Ransomware is one of the most intractable — and common — threats facing organizations globally across all sectors, and incidents of ransomware attacks continue to rise. Meanwhile, ransomware threat actors are adjusting their attack model to adapt to the improvements that organizations are making to recover from these attacks.
There are multiple articles describing the ransomware history, starting from AIDS, the first known ransomware sample, to the newest families with advances that make them almost impossible to stop.
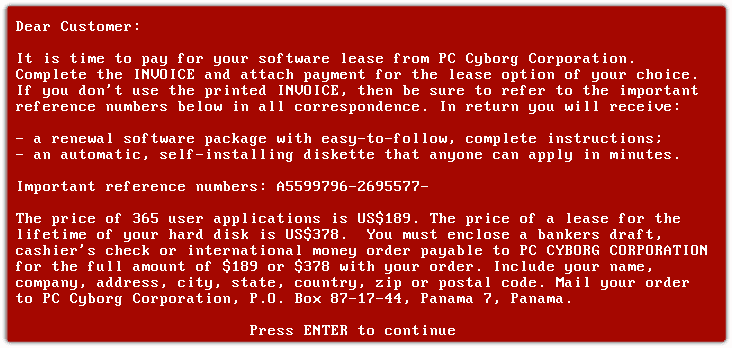
All these ransomware families have focused, sooner or later, on the following features and techniques in their life cycle:
- Find initial infection vector
- Infect as many devices as possible from the initial infection
- Encrypt important files (quickly, hard to decrypt, as many as possible, and exfiltrate infection encryption key)
- Receive the payments without being tracked by Law Enforcement
- Support infected users – decrypting their devices
In this blog post we are going to focus on steps 2 and 3, and how we can use different methods to detect them.

Infect as Many Devices as Possible
When ransomware (and worms in general) started back in the 80’s, the main method of infection was the use and distribution of infected diskettes. That was the ‘lateral movement’ technique for that period of time.
Once ransomware started to invade internal enterprise networks, attackers changed their techniques to use the standard Windows and Linux remote tools and services used by System Administrators, making detection harder. Tools and services like psexec, WinRM, WMI, SSH, etc. are continuously abused for ransomware distribution.
At the beginning, ransomware relied on aggressive scanning of the entire network, looking for shared folders or other devices to infect, but now they are smarter (and less noisy) and just try to infect systems they know they exist (for instance, by looking at the ARP table).
Encrypt Important Files
The first action that any current ransomware family in an infected device is to try to encrypt as many important files as possible.
In Windows systems, there are a number of different tricks that malware authors use for improving their encryption mechanisms. The following are some examples:
- Use of Windows I/O Completion Ports: for multi-threaded asynchronous I/O (for example Conti uses 32 threads for encryption)
- Persistence: not really of use once all files have been encrypted, but rather as an extra mechanism in case the encryption fails.
- Processes and services shutdown: stop services that could interfere with the encryption process: backup services, security products, etc.
- Delete shadow copies: avoid any possible local restore.
- File encryption.
- Use Windows Restart Manager: to be able to encrypt files that are used by other applications.
- Change internet settings: to be able to bypass proxies and other network settings.

Active Defense
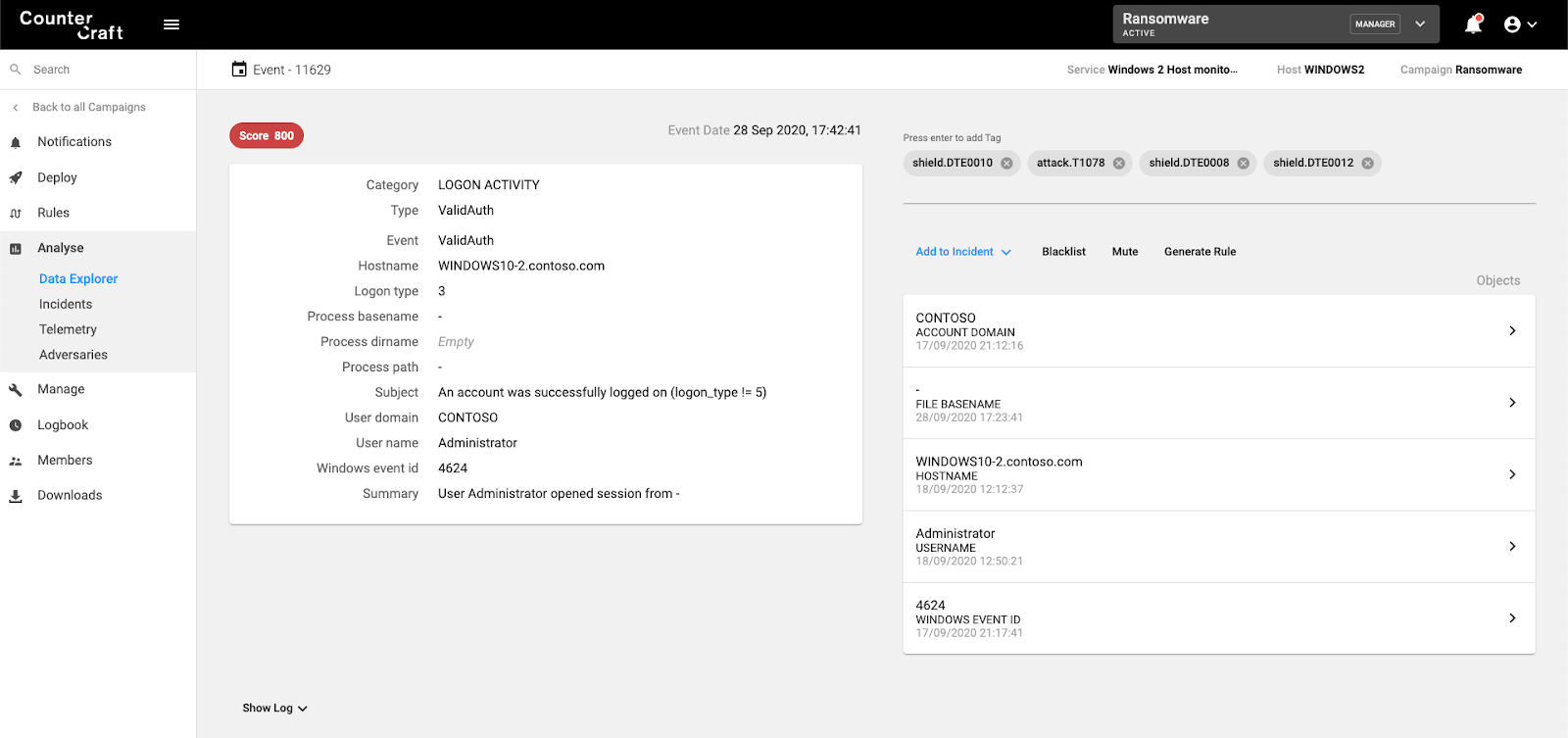
How can we be more active in our security defenses against ransomware? Fortunately the folks at MITRE recently created the Shield framework, which is very useful for defining the techniques we can use against different types of security incidents.
MITRE Shield is an Active Defense knowledge base that was developed from their first-hand experience with defending MITRE’s corporate network. Many of the techniques found in MITRE Shield are fundamental security techniques — the cornerstones upon which good active defense is built. These techniques make MITRE Shield accessible and actionable to organizations regardless of size or sophistication.
In our ransomware scenario, we are going to use a number of Shield techniques, that will help to:
- Detect the activity and notify it immediately
- Obtain TTPs and IOCs
- Engage with the attackers
- Act on the information (integration with SOARs and SIEMs)
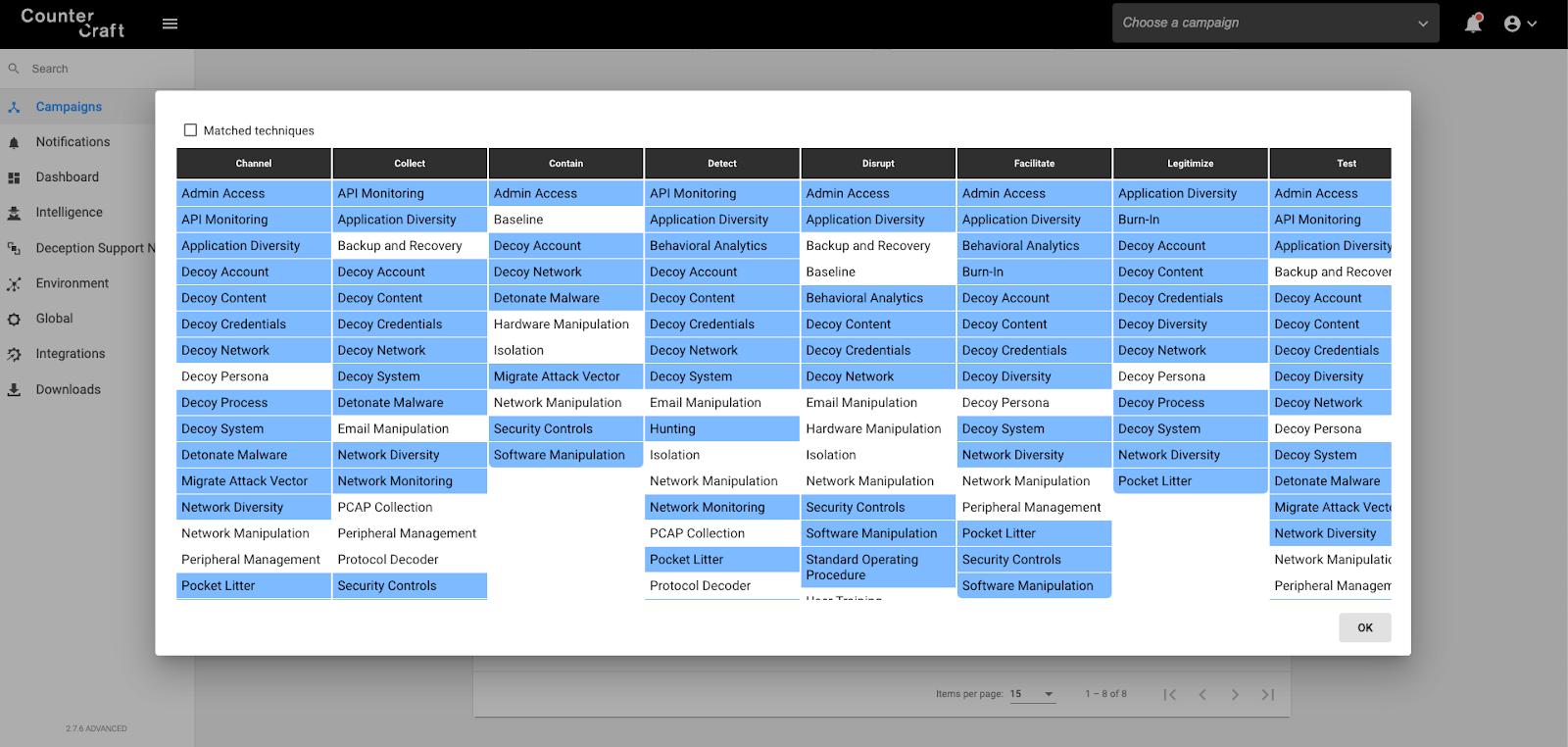
As you can see in the above picture, to achieve our original four goals we are going to use different techniques like Decoy System, API Monitoring, etc.

