The concept of attack trees or attack paths and how to increase the cost for the attacker in time and resources (not always monetary) has been discussed many times and it is still considered a good approach in any modern security strategy. Bruce Schneier explained the concept in the Dr. Dobb’s Journal in 1999K Leveraging an attack tree model is not only an important step towards formalizing our understanding of attacks, but also a means to understanding our defense.
Stephan Chennette from AttackIQ also shared some interesting comments about attack paths:
“Longer attack paths are less appealing to the attacker and more likely to fail. If you can make the attacker take more actions, even if they have a moderate or good chance of succeeding, you strengthen the probability of your defenses succeeding. This is true of your ability to prevent, detect, or respond to an alert and/or remediate an incident. As you look at building out your security program, whether you look at the Cyber Kill Chain® or the MITRE ATT&CK Framework, the more effective defenses you have for each phase of an attack from Persistence to Impact, the more steps an attacker has to go through to reach their intended goal, the more mistakes they can make, and the more likely your defenses will thwart their efforts. Remember, sophisticated attackers run like a business and have deadlines, where the inability to meet deadlines can cause stress and mistakes. As a defender, exploit that fact.”
More recently, Verizon, in its 2019 Data Breach Investigation Report stated that the majority of the incidents had short attack paths and it is confirmed in its recent 2020 Data Breach Investigation Report 2020 Data Breach Investigation Report: “Attackers prefer short paths and rarely attempt long paths. This means anything you can easily throw in their way to increase the number of actions they have to take is likely to significantly decrease their chance of absconding with the data.”
Both statements emphasize the fact that, as defenders, we need to exploit that weakness. How? By using attack paths in Deception Campaigns.

How to Feign Short Attack Paths in Deception Campaigns
The use of attack paths in deception campaigns has two phases: first, deploy breadcrumbs everywhere, so the attacker can use them in order to shorten their attack paths. Secondly, design an attack path as long as needed after you have been able to reroute the attacker to your path. The longer the path, the more intelligence you can gather about them, apart from rising the cost of the attack, and controlling their behaviour.
Let’s start with some examples of how we can attract attackers to our path that pretends to be a shorter one:
- A GPO policy containing some credentials in a startup script easily found in SYSVOL.
- A Microsoft Office document explaining how to access the new HR web portal, stored in an HR shared folder.
- A public exposed and vulnerable Apache Struts with a signed SSL certificate found by Shodan or Censys.
- An SSH keypair in a linux folder.
- A QR code found in the trash bin.
- Etc.
Once we’ve got the attacker’s attention, it’s likely that they’ll prefer to take the shortest path instead of trying to look for other ways to compromise the organization. Again, credibility is key in these deception campaigns (real hosts, real services, credible cover story, etc.), as skilled attackers can easily detect we are trying to deceive them.
Now, it’s time to set up the path we want the attacker to follow. We can have an entire deception campaign used in the attack path, or mix production endpoints and hosts with deception hosts or services in order to increase the chances of deceiving the attackers.
