Whatever industry you’re in, whether you’re a critical infrastructure provider, giant multinational, or micro business, you’re a target for cyber attackers. And most of the time, whatever security measures you put in place, bad actors will infiltrate your network. That’s just a fact.
Once a cyber attacker has made it inside your IT environment, three questions arise:
- How long will they remain in your network?
- What will they do while they’re there?
- How will you get them out?
What many organizations don’t realize is that they can influence the answers to all three of these questions. One straightforward technology – threat intelligence powered by deception – can help you detect breaches rapidly, control attackers’ malicious actions, and give you time to neutralize the breach.
In this article, we’ll look in more detail at how threat intelligence powered by deception helps you detect breaches faster. We’ll also share a story of how one of the most prominent organizations in the world, with top-rated cybersecurity precautions in place, still got breached by attackers who remained undetected for an extended period of time.
Why early detection matters for minimizing data breach impact
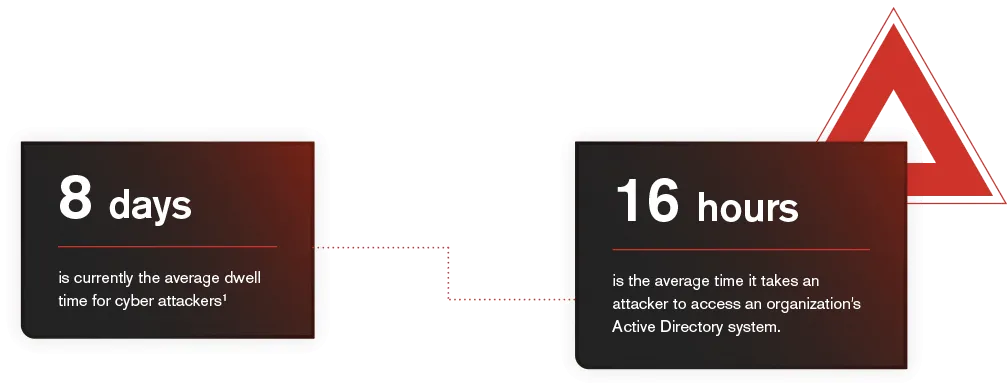
The average dwell time for cyber attackers is currently eight days . (Dwell time is the time between the attacker breaching the network and them being detected.)
An attacker can do a lot of damage in eight days. It takes an average of 16 hours for an attacker to access an organization’s Active Directory system, where they can escalate their privileges and carry out even more nefarious activities. Eight days is more than enough for an attacker to locate your most essential business-sensitive data, while it only takes mere minutes to drop a piece of malware or ransomware.
These stats make it easy to see why early detection of a network breach is vital. The earlier you detect a breach, the earlier you can respond, ejecting the attackers before they can do their worst work and minimizing data breach impact. After you’ve removed them from your network, your job is to repair the damage they caused and fix the vulnerabilities they exploited.
However, if you can neutralize a cyber attack before the attackers breach your system, that’s even better. Threat intelligence powered by deception gives you this capability. We’ll look at this in more detail later, but first, we’ll share a story to illustrate how easily attackers can infiltrate a network and then evade detection, even in the most well-resourced organizations.
US federal agency breached for five months
In July 2024, The Register reported that in the previous year, a US Cybersecurity and Infrastructure Security Agency (CISA) red team infiltrated an unnamed federal agency, remaining in their network for five months without detection. While this breach was (thankfully) an exercise rather than a genuine cyber attack, it exposed how hard it is for organizations to avoid breaches and detect attackers.
CISA performed this exercise on the agency without any notice, aiming to mimic how nation-state attackers might attempt to compromise the agency’s network. Their actions included:
- Gaining access through an unpatched vulnerability in the agency’s Oracle Solaris software
- Carried out successful phishing attacks on agency employees to gain privileged access to the system
- Discovered unsecured administrator credentials for unimpeded access to the agency’s data
As worrying as it is for the agency that the red team could break into their network, the exercise also exposed procedural failures. For example, during the probe, the red team informed the agency about the vulnerability they exploited to access the network, but it still took more than two weeks for them to fix it. They also discovered administrators were using weak passwords that had not been changed in more than eight years, severely compromising their access privileges.
All in all, the agency took five months to detect the presence of CISA in their system. It would have been even longer if CISA hadn’t decided to let the agency know what they had been doing, ending the exercise.
Lessons learned about data breach impact
What lessons can be learned from this story? Perhaps the most relevant lesson is that if a US federal agency, backed with ample cybersecurity resources, can be infiltrated, anyone can. Nobody can afford to feel complacent, believing you have attack-proof cybersecurity measures in place, or that you’re too small and insignificant to be a target. If you have data, bad actors want it.
The next lesson is that if you’re waiting for attackers to be inside your network before you respond, it’s already too late. The unnamed US federal agency was relying on spotting indicators of compromise (IOCs) before responding to cyber threats, but the CISA red team was in their system for five months without being detected (it would’ve been longer if CISA hadn’t given up their cover).
Finally, organizations of all sizes need to do more to lessen the impact of network breaches. This includes educating staff on the importance of cybersecurity, changing passwords regularly and being more vigilant against phishing. Organizations should also do more to safeguard their network technologically. CISA recommended that the agency segment its network to limit potential attackers’ movements and bring in new technologies to create a ‘secure-by-design’ approach.
But what if you could neutralize cyber threats before they even enter your network? What if you could discover attackers’ identities, aims and methods before a breach occurs? That’s where threat intelligence powered by deception comes in.
Deception technology for rapid threat detection
Threat intelligence powered by deception technology – such as CounterCraft’s The Platform – is the most effective way to identify threats and mitigate them before a breach can take place.
While there’s no silver bullet in cybersecurity, deception technology adds an extra layer of detection to your security stack, turning your approach from reactive to proactive.
Here’s how The Platform works: CounterCraft’s deception technology creates a digital twin of your network running parallel to your actual network. It then drops a trail of breadcrumbs to lure potential cyber attackers over.
Cyber attackers enter the decoy network and go about their malicious business (e.g. dropping malware, stealing data, instigating a DDoS attack) thinking they’re in your actual network. But of course, they’re not. While the attackers are in the digital twin, the deception technology monitors their activity, so you can predict their next moves.
The second an attacker interacts with CounterCraft’s decoy, the technology generates an alert. For network security teams that often find themselves wasting time chasing false positives, an alert generated by deception-powered threat intelligence is immediate, relevant and evidence of genuine malicious activity. If you act on only one alert, it should be one from CounterCraft.
The security team can then take the necessary steps to fix any vulnerabilities and better secure their network for the future.
The CounterCraft solution
CounterCraft is trusted by some of the world’s top critical infrastructure providers, banks, telcos and retailers as well as government agencies. They understand the power of threat intelligence driven by deception to thwart cyber attacks before they even begin. They know how effective it is to proactively take the fight to cyber attackers rather than wait for them to arrive.
CounterCraft’s platform is easy to set up and integrates with all major cybersecurity platforms. In minutes, your security team could be receiving specific, actionable threat intelligence of genuine attack attempts happening around your environment. And you could initiate an effective, robust response.
Breaches happen, so why wait? Request a tailored demo from our team of experts and get started with CounterCraft’s threat intelligence powered by deception technology today.
To find out more, visit our Solutions page.
Sources:
[1] https://www.infosecurity-magazine.com/news/attack-dwell-times-faster/