Using Threat Intelligence Powered by Deception (DTE001) to Lure the Attackers Toward Our Decoy Systems (DTE0017)
As a defender, you can create several types of decoy content/breadcrumbs in order to lure the attackers toward the decoy systems/deception hosts. We know than ransomware actors usually take control of the entire network before releasing their ransomware, so we can try to attract them by using breadcrumbs such as:
Passive Breadcrumbs
- Domain machines with tempting names (BACKUPSERVER, etc.). We will use these as Decoy Systems.
- Real domain admin users with attractive description fields (example: \10.10.10.1\DomainDocs; 10.10.10.1 will be one of our Decoy Systems).
- StartUp scripts from GPOs that include credentials in SYSVOL pointing to our Decoy Systems.

Active Breadcrumbs
- Mapping a Decoy System shared folder on all endpoints and servers, or just in critical servers (the ransomware will try to encrypt them).
- Activating shared folders on our Decoy Systems (ransomware will try to find writable shares in the network).
- Deploying Windows Servers with RDP connected to the Internet (in an isolated network with other Windows machines). This could be the initial infection vector.


Ransomware Techniques
Now that we have deployed our breadcrumbs, we can analyze when an infection occurs in one of our Decoy Systems. Let’s have a look at the most common techniques that can be seen in a ransomware infection.
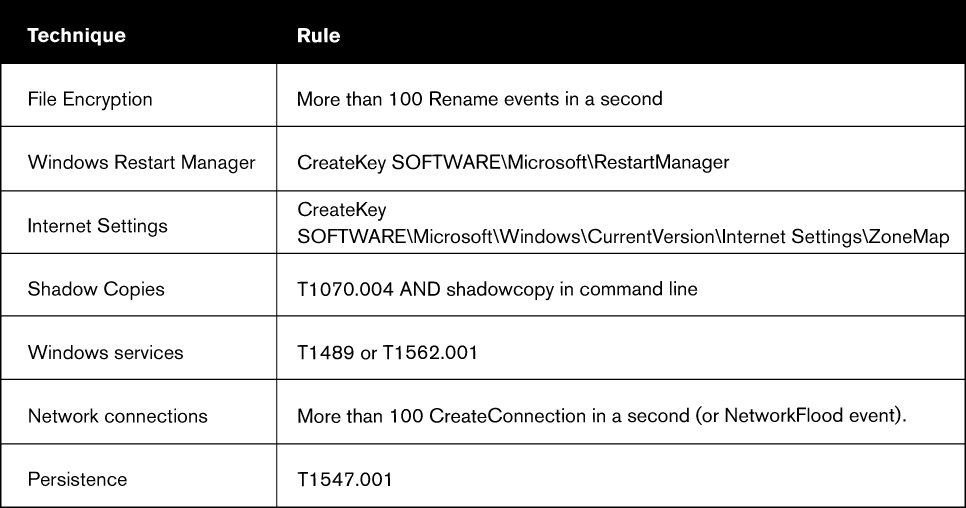
File Encryption
The majority of ransomware families rename the files after encrypting them in memory. They usually spawn a number of threads to accelerate the encryption process.
Detection rule: More than 100 rename events in a second.
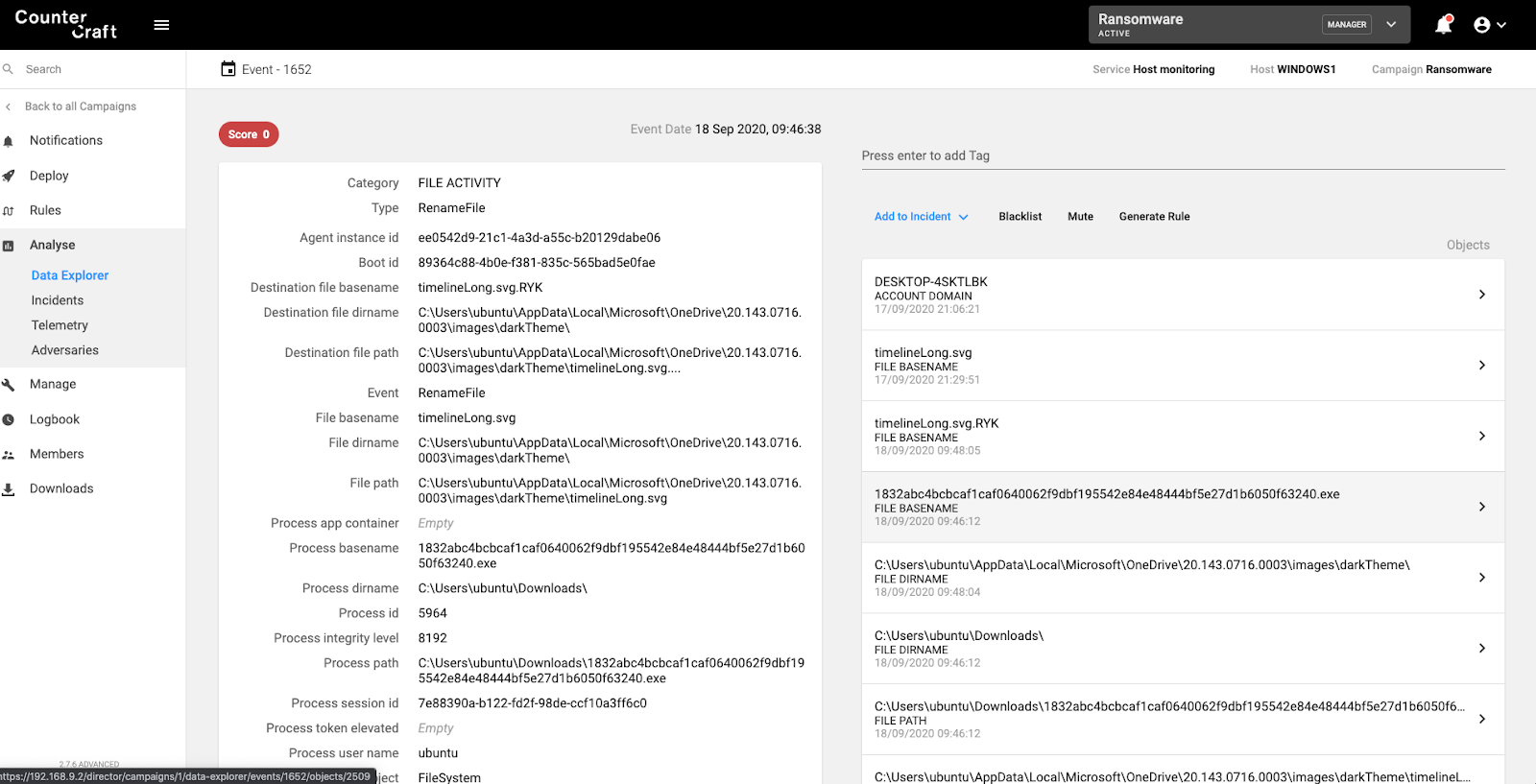
Screenshot of the CounterCraft platform identifying multiple rename events, indicative of ransomware.

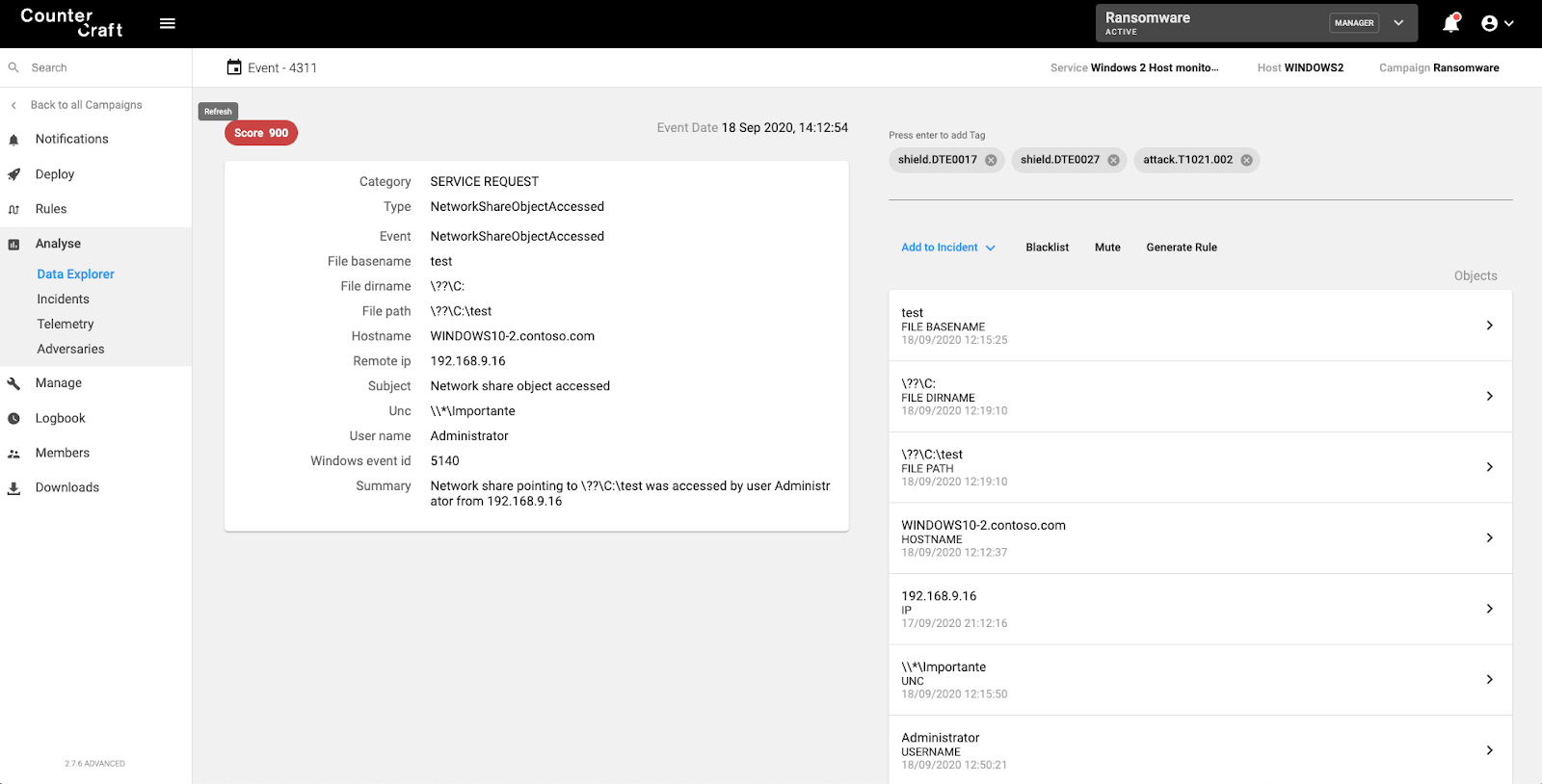
Shadow Copy Deletion
Attempts to delete Shadow copies is detected and mapped to ATT&CK techniques T1059.003 – Windows Command Shell – and T1070.004 – File Deletion
Detection rule: T1070.004 AND parameter ‘shadowcopy’ in command line.
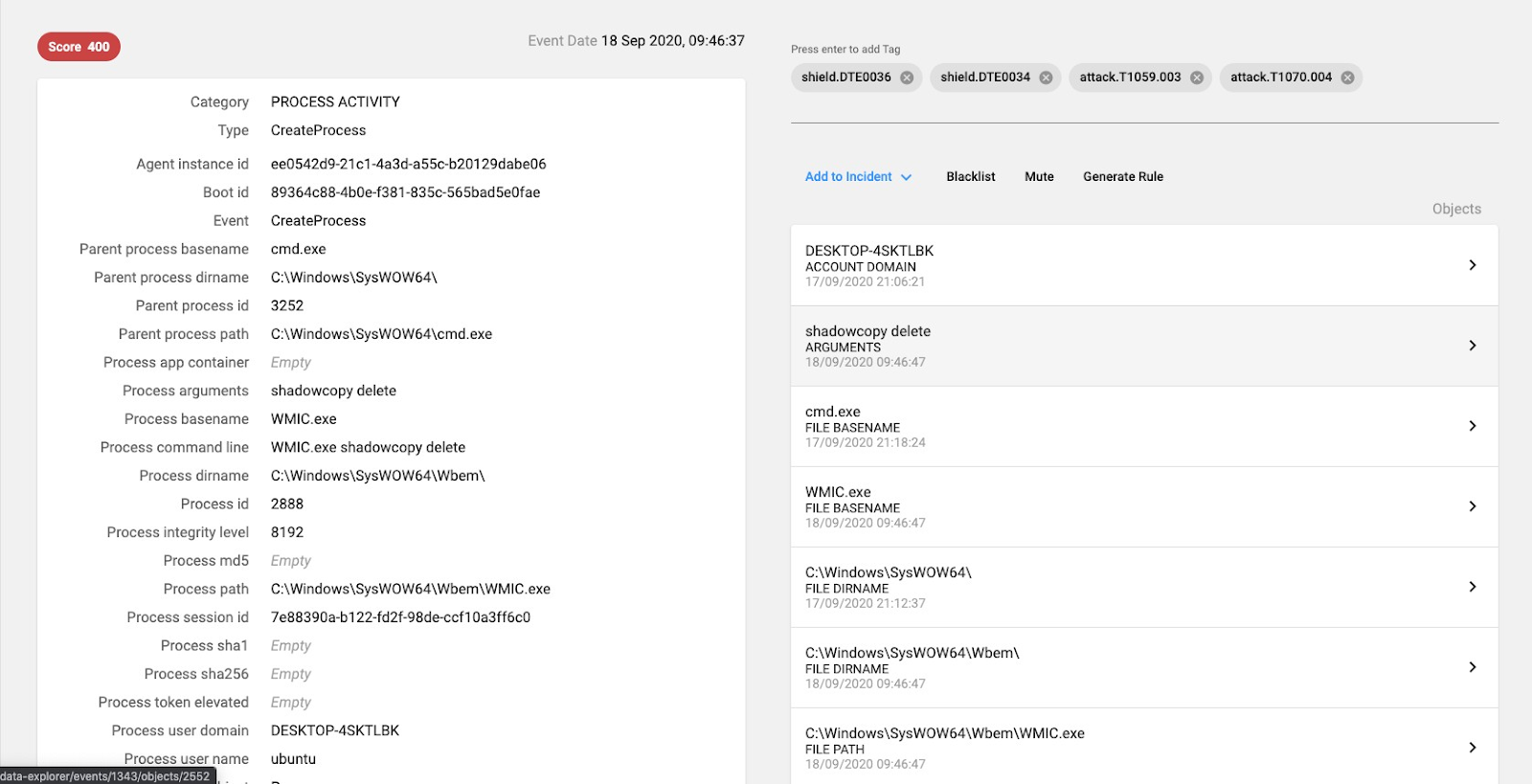
Screenshot of the CounterCraft platform detecting shadowcopy deletion.

