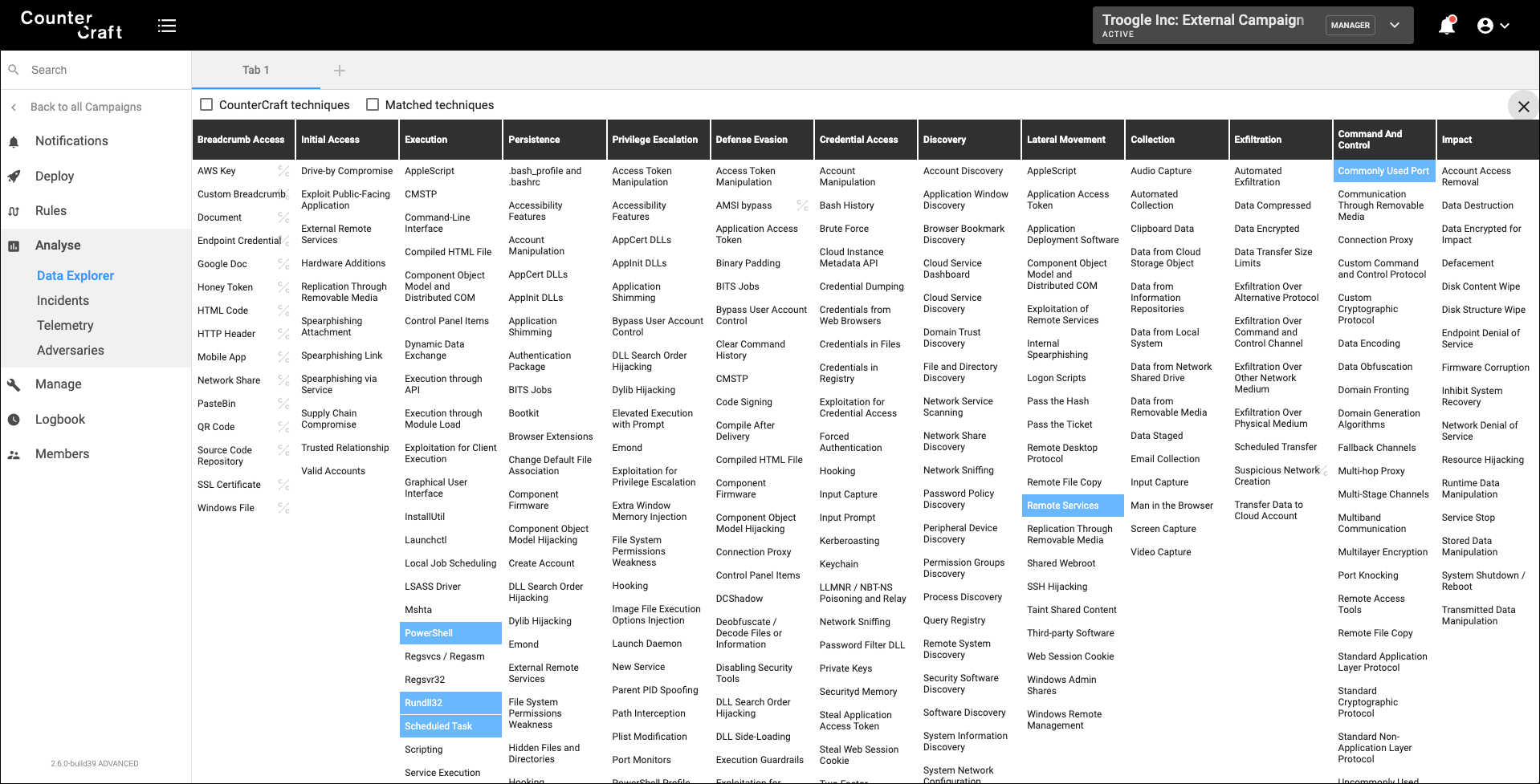
The growing popularity of MITRE ATT&CK is a good indication that finally, we have a common language to describe the tools, techniques and procedures (TTPs) that threat actors are using in their daily operations.
