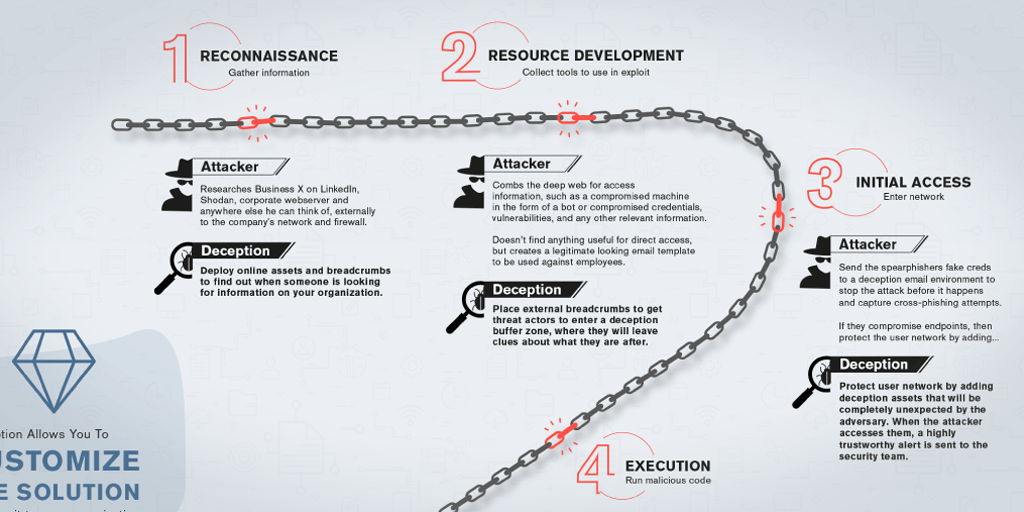
All cyber attacks, no matter how complex, share a similar DNA, and deception technology has an answer for nearly every attack stage. Check out our breakdown of a typical cybersecurity incident. In this infographic, you’ll find the steps threat actors often take when compromising a network, and how to stop them along the way, all in one handy infographic.

Like Jim Morrison said, this is the end. But you can…