In the following image you can see an example of an attack path after we managed to redirect the attacker to our campaign:
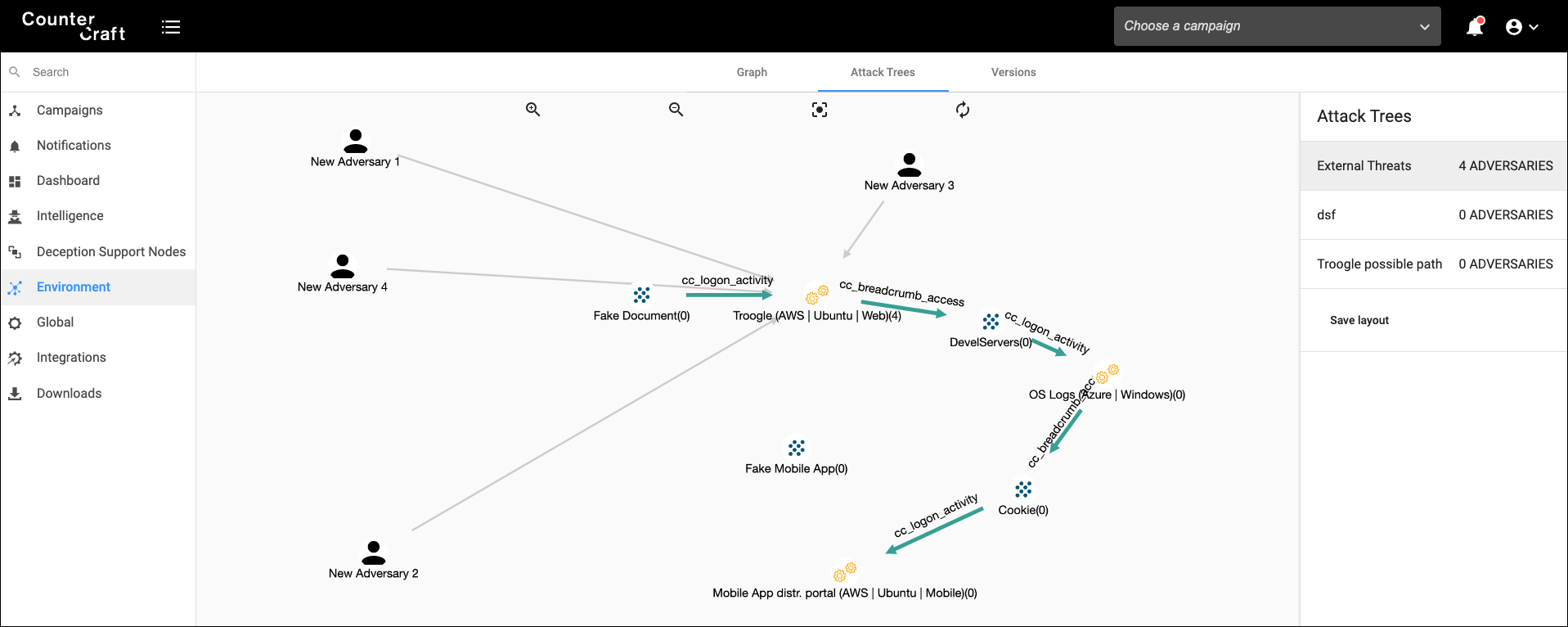
*Click to enlarge image*

Nodes of the the Attack Path
- A Microsoft Office document explaining how to connect to a new HR portal (including credentials). This document is stored in an HR shared folder with no authentication.
- An HR web portal that contains information about its database settings in a Windows 2019 server
- A Windows 2019 server with some special cookies in Chrome for accessing a backup web portal.
In each of those different nodes, we are gathering significant telemetry of the attacker’s activity: network connections, file creations, kernel manipulation, commands executed, etc. The concept is similar to having a full-featured sandbox that consists of an unlimited number of assets and it’s running 24×7 until we have decided it’s time to call our incident response team.
Each path in the attack trees can have different branches, depending on the complexity; we can have different starting nodes (a document, the GPO policy, an Active Directory user account, etc.) and all of them can point to the next stage. Or, we can have different exits depending on the skills of the attacker; we can even design our own choose-your-own-adventure interactive attack path, where the attacker will make decisions and choose different paths depending on their decisions.