At CounterCraft, we have been firm believers in MITRE ATT&CK; we first added support for the first versions of the ATT&CK Matrix in our Deception Director product at the end of 2018, and now we are rolling out all the new subtechniques. We did a great deal of work classifying all the events generated from the telemetry we collect from our deception campaigns. We even created some new techniques that we thought were important and they weren’t available in the latest ATT&CK releases.
*Click to enlarge image*

So far, our ATT&CK journey has been great: our users love the clear view of what is happening in their deception environment that ATT&CK provides. Their debate then shifts from talking about log events to the operational impact of TTPs. But, ATT&CK does not only help us in our mission to get more operational information, we are also using ATT&CK for two other use cases:
- To test all our deception campaigns against known threat actor TTPs and modus operandi to confirm we can detect threat actor activity, when it occurs.
- To create tailored deception campaigns targeting the threat actors that are attacking a specific vertical or geography.
In this article we will focus on the second main use case and we will talk about the other use case in future blog posts. Adam Pennington also covered this topic in his recent FIRST CTI presentation: Bringing Intelligence into Cyber Deception with MITRE ATT&CK.

Targeted Deception Campaigns
Deception can be used in different scenarios or use cases: as a basic threat detection solution, as a threat hunting tool, or as an advanced active attacker engagement strategy. Depending on the sophistication of the use case, we will be able to obtain a different range of results.
Let’s focus on the most advanced use case: we want to be able to actively engage with our attackers. In this case, we need to perform a series of steps that will help to achieve our mission goals:
1. Identify our adversaries: know adversary’s preconceptions, expectations and reactions. Start choosing adversaries targeting your vertical (for example, engineering, insurance, government, etc.) and/or your geography. Do not try to be too ambitious and start with 3-5 adversaries.
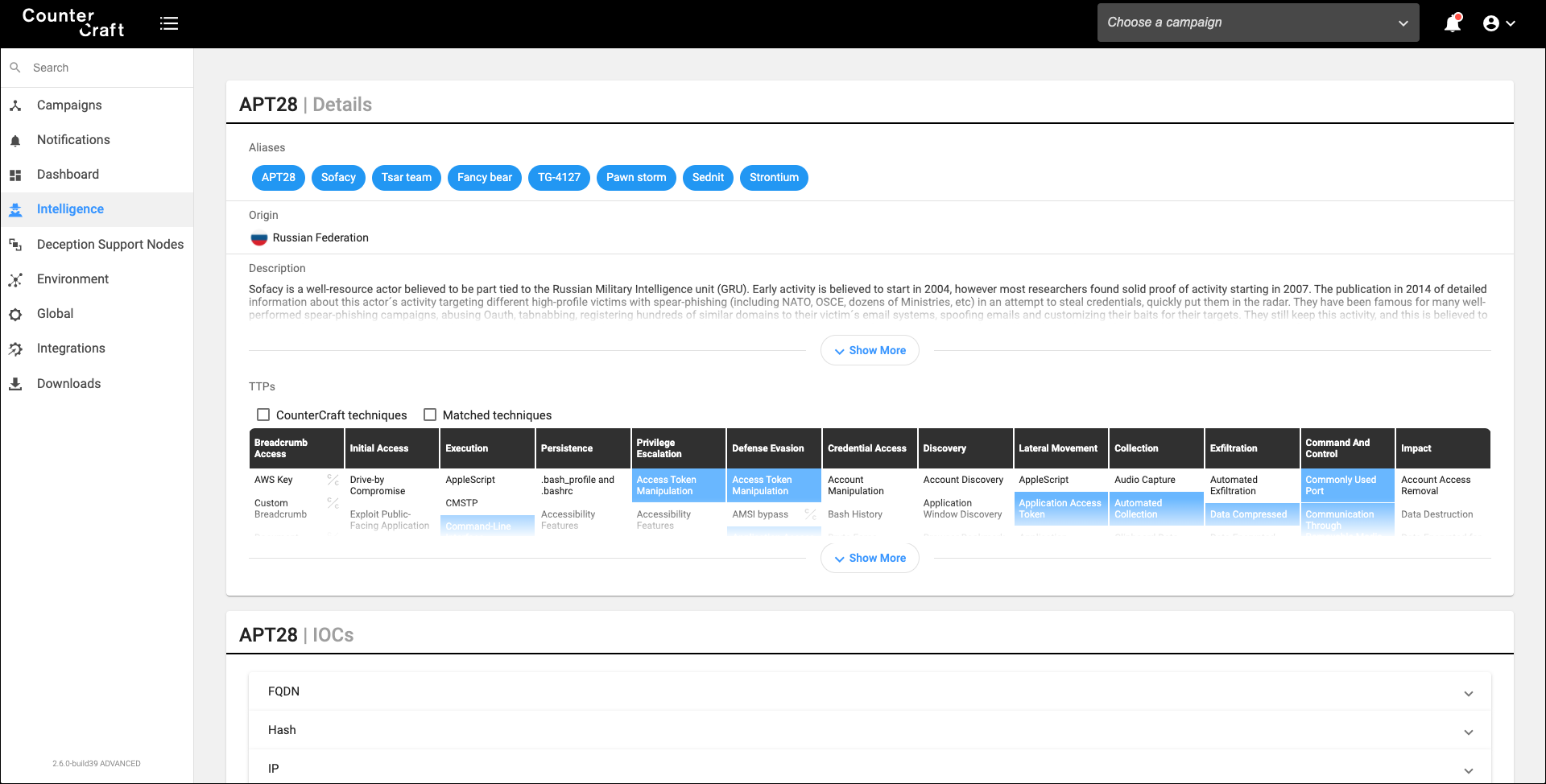
2. Research about the TTPs they use in their attacks: MITRE ATT&CK is a great resource for known threat actors, but compile your own adversaries from public or private sources if you need it. You can also collect all the IOCs related to them, and the CVEs they try to exploit. The following image is an example of the techniques used by APT28, but it also includes known IOCs and CVEs.
*Click to enlarge image*