Persistence
Attempts to create Windows persistence. T1547.001 – Boot or Logon Autostart Execution
Detection rule: T1547.001
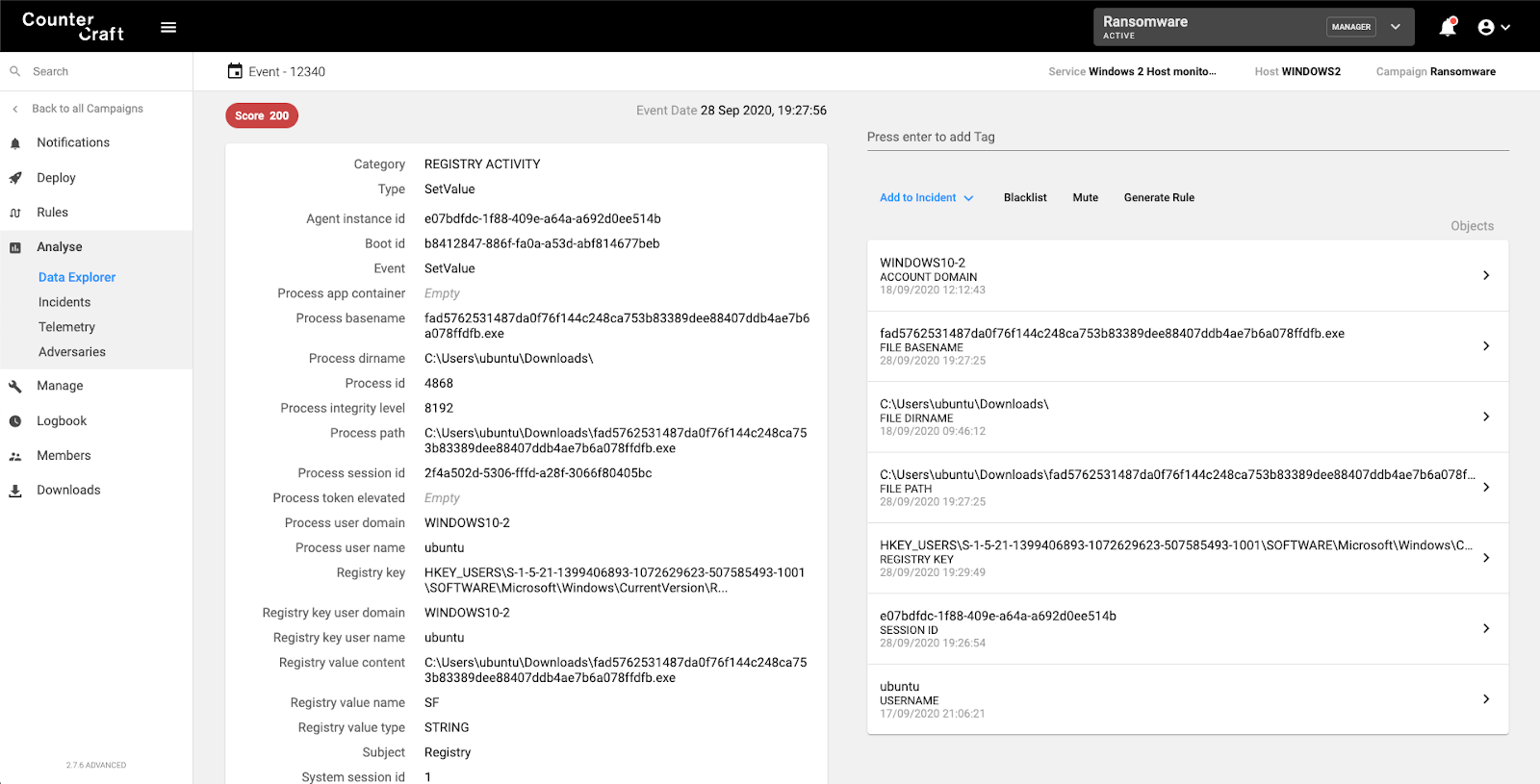
Screenshot of the CounterCraft platform detecting registry manipulation

Network Connections
Attempts to create multiple network connections per second
Detection rule: More than 100 CreateConnection / second (or NetworkFlood event)
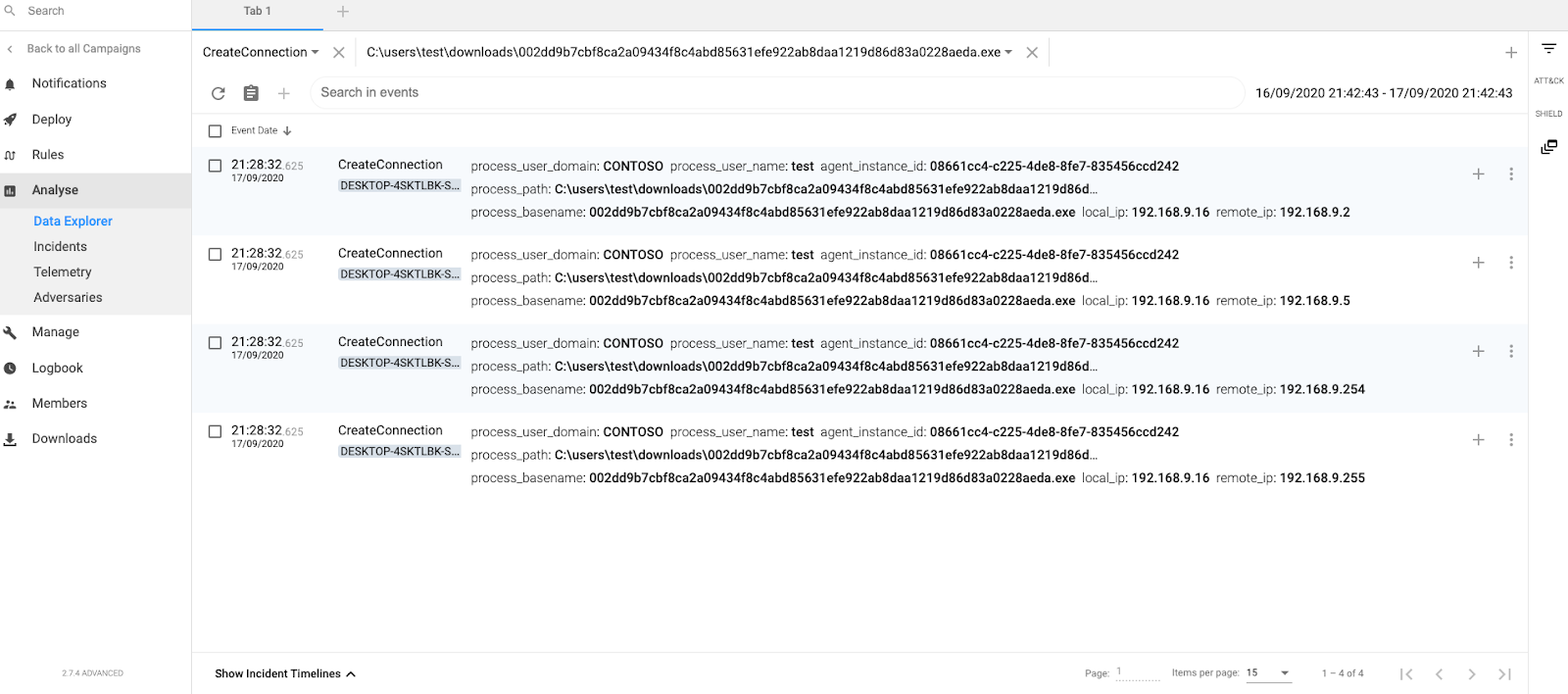
Screenshot of the CounterCraft platform detecting multiple network connections.