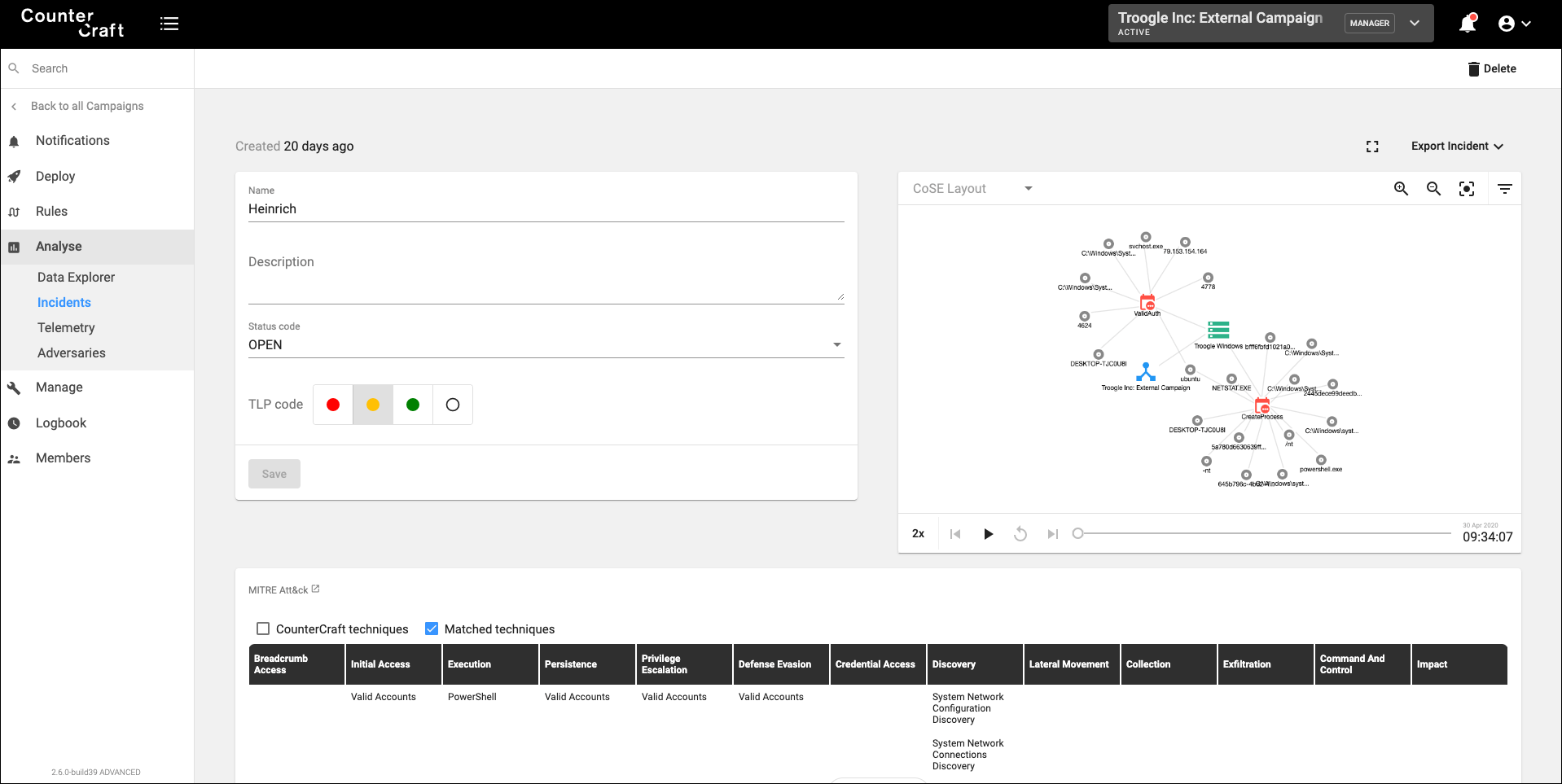
*Click to enlarge image*

During the attacker’s journey in our attack paths, it is really important to start putting into action all the intelligence generated in real time. As we are getting information about what the attacker is doing, we can integrate that information into other security products, like SOAR, SIEM, TIP, etc., triggering other security playbooks that can help to control the attacker and put the security measures in place, as well as alert our incident response team.

Author: David Barroso, CEO and Founder
