Frameworks do not need to sit in the Security Operations Centre (SOC) or be buried away as part of a workflow process. These frameworks can be a powerful visual tool in the hands of the CISO and allow them to paint a vivid picture of not only where the current security posture is for their organisation but also where it needs to be. The goal is to turn these frameworks into powerful tools that help you visualise your security roadmap. To this end let us discuss a new framework that is being widely adopted: MITRE Shield (MS).

MITRE SHIELD
MITRE Shield can be described as a knowledge base that captures what has been termed as active defense tactics and techniques. What is Active Defense? This is a concept that has been co-opted from military terminology and is defined by the US department of defense as a strategy that deploys limited offensive action and denies an adversary a contested area or position. How is this achieved? Through the use of cyber deception, adversary engagement and cyber defense capabilities. You can use any one of these approaches to build your defense shield, or from a cost-effectiveness perspective seek to deploy a combination that is most effective. Before we delve any further into the key concepts let us take a look at the framework itself.

Tactics & Techniques
The MITRE Shield is split into tactics and techniques. These can be seen in the table below. What is interesting is how security leaders can use this to help them develop a cohesive security strategy that is based on actual cyber attacks against the organisation’s infrastructure. You want to get ahead of the attackers —why wait to detect them once they are inside your network before you realise that your defenses have failed? Now it’s possible to move detection to a much earlier part of the attack cycle and not only capture TTPs and IOCs, but also map what MITRE Shield defense techniques would be most effective at mitigating the TTPS and IOC’s that have been observed.
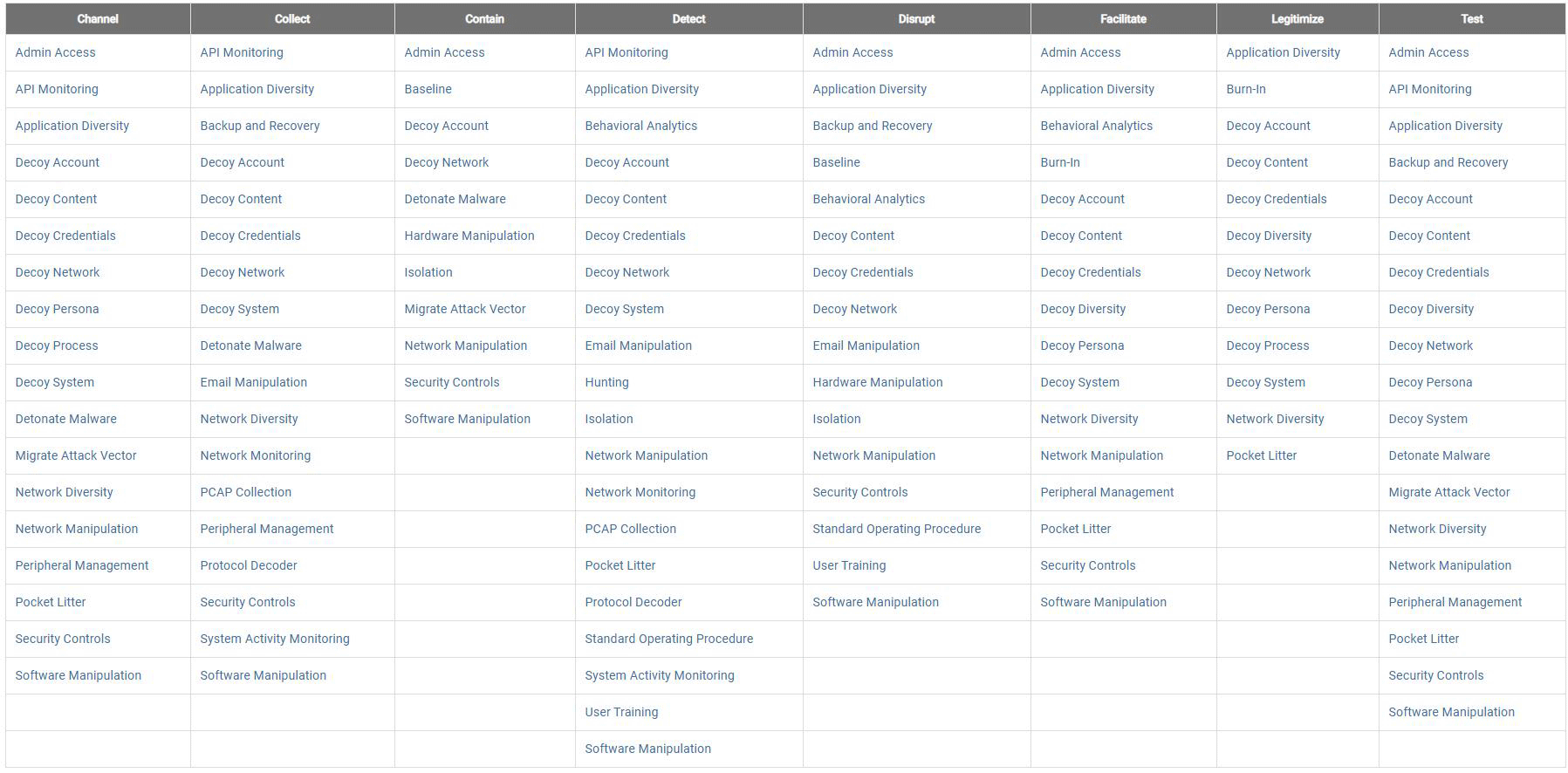
Source: MITRE Shield

