AI has transformed traditional cybersecurity threats like ransomware, phishing, and supply chain attacks, making them faster, more precise, and more scalable. These familiar threats are now amplified by AI’s ability to analyze, adapt, and optimize attack strategies in real-time.
AI-enhanced ransomware, for instance, encrypts critical data while evading detection, prolonging recovery efforts. In phishing, AI generates highly personalized messages that mimic a victim’s communication style, increasing success rates. Supply chain attacks, meanwhile, leverage AI to identify weak points in vendor ecosystems, compromising entire networks with minimal effort.
Real world examples of persistent traditional threats enhanced by AI
The impact of AI on cyber threats isn’t theoretical—it’s already happening. Attackers are leveraging AI to refine and scale long-standing techniques, making them more effective and harder to detect. The following real-world cases demonstrate how AI is amplifying traditional threats, from phishing campaigns that mimic human behavior to ransomware that adapts on the fly and supply chain attacks that pinpoint vulnerabilities with unprecedented speed.
- AI-Enhanced Phishing: Attackers used AI to craft tailored phishing emails, successfully compromising hundreds of high-ranking corporate accounts.
- Ransomware Adaptation: AI-enabled ransomware dynamically adjusted its encryption and lateral movements methods to evade detection software.
- Supply Chain Exploits: An AI tool identified and exploited a vulnerable vendor API, leading to widespread data breaches across downstream organizations.
Persistent traditional threats enhanced by AI: The bottom line
The integration of AI into traditional threats presents a formidable challenge. Attackers no longer rely on brute force but leverage AI’s capabilities to exploit weaknesses with precision. For defenders, this requires a dual approach: countering AI-driven enhancements while maintaining vigilance against traditional methods.
Your AI cybersecurity defense against persistent traditional threats enhanced by AI
Though attackers use AI to enhance their techniques and avoid traditional security measures, deception systems remain effective because they operate in real time, detecting unauthorized access as it happens. To counter the threat of AI-enhanced APTs, the defender can enhance them with AI.
By using AI and deception technology, defenders can dynamically adjust deception scenarios, generate alerts upon intrusion, and provide real-time intelligence on attack tactics. This ensures that even if an adversary bypasses conventional security measures, their activities within the network can still be detected and analyzed.
AI-enhanced deception: What it looks like
Defensive AI is particularly valuable in deception campaigns, as it enables the creation of dynamic, adaptive environments that respond in real time to attacker behavior. Instead of static environments, AI-generated deception continuously adapts and changes, making it significantly harder for attackers to distinguish between a real system and a fabricated one. By generating credible, changing content, AI-enhanced deception technology misleads and delays.
This approach is particularly relevant in ransomware and other AI-augmented attack scenarios, where attackers are improving their ability to craft sophisticated exploits. If they use AI to optimize phishing, reconnaissance, or intrusion tactics, defenders can counteract by using AI to improve deception credibility—effectively turning the attackers’ own advancements against them.
AI-powered Deception: Fighting AI-driven attacks with AI-enhanced defense
AI enables adversaries to automate reconnaissance, refine phishing lures, evade detection, and scale their attacks faster than ever before. Our ransomware deception campaign is designed to detect and neutralize ransomware threats at multiple points along the kill chain—from initial reconnaissance to lateral movement—using a combination of proactive defense, real-time threat intelligence, and AI-generated deception. This AI-enhanced Ransomware Defense Campaign approach leverages AI-powered deception—using artificial intelligence not just to detect threats, but to actively mislead, contain, and study attackers in real time.
AI-enhanced Ransomware Defense
By deploying dynamic, AI-generated decoy environments, we can create a proactive defense that not only detects but also misleads and neutralizes attackers in real time, all while safeguarding real assets with no added effort from your threat intelligence team.
