From ransomware to malware affecting critical infrastructure, cyber attacks are more mainstream and more damaging than ever. Keeping up with all the attack vectors and evolving threats gets more challenging by the day. IDG’s recently released 2021 Security Priorities study is an important look at the state of security strategies today. This 2021 report provides an in-depth look at the security landscape today from the valuable viewpoint of its top leaders and decision makers.
To appreciate the evolving role of cybersecurity in enterprise, you only have to take a look at some of the statistics offered up in the report.
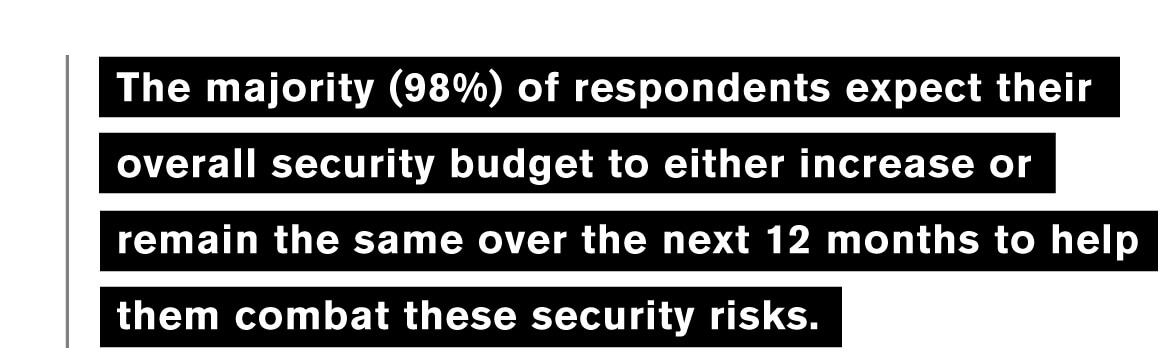
(2021 Security Priorities Study)
It paints a picture of security leaders that are launching new efforts to become better prepared for the next unexpected security incident that comes their way. The report highlights expectations these leaders have around budgets, as well as the priorities that will influence how they allocate these budgets.

(2021 Security Priorities sample slides)
According to the report, expected to top the list of solutions being actively researched are Zero Trust technologies, SOAR (security orchestration, automation, and response), SASE (secure access service edge), and deception technology. We were thrilled to see deception technology high on the list of solutions that leaders in cybersecurity are actively researching.
(For a primer on what exactly deception technology is, click here >)
We have also seen an increase in interest in deception, and have watched client after client benefit from early detection, strengthened networks and an all around more robust cybersecurity posture.

The Evolution of the Product Category
The product category for deception has matured rapidly over the last 5-7 years. The category solves problems that have always been around, and is especially useful for OT networks, IoT, SCADA, and sophisticated, high-stakes networks.
Nowadays, some governments have even begun to make the use of deception technology obligatory in certain high-stakes sectors, like banking. A mixture of defense and offense is becoming more and more common across many sectors.
Deception makes up a small part of the cybersecurity market, but it is growing and gaining market share every year. With still only a few key players, buyers have the option to choose between basic solutions that are not much more than honeypots or deception platforms that offer total customization and adaptation, with an endless set of capabilities.

Deception Ready for Mass Market
Deception is easier to deploy than ever, and there are even deception-as-a-service options available for mass market rollout. These threat intelligence services are managed by an expert team (freeing up an organization’s resources) that identifies cyber threats before they attack your online IT assets, remote workers, and networks.These cloud-based managed services are fast and easy to implement with no additional resources needed.
Read how deception as a service can help teams with little resources to spare >

Why Deception is Necessary
Deception environments are exceptionally effective because they generate known “bad” data. No one should be messing with them. So, the data they collect is clear and unequivocal. Deception is unique in its solution because:
- It can gather data without disturbing operational IT systems
- It helps analysts understand the context of attacks
- allows teams to observe and react to intruders in real time
- tells security teams how real threat actors are behaving against your infrastructure
This is how to see clear signals in all the noise. The threat data collected can be used as an input into threat hunting across larger networks and for training other AI based systems (more on that here). Deception environments provide concentrated quantities of highly valuable threat data than other comparable detection systems.
Threat intel analysts need to be more agile and, which is why mapping real-time attacks in deception environments will help. This will alert your teams on where you’re exposed, as well as inform you on which control uplifts are needed. You can also watch their behavior and place decoys as you go, which can provide you with specific, timely information on your attackers.
Click here for the top 10 business benefits of cyber deception >

How to Move Forward
The problems highlighted in the 2021 Security Priorities report shows the need for solutions that are malware agnostic. Readiness to work with deception technology can depend on your current security team and your operation. Find out if your existing network infrastructure is fit for deception by contacting us.
Meeting the major goals that cybersecurity leaders have for the upcoming year —detecting, protecting and managing attacks— can be done by building a complete cybersecurity strategy, using tools that give coverage where there has previously been little or none. Be sure to check out the 2021 Security Priorities report from IDG, it’s a fascinating read.