If you have the capability of detecting attacks against your infrastructure —before attackers get anywhere near your actual infrastructure— and mapping what MITRE Shield tactics and techniques would be most effective in thwarting these attacks, what you have in effect is a roadmap as to what security controls you may need to introduce to mitigate attacks. This pictorial representation of what tactics and techniques could be effective would be a powerful visual tool in convincing both boards and other senior stakeholders of the necessity to deploy such controls. Below you can see such a mapping that is produced by the CounterCraft Cyber Deception Platform.
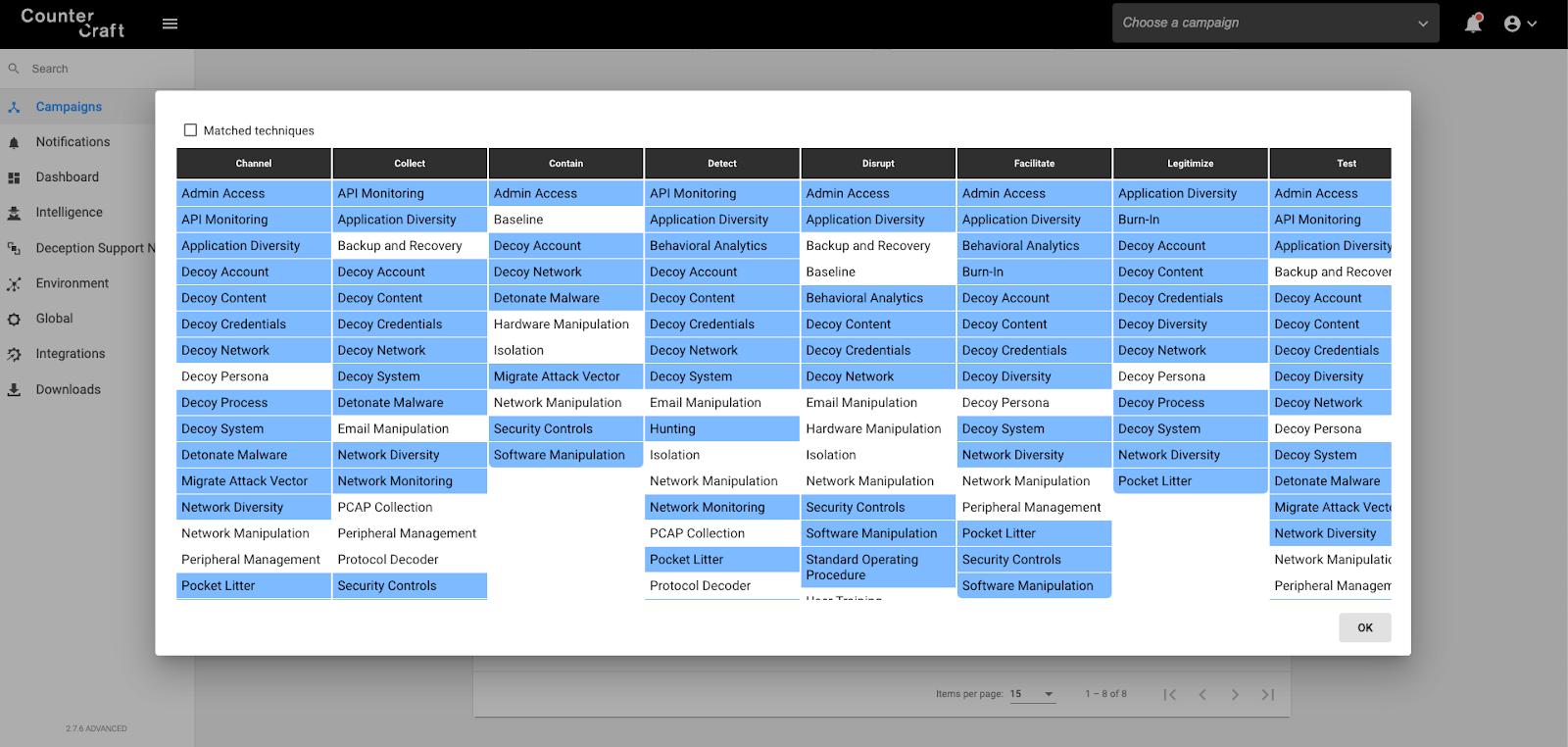