Shutdown Services
Attempts to stop services and mapped to ATT&CK techniques:
Detection rule: T1489 OR sub-technique T1562.001
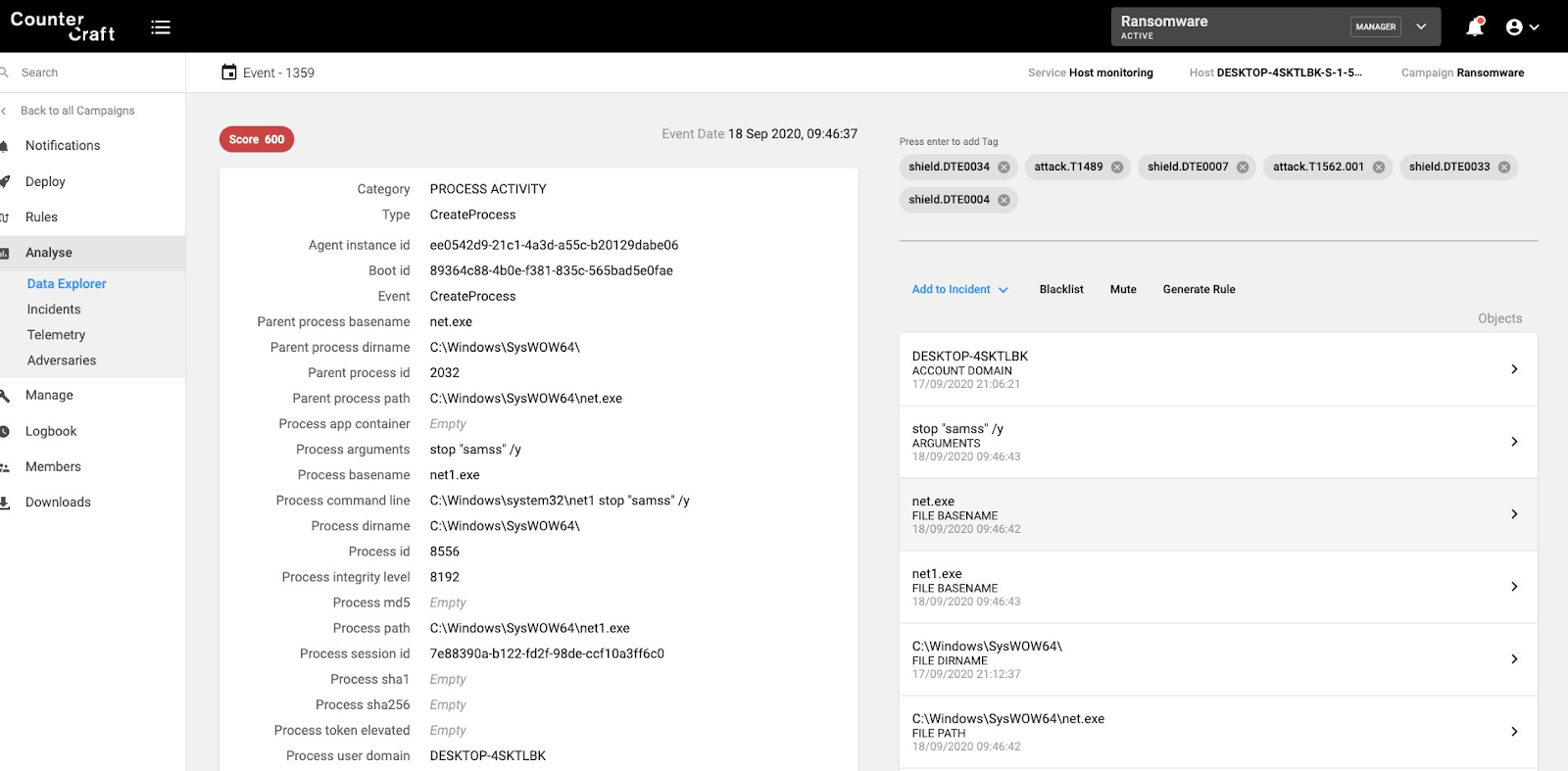
Screenshot of the CounterCraft platform detecting service shutdown.

Windows Restart Manager
Some ransomware families use the Windows Restart Manager to ensure that all files are encrypted.
Detection rule: Access to SOFTWARE\Microsoft\RestartManager
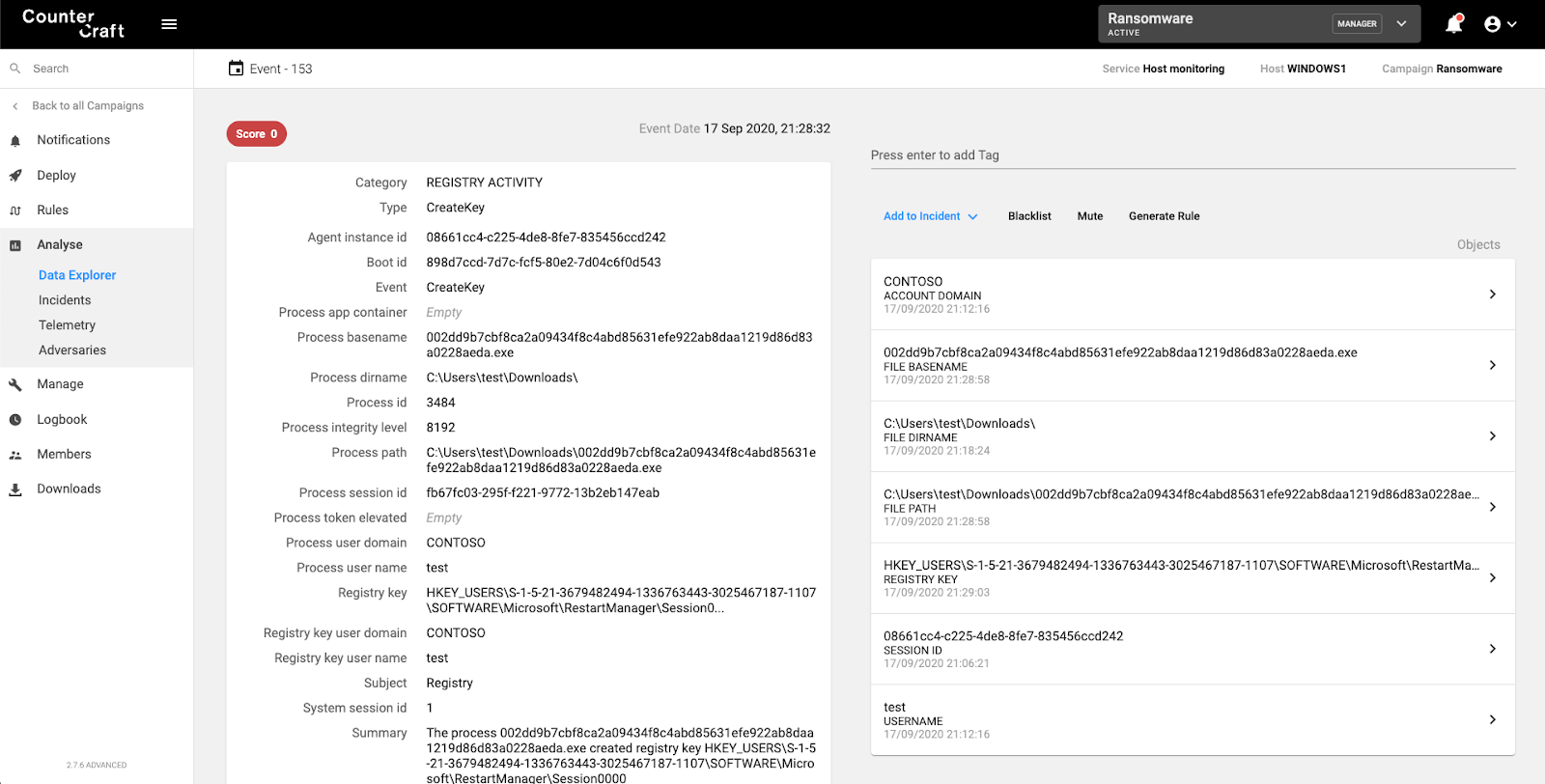
Screenshot of the CounterCraft platform detecting RestartManager being accessed.

Internet Settings
Some ransomware families change the Internet Settings to bypass proxies.
Detection rule: Access to SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
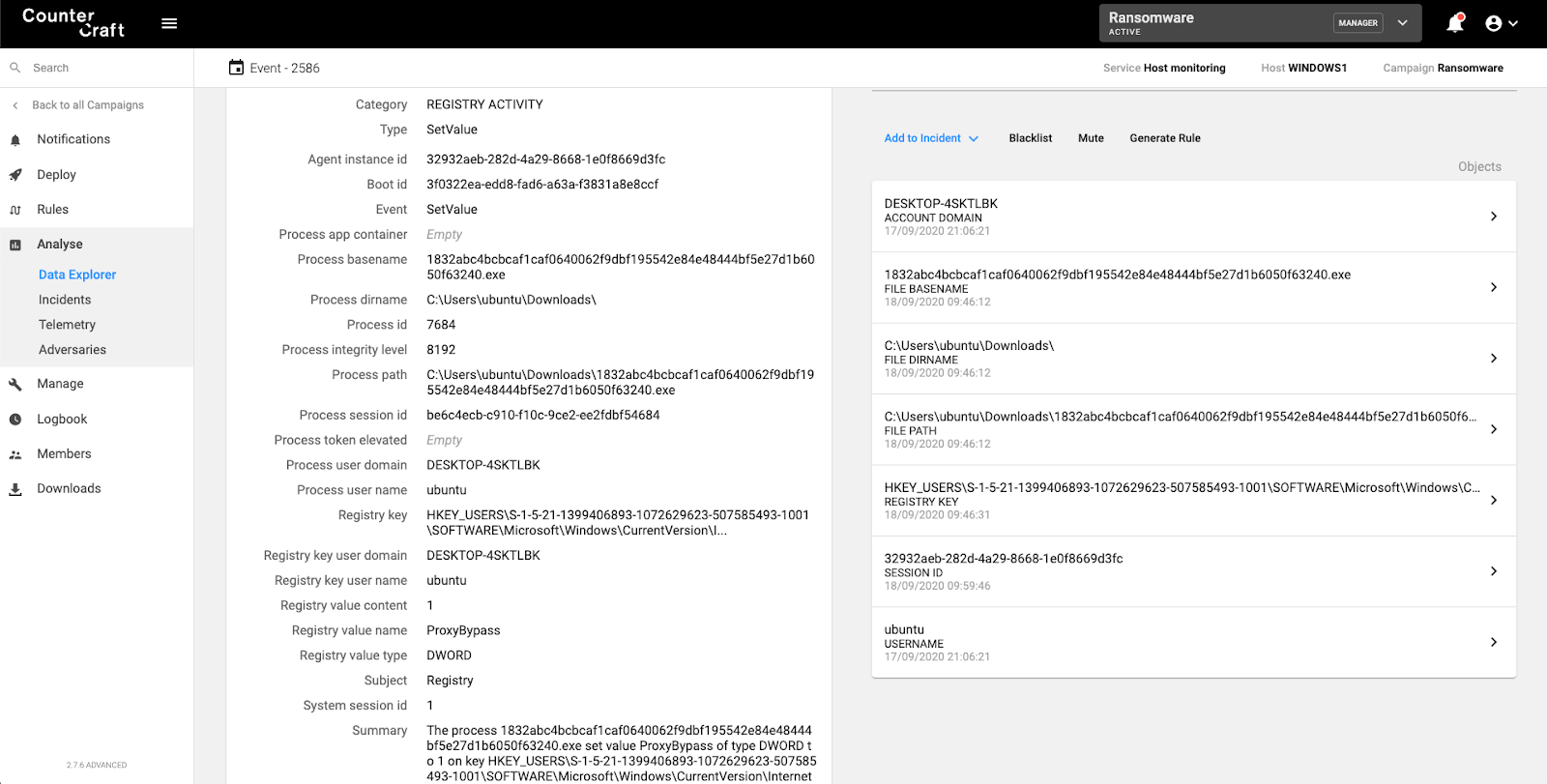
Screenshot of the CounterCraft platform detecting use of ZoneMap to bypass proxies.

