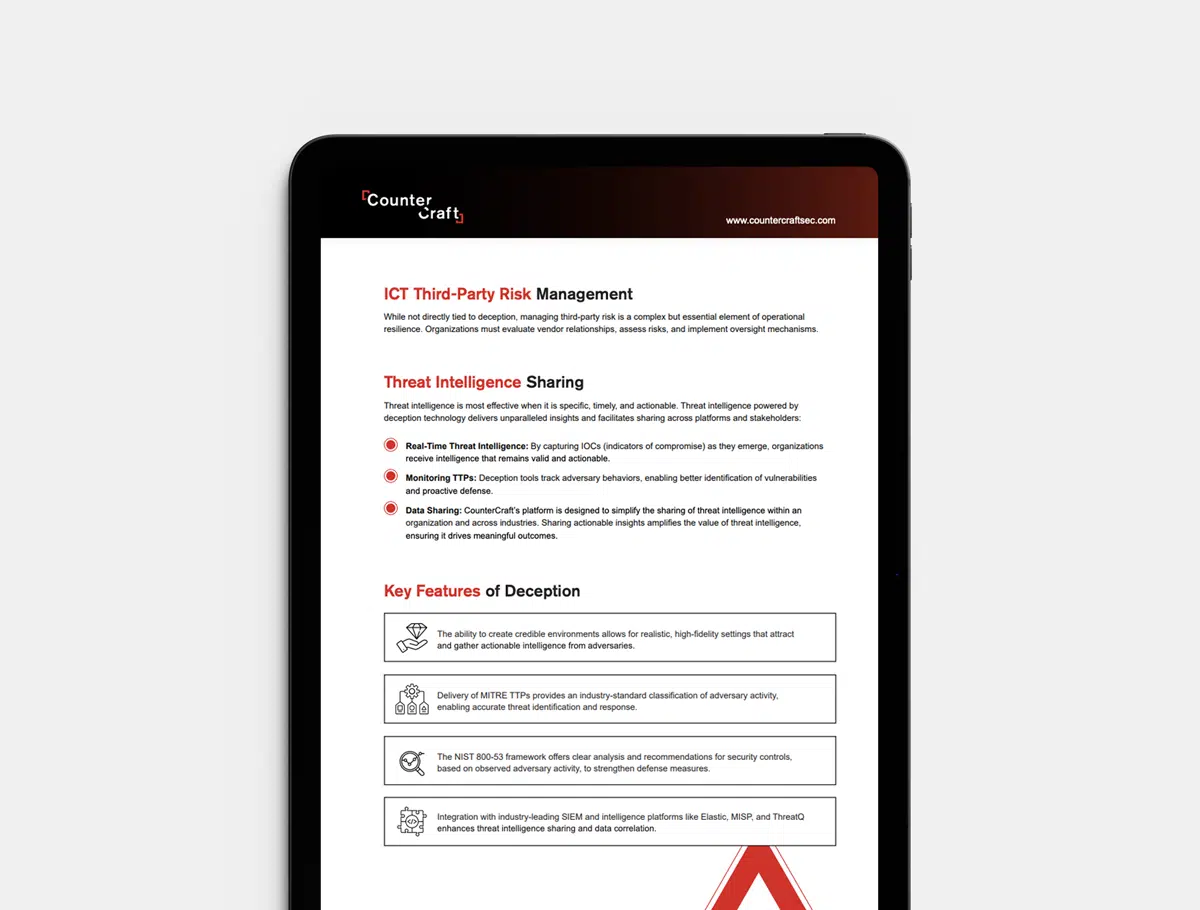
The Key Requirements of DORA
Delve into the key requirements of the Digital Operational Resilience Act and understand how this first-of-its-kind regulation sets a new standard for ICT risk management and incident reporting. Learn why DORA’s unified framework is a game-changer for the financial sector and how it applies to your organization, including critical ICT third-party service providers.

The Power of Deception Technology
Discover how cutting-edge deception solutions go beyond traditional security measures. Learn how these tools help detect threats early, deflect adversaries away from critical assets, and gather invaluable threat intelligence—all aligning with DORA’s pillars of resilience, compliance, and recovery.

How Deception Maps to DORA Requirements
Explore a step-by-step mapping of DORA’s main pillars—ICT risk management, incident reporting, operational resilience testing, third-party risk management, and threat intelligence sharing—to deception technology features. Understand the practical methods that transform regulatory obligations into actionable, high-value security outcomes.

The Fastest Route to Compliance and Operational Maturity
Gain insights on how to integrate deception technology into your existing security frameworks and processes, reducing complexity and cost. Learn about effective strategies for refining risk assessments, supporting executive-level accountability, and continuously improving threat response—all essential for meeting DORA requirements and enhancing overall organizational resilience.
Get the whitepaper.
Fill out this form to download the whitepaper and find out how deception addresses DORA’s key requirements.