Security Roadmap
The CounterCraft Cyber Deception Platform has the ability to deploy campaigns that are purely external to your corporate environment. Sometimes, an objection may be raised: that organisations are increasing the level of risk by deploying deception campaigns externally. This is not not the case, if you have an online presence, where there is a high level of certainty that you are being attacked on an ongoing basis. Furthermore, the current security mantra is that you begin your security strategy from the assumption that you have already been breached. So, by deploying an external deception campaign, what are some of the key benefits you, as a CISO, could expect to see?

Detect & Map
By moving the detection component of cyberattacks to the outside your corporate network boundaries you will avoid any kind of business disruption. Remember that adversary engagement is a key component of the MITRE Shield’s tactical approach. By engaging the attackers, you will gain a valuable insight of how they might overcome the security controls you might already have in place. You will understand if the attackers are looking for persistence and adopting a stealthy approach, or if they are simply looking to move quickly to deliver a payload such as a ransomware or to get to valuable data and exfiltrate it as quickly as possible. In parallel you will receive real-time intelligence about the toolsets that are being used by the attackers to achieve their strategic goals, what remote access tools are being used to control the compromised asset, what type of traffic is being generated, and finally, the ports that are being used to communicate over. This is not an exhaustive list but a small sample of the types of intelligence that can be captured. The key here is that the intelligence is captured in real time, and is therefore actionable in real time as well.
The CounterCraft solution will provide you with a mapping of the attackers’ TTPs and IOCs in real time and in an automated manner, and will simultaneously generate the MITRE Shield matrix, which will enable you to understand what controls have failed in thwarting the attackers. Therefore, you are armed with a mapping of different security techniques that should be implemented in a pictorial manner, a roadmap that is board-ready. You have, through the use of the CounterCraft Cyber Deception Platform, generated a security approach and a strategy that will help you put in place controls that will detect and mitigate attacks that are targeting your organisation.

Final Thoughts
Too often, security leaders are faced with the impossible task of trying to condense what security controls are needed and why they are needed into a single slide . These presentations tend to be generic because the data that explains how attackers are trying to hack into an organisation’s network and therefore what controls are going to be most effective is simply not there. In other words, organisations don’t know where the greatest return on investment will be. Right now, security leaders can collect these data and have an automated mapping that is board-ready and that helps the board to understand how scarce security budgets can be spent to plug security controls that attackers are bypassing. If you want board-ready security roadmaps based on objective data sets then reach out to CounterCraft and let us show you how simple this is to put in practice.