Common Lateral Movement Ransomware Techniques
Although many of the following techniques are not specifically used by ransomware samples, they are actively being used by actors in order to compromise internal networks. They can then just release their ransomware and wait for the results.
In our scenario, WINDOWS1 (192.168.9.16) is the source of the connection, while WINDOWS2 (192.168.9.17) is the destination device. Both machines belong to the CONTOSO.COM windows domain (192.168.9.5 is the DC, running Windows 2019 server).
Below you can see a list of common lateral movement techniques and how CounterCraft´s platform detects them and collects intel on how they are working.
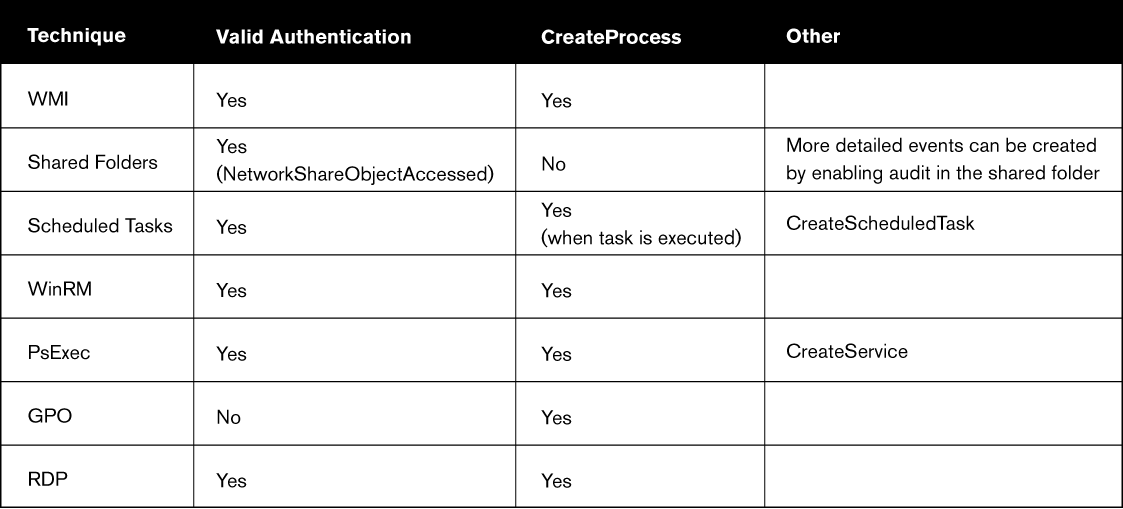
- WMI
- WinRM
- PS Exec
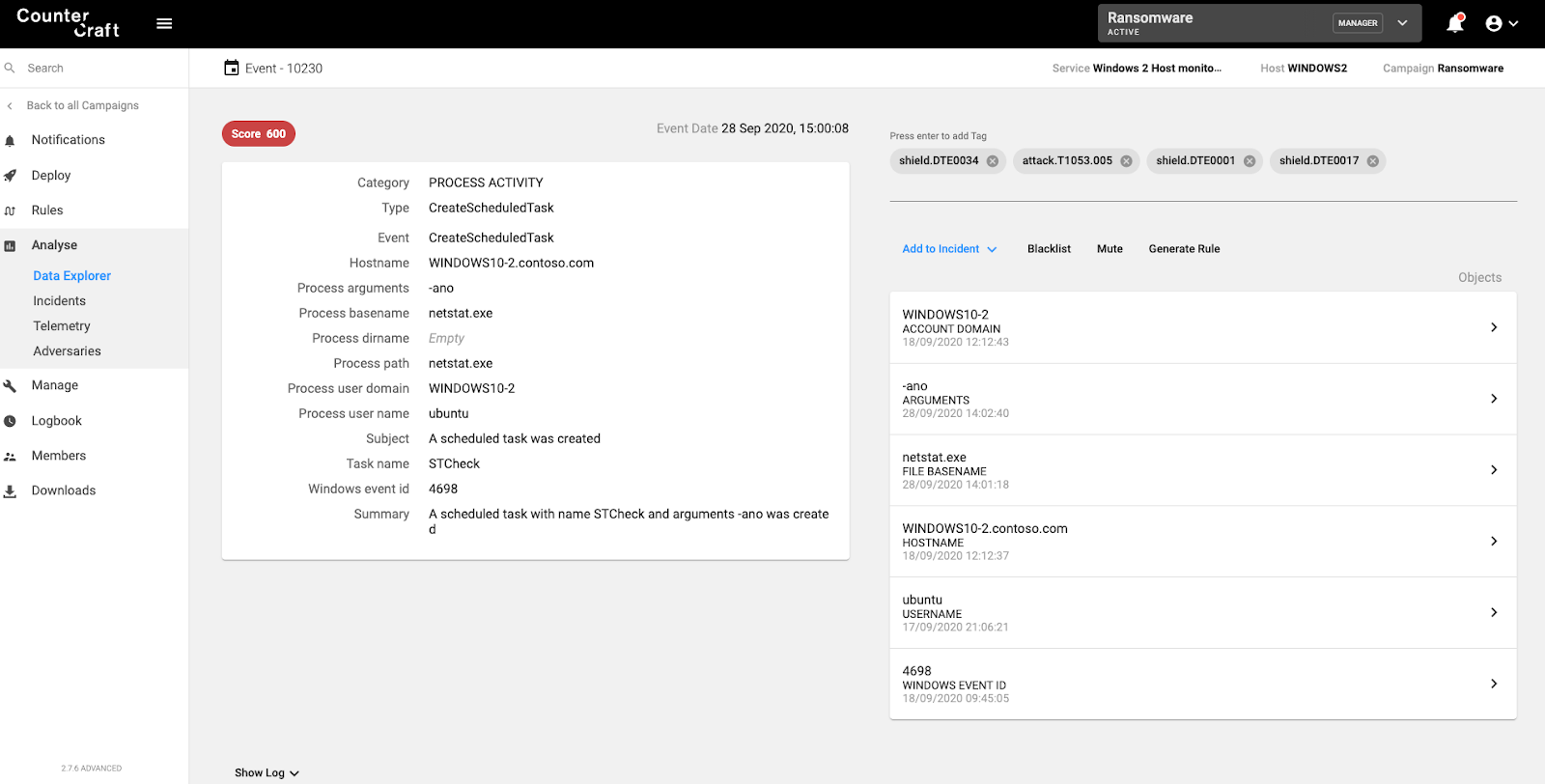
- Remote Scheduled Tasks
- Shared Folders
- RDP
- GPO Startup Boot

