While most of us are sitting down to enjoy a holiday meal around a table with family and friends, threat actors are putting carefully designed holiday ransomware attacks into motion. In fact, security researchers discovered a 30% increase in the average number of attempted ransomware attacks globally over the holiday season in every consecutive year from 2018 compared to the monthly average. The retail industry and e-commerce sites are the major targets for this type of attack.
Ransomware has been around for a long time, making its first appearance back in 1989. Today, ransomware actors use techniques that are more and more sophisticated and targeted. So much so that Gartner says the threat of new ransomware models is the top emerging risk facing organizations.
As a matter of fact, ransomware is one of the most common threats facing organizations globally across all sectors, and incidents of ransomware attacks continue to rise. Ransomware attacks cost the US $159.4bn in downtime alone in 2021.
Download our data sheet on how to improve retail cybersecurity here.
Ransomware Attacks on the Rise Over the Holidays
Holiday season is the time of the year when people disconnect from their work duties and enjoy a well deserved rest, but for cybercriminals it’s time to attack. In the United States, The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have observed an increase in highly impactful ransomware attacks occurring on holidays and weekends. The shortage of personnel on those dates means companies have less manpower to protect their systems and respond to incidents.
The retail industry is especially vulnerable at this time of year. Consumers spend billions of dollars online during the holiday shopping season, typically around $10 billion dollars on Black Friday alone. In recent years, SonicWall Capture Labs threat researchers recorded a double-digit malware spike (63 percent) in the U.S. between the eight-day holiday shopping window from Thanksgiving to early December.

On December 11, 2021, Ultimate Kronos Group (UKG), a multinational that provides HR, payroll, and workforce management technology and services became aware of unusual activity impacting their Kronos Private Cloud solution. It turned out to be a ransomware attack that took down their payroll systems affecting 2,000 of their clients, which include Tesla, PepsiCo, Whole Foods, and the New York Metropolitan Transit. Kronos had to scramble to create temporary manual workarounds, and many employees missed paychecks over the holidays. The attack also affected the many businesses that relied on Kronos software.
Europe’s largest consumer electronics retailer MediaMarkt also suffered a ransomware attack over the holidays last year, in an attack with an initial ransom demand of $240 million. Hive Ransomware operation was behind the attack, which made its first appearance back in June 2021. They operate through malware-laced phishing campaigns to gain access to a network. Once they reach that, threat actors start looking for unencrypted files, following the lateral movement procedure, to be used in extortion demands.
This spike in major incidents during the holiday season has caught the FBI and CISA’s attention, causing them to strongly urge all entities to examine their current cybersecurity posture and implement best practices and mitigations to manage the risk posed by cyber threats.
Find out how organizations have stopped ransomware in its tracks with this data sheet.
Despite these recommendations, the current situation is not encouraging, with 90% of cybersecurity professionals concerned about holiday/weekend attacks. And it’s no wonder— nearly a quarter (24%) companies do not have a specific plan in place to address the increased risk on holidays and weekends, even if they had been attacked before. And the pressure is on—holiday ransomware attacks take longer to respond to and recover from, resulting in more loss of revenue.
Protecting Against Ransomware in the Retail Industry
Leaders in industry security recommend various measures to improve retail industry cybersecurity, including this common Top 5:
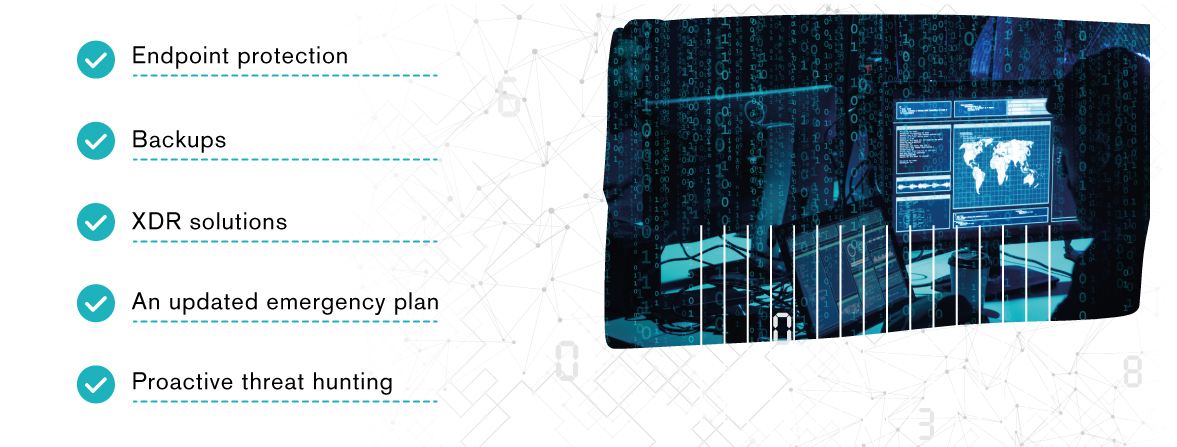
The first four measures are obvious e-commerce cybersecurity best practices and even out-of-the-box solutions. The fifth security measure, however, is both more interesting and more effective, when done correctly: proactive threat hunting allows organizations to take back the advantage from the adversary, putting the threat actor on the defensive. Proactively hunting for threats means organizations can identify and stop adversaries before they can execute attacks.
Cyber deception is an excellent method to use for proactive threat hunting. With deception, you can find attackers and observe their movements before they have even entered your network. CounterCraft The Platform can detect ransomware activity in its early stages and deflect attacks away from the infrastructure of the organization by deploying a deception buffer zone. The service will deliver real time intelligence that you can then use to protect your network.

Top-quality threat intel is at your fingertips, and here is how it works:
- Deploy deception – buffer zones with zero workload and effort to your threat intel team.
- Detect threats – detect when ransomware threat actors are conducting reconnaissance externally and/or moving laterally internally in real time.
- Collect intelligence – collect real-time, focused and actionable intel about how ransomware threat actors are trying to compromise internal and external Windows servers, with zero increase to analyst workload.
- Proactively protect – investigate Incidents rapidly and reconfigure enterprise systems in real time.
See it for yourself
Protect your retail and e-commerce organization this holiday season. Find out how CounterCraft’s The Platform generates actionable, adversary-generated threat intelligence powered by deception technology. These campaigns require no training and zero ramp-up time.
Spend 20 minutes with us to see why the world’s most sophisticated organizations, including the U.S. goverment, are using our deception technology platform for active cyber defense, freeing up resources and staying ahead of threat actors.
Source:
1https://www.securitymagazine.com/articles/91425-malware-spike-during-black-friday-and-cyber-monday
2https://hitechglitz.com/cybercriminals-work-around-the-clock-and-so-should-your-cybersecurity/
3https://www.cybereason.com/blog/research/cybereason-research-finds-organizations-unprepared-for-ransomware-attacks-on-weekends-and-holidays
4https://cioafrica.co/why-many-ransomware-attacks-target-retail-industry/