3.Design your deception campaigns: credibility is key. Determine what services and breadcrumbs need to be deployed, and the cover story you are going to use. Mimic the same resources that are available in your organization but tailor some of those resources to match your adversary appetite. For example, if they always use spear phishing emails for compromising internal users accounts, design a deception campaign that supports that technique. Or, if they look for vulnerable Apache Struts servers, include them in your design.
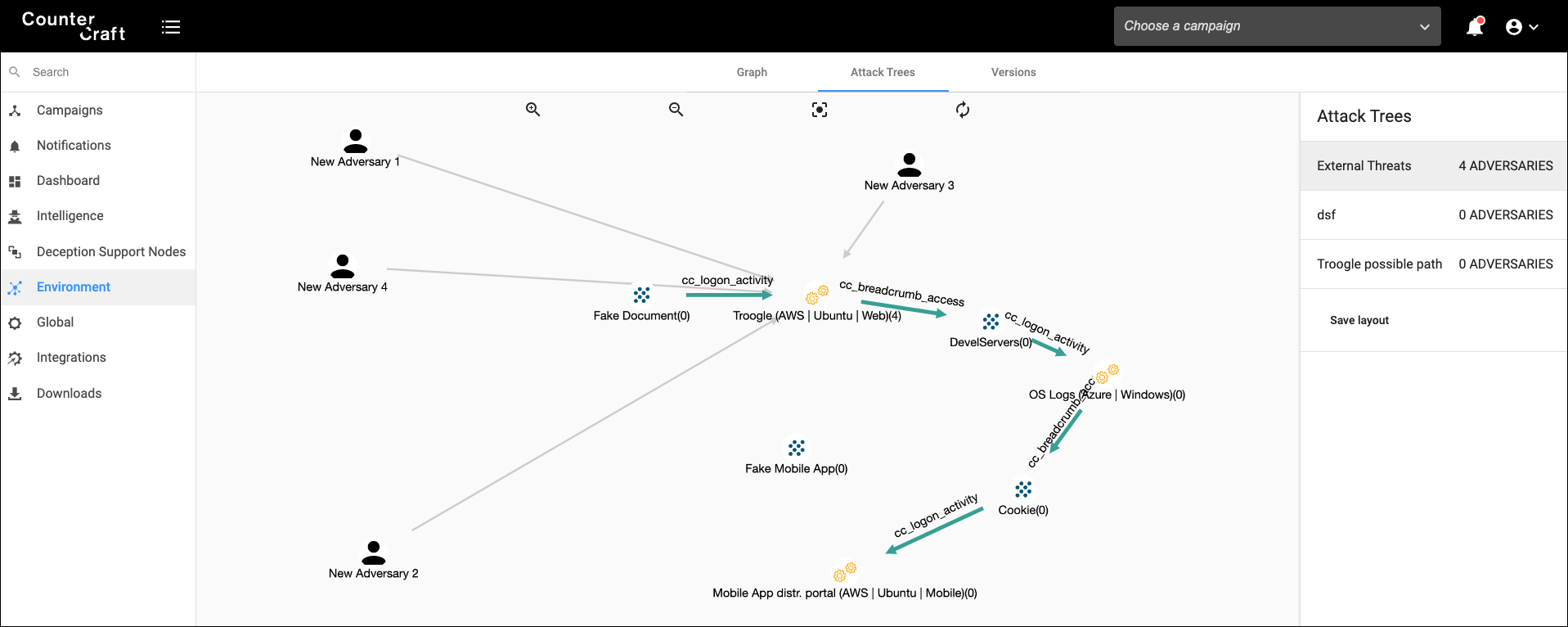
4.Create attack trees for those campaigns: We want to engage with the attacker as long as possible, so credible attack trees can be very helpful. In the following image we can see four adversaries in our deception campaign. They are still in the first node of our attack tree, but depending on their skills and appetite, they will move around the tree.
*Click to enlarge image*

5. Deploy your campaign: use a logbook for all the deployment events (hosts, services, breadcrumbs, cloud entities, etc.)
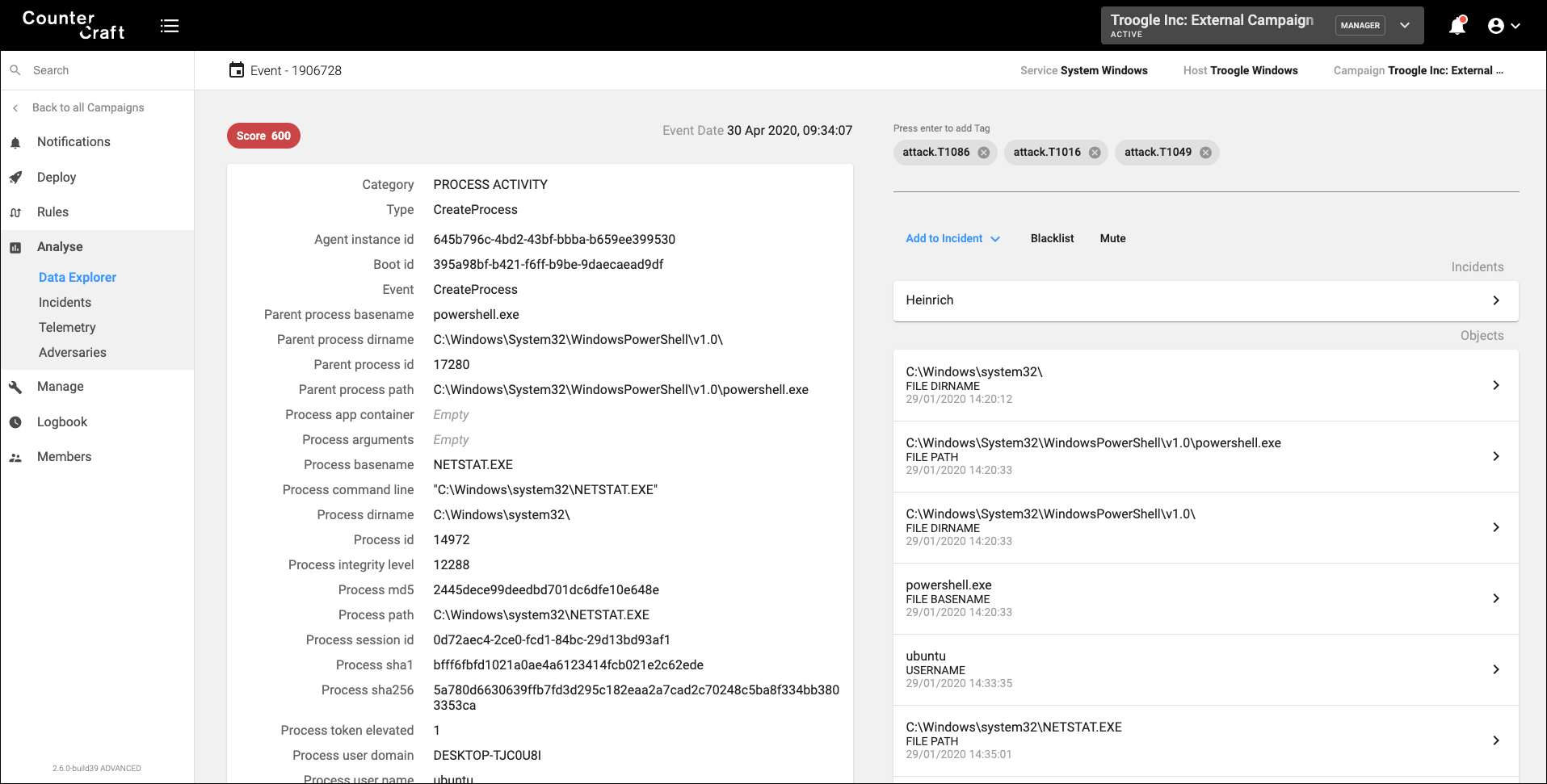
6. Collect, monitor and control: gather all the telemetry from your campaigns, and start correlating all your events. MITRE ATT&CK to the rescue again! Map all your observations to valid techniques and see if you can find any known IOCs. In the following image we can see a netstat.exe execution and how the event is mapped to the techniques T1016, T1049, T1086.
*Click to enlarge image*

7. Engage with the attacker: your deception campaigns need to be dynamic and change based on attacker engagement in real time. This will increase the attacker dwell time in the deception environment and allow us to collect better intel and delay the attack against real infrastructure. For example, if the attacker has compromised a host, and has opened a folder about a specific internal project, drop in real time another folder with other types of information (to discover their objectives). If the attacker is trying to compromise a specific host, drop some breadcrumbs with credentials in an attractive place. Or spin up a new machine that the attacker can find.
8. Make it actionable: integrate all your results with other products that take feeds. For example, create playbooks in your SOAR to automatically search for the collected TTPs and/or IOCs in your SIEM – identify adversaries in your deception environment and hunt them across your enterprise systems; correlate intelligence with your TIP; deploy more advanced deception campaigns, etc.

It looks like a long journey, but it is worth it. Not only are you going to be able to detect earlier than ever before, collect unique intelligence about your adversaries, but you also are able to engage, and manage their attack. It is the next step in your security strategy.
When we started CounterCraft we wanted to build a product that was able to improve your active defense posture. Today, all the steps above can be automated by using our Deception Platform. To find out more, please contact us.

Author: David Barroso, CEO and Founder