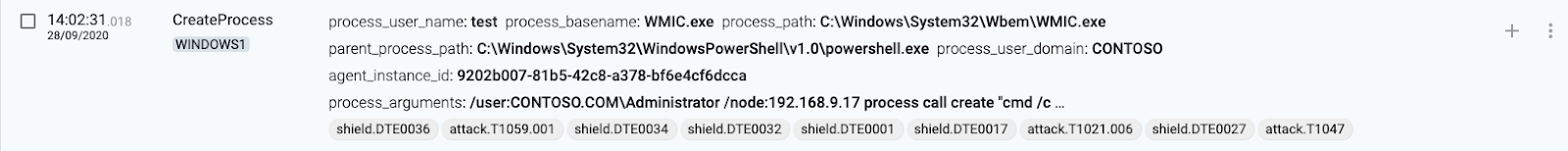
WMI
1 WINDOWS1(source) executes WMIC
2 WINDOWS1(source) connects to WINDOWS2 using svchost.exe
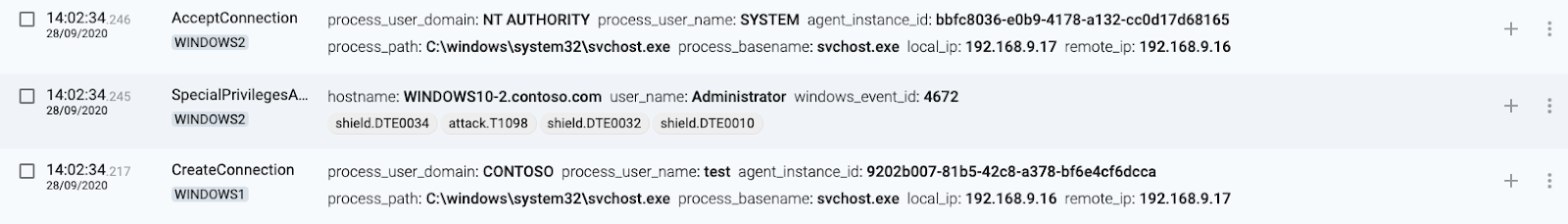
3 WINDOWS1(source) connects from wmic.exe
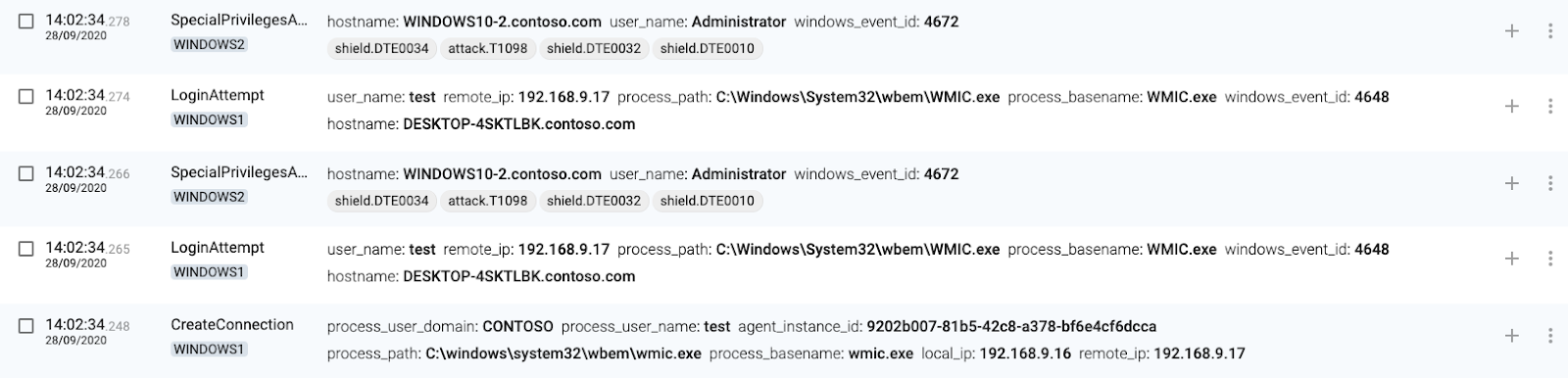
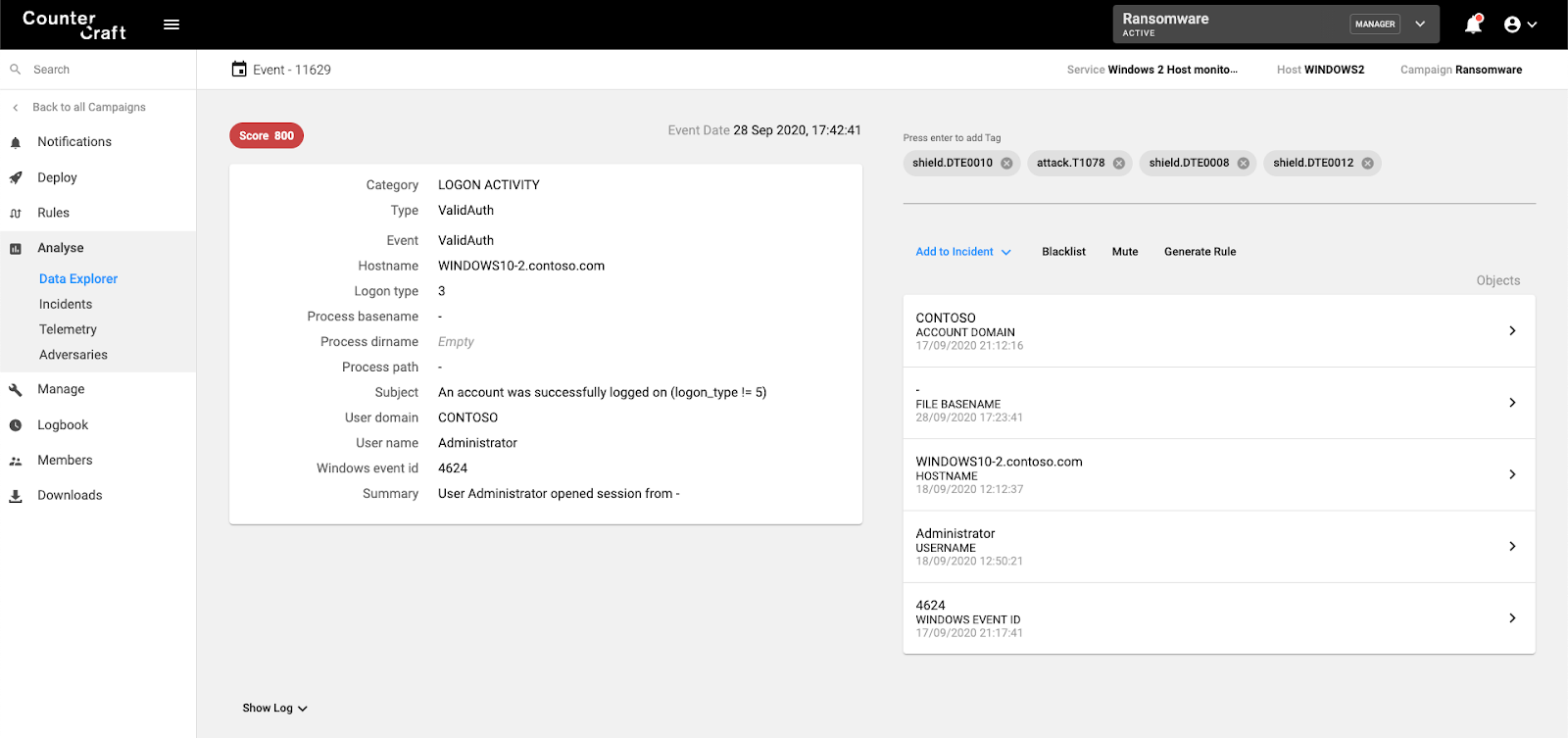
4 WINDOWS2(destination) authenticates connection
5 WINDOWS2(destination) executes command
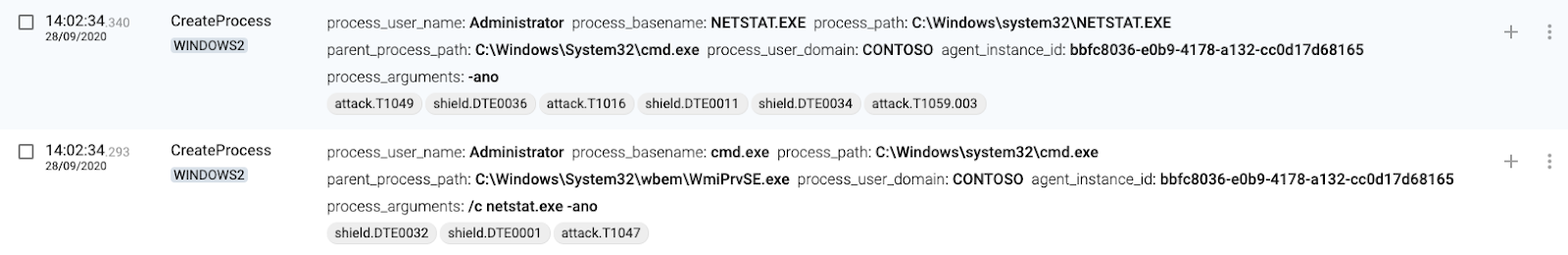
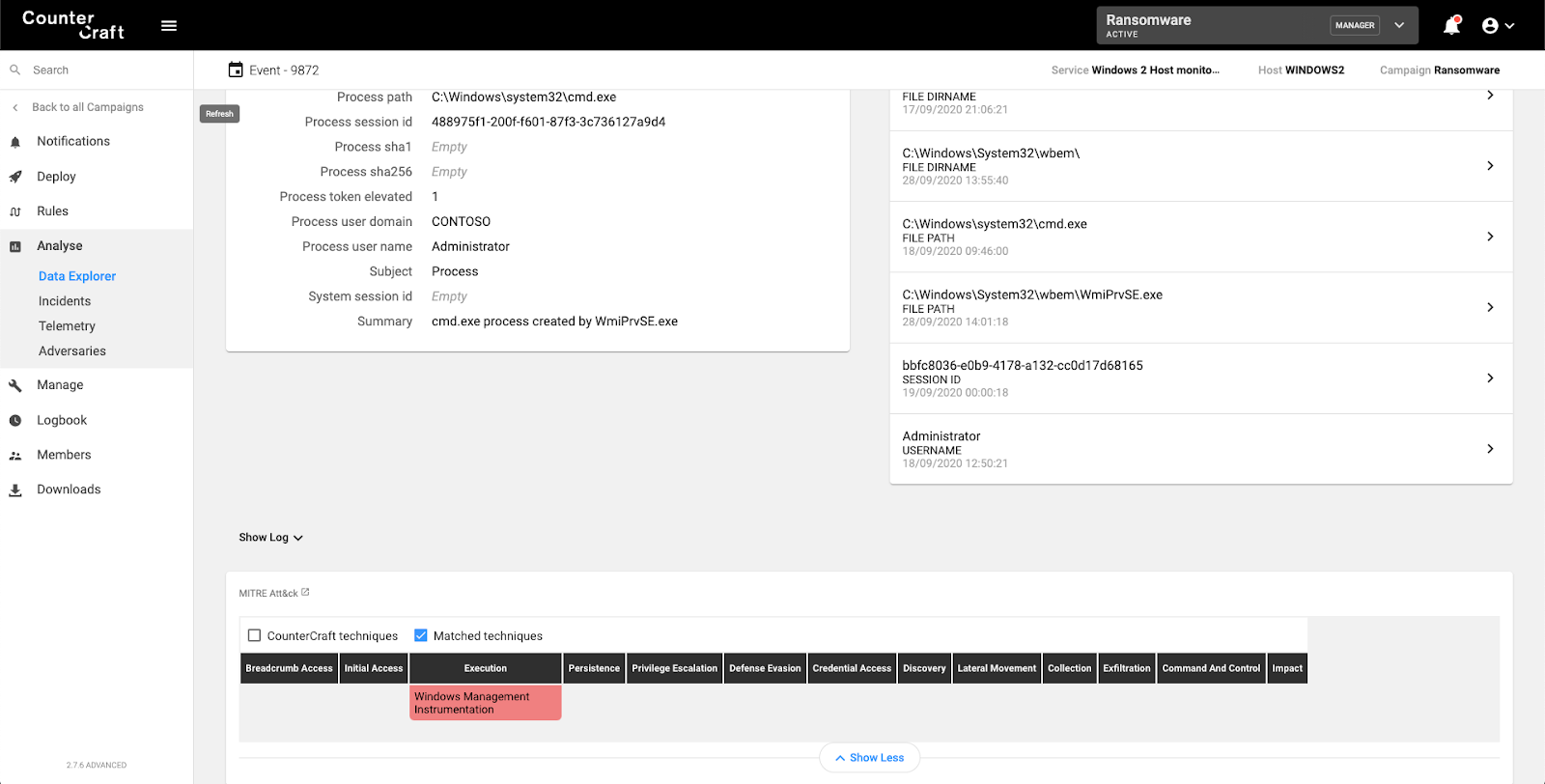
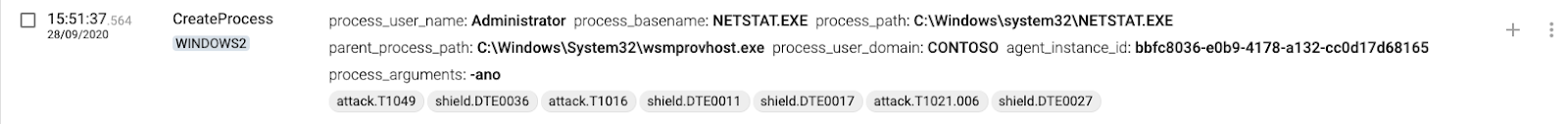
The CreateProcess command is mapped to T1047 – Windows Management Instrumentation.
WinRM
1 WINDOWS1(source) executes Enter-PSSession
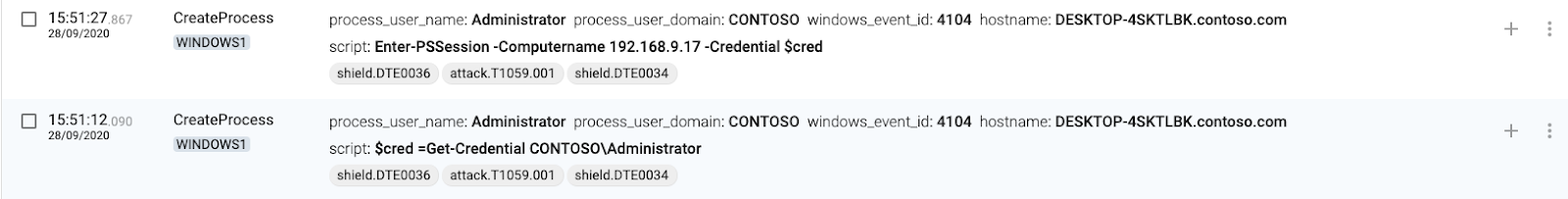
2 WINDOWS1(source) connects to WINDOWS2(target)
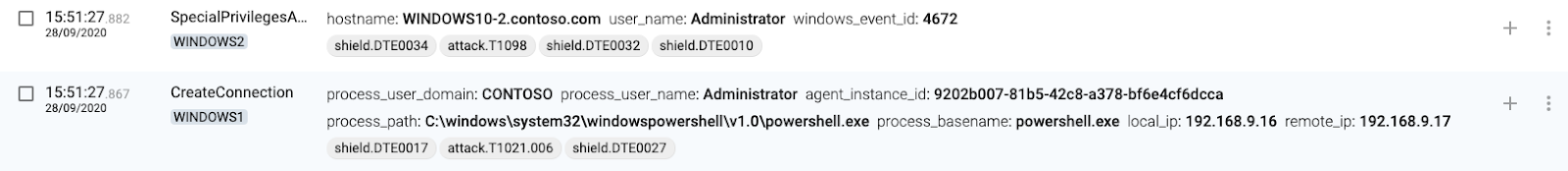
3 WINDOWS2(destination) authenticates connection
4 WINDOWS(destination) creates wsmprovhost.exe process
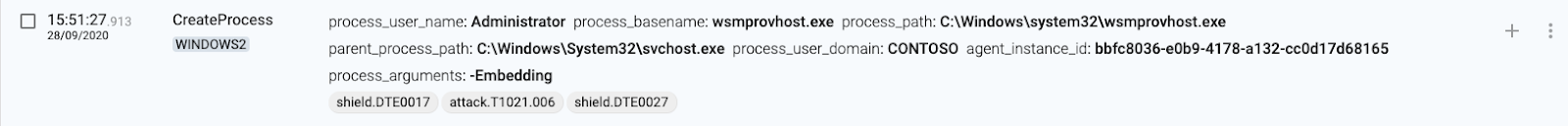
5 WINDOWS2(destination) creates temporary files for execution
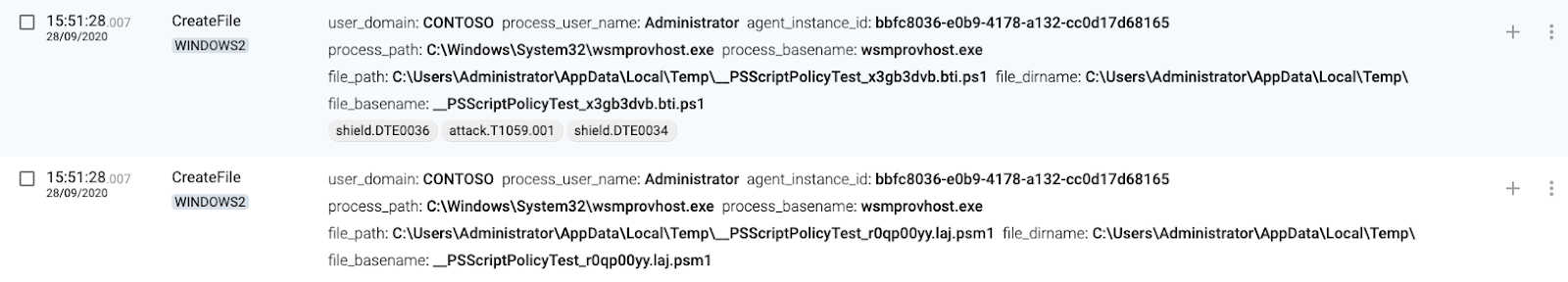
6 WINDOWS2(destination) executes process