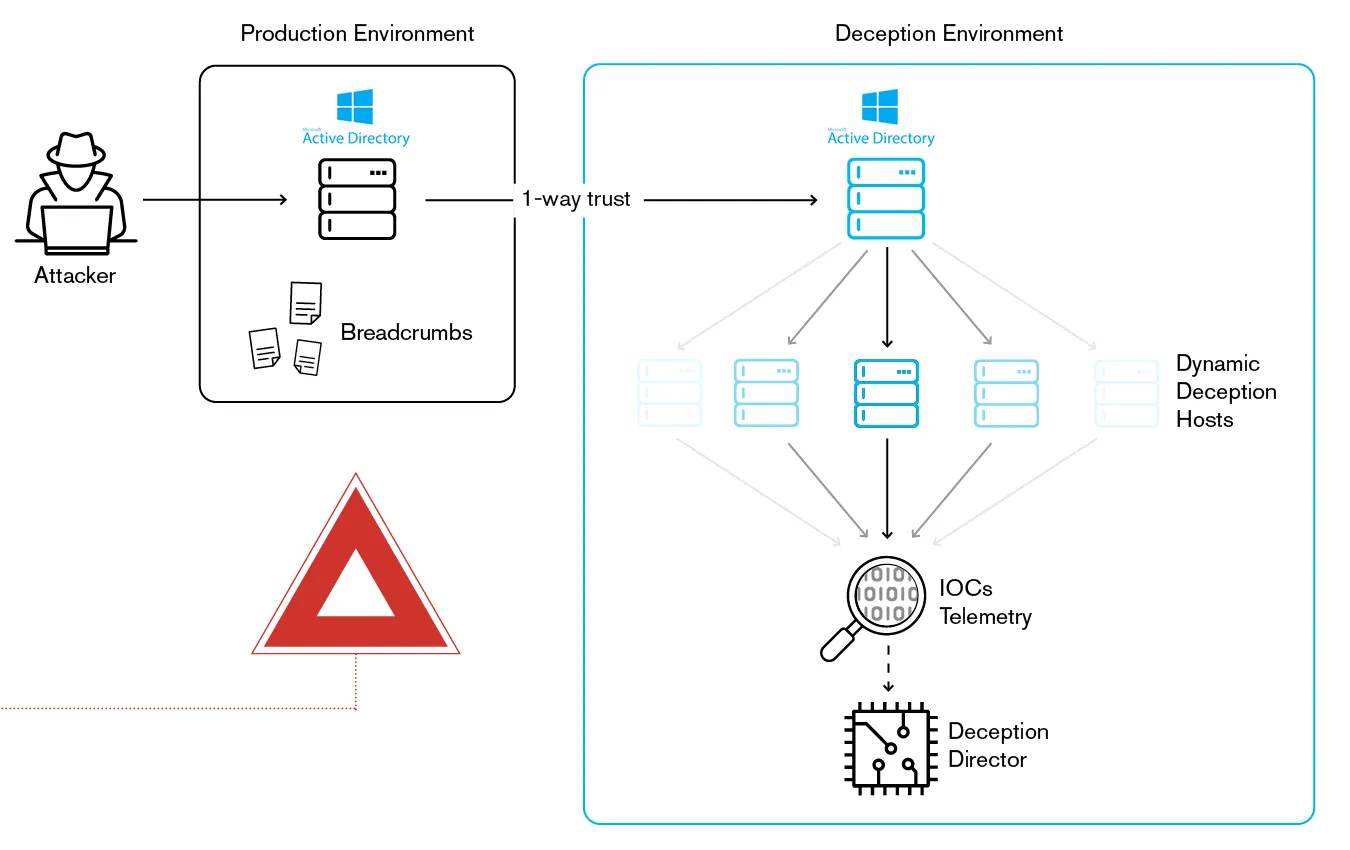
The first step in this campaign involves deploying AI-enhanced deception buffer zones. In this campaign dynamic, AI-generated decoy environments are designed to mimic real networks and assets (like Active Directory servers or backup systems), constantly adapting in real time to create more believable and effective traps for attackers. Unlike traditional systems, which can be quickly bypassed, the dynamic decoys continuously evolve, ensuring that attackers remain engaged in a virtual space designed to waste their time and expose their tactics. Even when attackers attempt techniques like prompt injection, lateral movement, or reconnaissance, they are confined to artificial environments that prevent them from reaching their intended targets.
As attackers engage with the decoy systems, the AI adjusts the deception elements based on their behavior. For example, if an attacker probes a decoy system or attempts lateral movement, the AI responds by creating new layers of plausible infrastructure, feeding the attacker misleading data that further diverts their efforts. At the same time, the system triggers alerts to notify defenders, ensuring that any activity in the deception environment is closely monitored and responded to promptly.
The final and key piece of this campaign is the AI-enhanced collection of threat intelligence. Every action an attacker takes within the deception environment is logged and analyzed, providing valuable insights into their tactics, techniques, and procedures (TTPs). By processing this information in real time, the AI can identify patterns in attacker behavior and refine detection models accordingly. This enables defenders to predict and preemptively counter future attacks, strengthening their defense mechanisms and ensuring that they are always one step ahead.
The future: AI vs. AI in cybersecurity
The new normal will be a battleground where AI-enhanced attackers face AI-driven defenses. While adversaries use AI to improve efficiency and stealth, defenders can become highly effective by using AI to create more realistic, evolving deception environments that neutralize threats in real time. By continuously adapting, poisoning attacker models, and leveraging deception to its fullest potential, AI-powered defenses can effectively turn the tables—using the attackers’ own advancements against them.
This approach ensures that defenders stay ahead in the AI arms race, making it increasingly difficult for attackers to trust the information they gather or the systems they attempt to compromise. The result is a cyber environment where deception is no longer just a passive defense but an active, AI-driven countermeasure that disrupts attacks before they can cause harm.
Stay ahead in the battle against adversarial AI. Get a technical briefing today.
Find out more
To learn more about how defenders can use AI to face AI-enhanced threats, get in touch with one of our experts.
If you’d like to read about more of the latest AI threats to cybersecurity, download our ebook,From Poisoned Data to Secure Systems: The Antidote to Navigating AI Threats today.