PsExec
1 WINDOWS1(source) executes PsExec
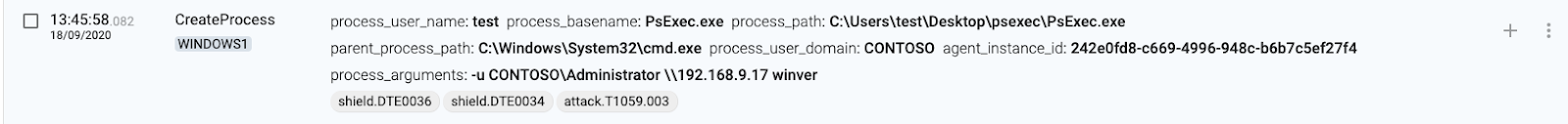
2 WINDOWS1(source) connects to AD

3 WINDOWS1(source) sets SysInternals EULA
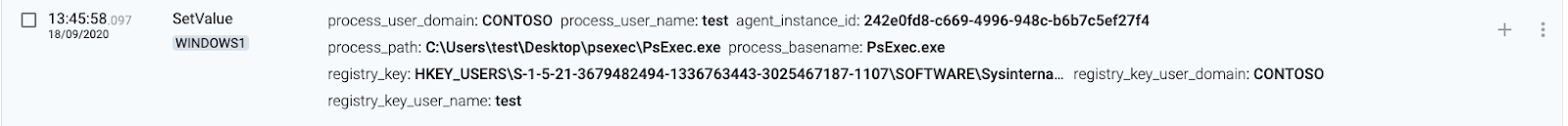
4 WINDOWS2(destination) authenticates connection
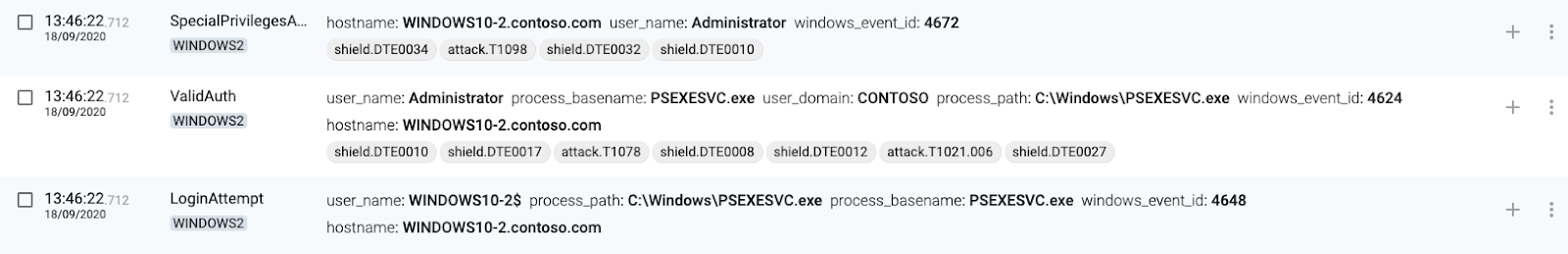
5 WINDOWS2(destination) accepts connections to IPC$
6 WINDOWS2(destination) accepts connection from services.exe

7 WINDOWS2(destination) accepts connections to ADMIN$
8 WINDOWS2(destination) accepts more connections from WINDOWS1
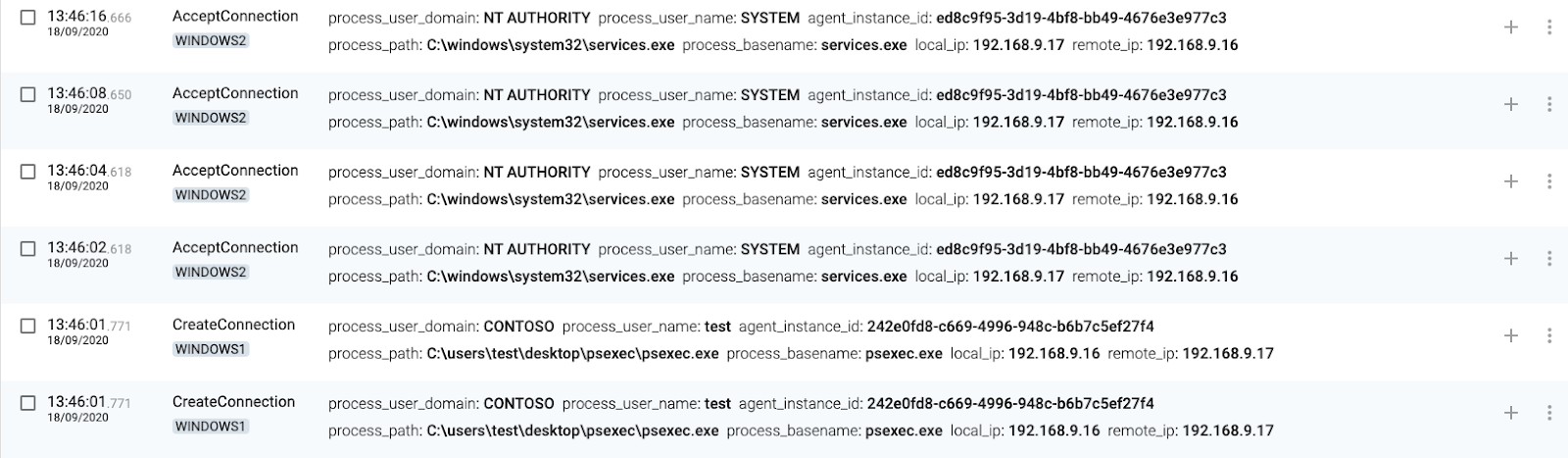
9 WINDOWS2(destination) creates a service named PSEXESVC
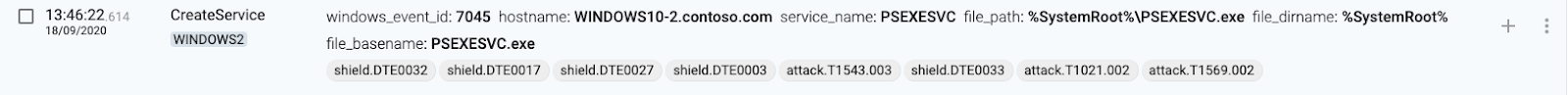
10 WINDOWS2(destination) creates process through the new PSEXESVC service
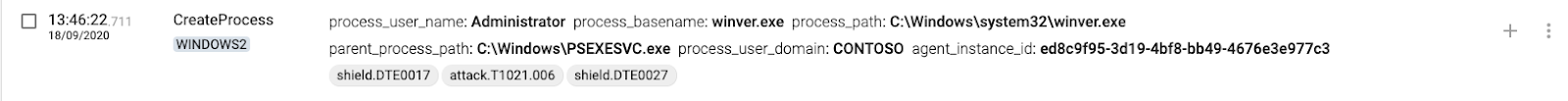

Remote Scheduled Tasks
1 WINDOWS1(source) executes schtasks.exe

2 WINDOWS1(source) connects to WINDOWS2
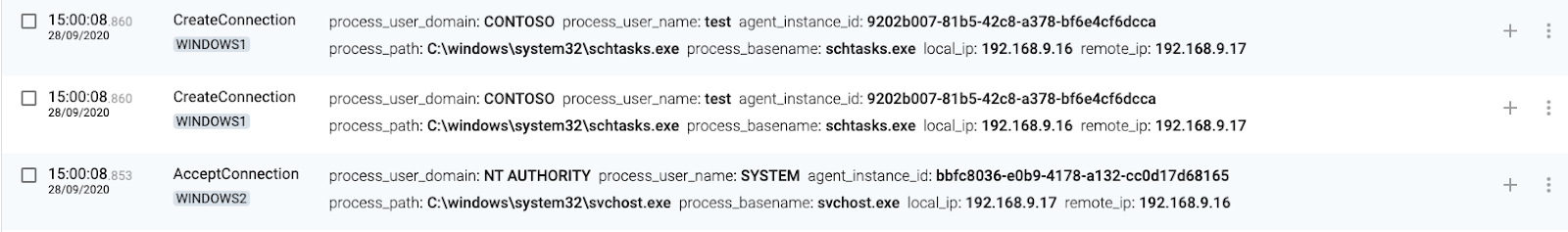
3 WINDOWS1(source) authenticates locally

4 WINDOWS2(destination) authenticates connection

5 WINDOWS2(destination) creates scheduled task
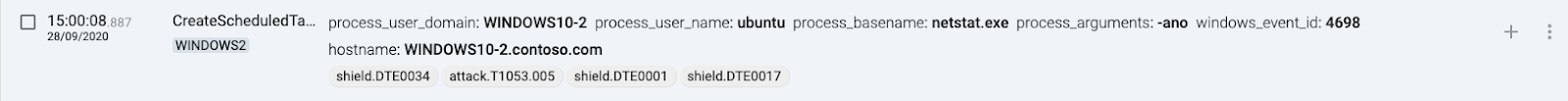
Target host will generate events when any shared folders access is attempted, mapped to T1053.005 – Scheduled Task/Job.

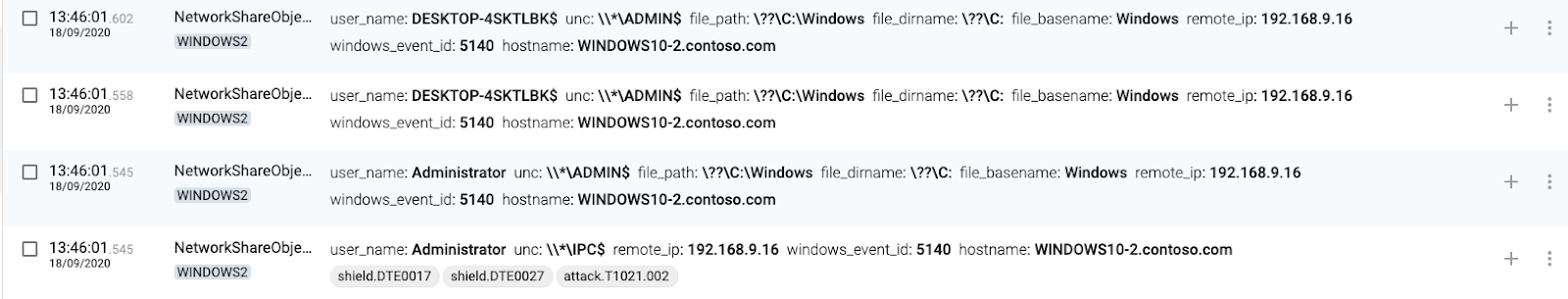
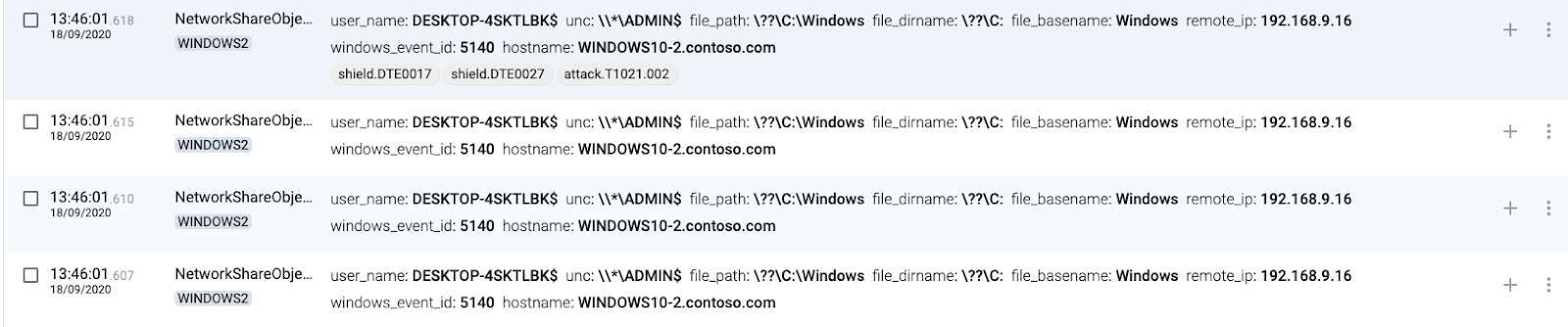
Shared Folders
1 WINDOWS1(source) connects to WINDOWS2 shared folder
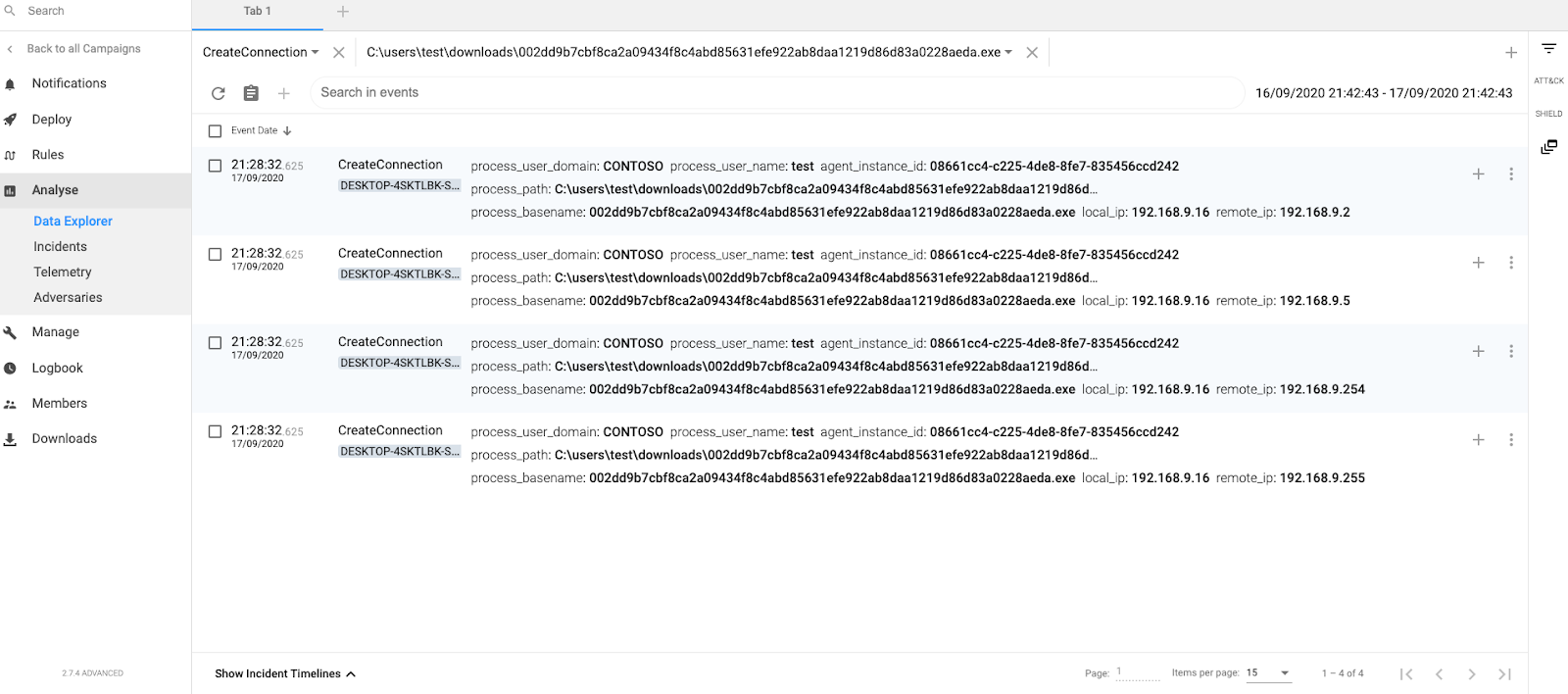
2 WINDOWS2(destination) accepts connection. The target machine (destination) will generate events when somebody is trying to access their shared folders, mapped to T1021.002 – SMB/Windows Admin Shares.
RDP
1 WINDOWS1(source) executes mstsc.exe

2 WINDOWS1(source) creates or updates the Default.rdp file
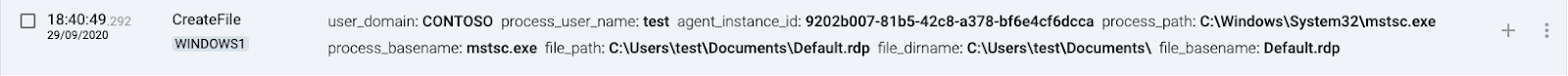
3 WINDOWS1(source) connects to the remote desktop
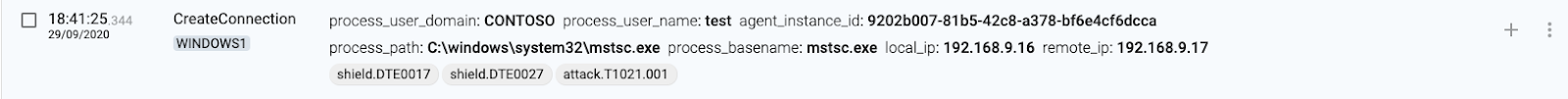
4 WINDOWS2(destination) authenticates connection

5 WINDOWS2(destination) loads the Microsoft Remote Desktop Input Driver

GPO Startup Script
Startup and Shutdown GPO scripts can be abused for massive execution. There will not be any authentication event, but there will be a CreateProcess event whose parent is gpscript.exe.
[Process] [CreateProcess] AgentSessionID=1e171c18-7d5e-4d17-96ae-f07e5594bc59 User=NT AUTHORITY\SYSTEM SessionID=a6172680-7495-f05f-982a-450a48e22f96 WindowsSessionID=0 IntegrityLevel=0x4000 AppContainer=0 TokenElevated=1 BootID=75b5d745-ebe7-f777-a441-2ac90620c450 Pid=4572 Process=C:\Windows\System32\notepad.exe ParentId=3548 ParentProcess=C:\Windows\System32\gpscript.exe CommandLine="C:\Windows\System32\notepad.exe" "\\contoso.com\sysvol\contoso.com\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Scripts\Startup\malicious_script.ps1" Id= Md5= Sha1= Sha256=
Conclusion
Finally, we have added some tables that review the important techniques for detecting ransomware and lateral movement (as part of a larger planned attack). All the techniques can be fully implemented on CounterCraft´s Threat Deception platform.
Ransomware Techniques Detection Summary

Lateral Movement Detection Summary

Please get in contact with us if you’d like to use our threat deception platform to provide you with rapid and clear assurance against ransomware attacks.
Author: David Barroso, CEO & Founder