With most employees working from home amid today’s COVID-19 outbreak, VPN and remote access to enterprise resources have drastically increased. This is a huge challenge for the IT and security departments as many security experts believe that the current VPN deployments are designed for a small percentage of employees of the organizations and not for the overwhelming number of teleworkers who now need to access them repeatedly throughout the workday. Many of these users can be tempted out of VPN access due to the associated slowing down or dropping of the connection, or the availability of unpatched desktop and laptop computers, and other non compatible devices where no VPN client is available. Besides, extensive use of personal collaboration apps for day to day activities like personal email, cloud-hosted email, cloud apps, Slack, Box, etc. is to be expected, with the threat of many credentials possibly shared or stored outside of the protected apps. All of these represent a serious cybersecurity risk in terms of credentials theft and data exfiltration as remote endpoints will also be storing more data, even if just temporarily.

Risks Associated with Remote Working are on the Rise
This urgent need to provide immediate remote access to any organization’s resources, forces many companies to extensively use the easy and straightforward SSL VPN alternative. This is because it requires minimum configuration and it is extensively available to users since it only needs a SSL/TLS-enabled web browser to have access to the intranet. In addition, the rush in the deployment of SSL VPN servers to digest the increasing number of concurrent connections, can be an open window for attackers trying to take advantage of known and potential vulnerabilities to extract private keys, users, and passwords from vulnerable installations or even attempt a zero-day attack.
Other risk vectors are RDP connections, which can be used by unauthorized personnel through the RDP links available at the endpoint or virtual desktop access, and the most common malware attacks on personal computers or devices which are not properly protected with a solid EPP/EDR solution.
In this context, there are some security recommendations for VPN SSL remote access, such as to avoid the obsolete SSLv3 protocol, avoid the use of untrusted SSL certificates (due to potential man-in-the-middle attacks), and use multi-factor authentication when possible, etc.
However, it is clear that active scanning and exploitation attempts won’t cease. Adversaries are quite aware of the situation and will try to take advantage of it. So the questions arising for the security teams of the organizations seem to be:
- Are our current security controls effective against the new threats our remote working infrastructure is facing? Detect Attacks
- Does our current threat intel collection detect threats to our VPN infrastructure? Collect Intel
- Does the intel we collect help us mitigate the increased risk produced by extensive remote working? Proactively Protect

Enterprise Threat Intelligence for a Safer Remote Access
In this scenario, deception techniques can be of great assistance in two main aspects: First of all, to deflect the attacker’s attention from the real assets of the organization like the VPN SSL server to a secure “buffer zone” where the attack is harmless and triggering a first-level alert. Secondly, to analyze the adversaries’ actions carried out within this secure zone by providing actionable intelligence that can be ingested by other security solutions in place for a rapid response to the incoming threat.
To assist in this particular use case, CounterCraft has devised a Threat Intelligence Service for VPN which deflects attacks away from the VPN infrastructure of the organization. The Deception Platform deploys a cloud deception buffer zone with a VPN login portal, emulating industry vendors like Check Point, Cisco, Juniper, OpenVPN, Barracuda, and Fortinet to represent a credible target. It also seeds the internet (Shodan, Censys, Pastebin…) with technical discovery information designed to look like the company’s real VPN, using social engineering techniques against the attackers. This technical discovery information will be placed where it can be found only by a threat actor searching for your organization’s VPN infrastructure.
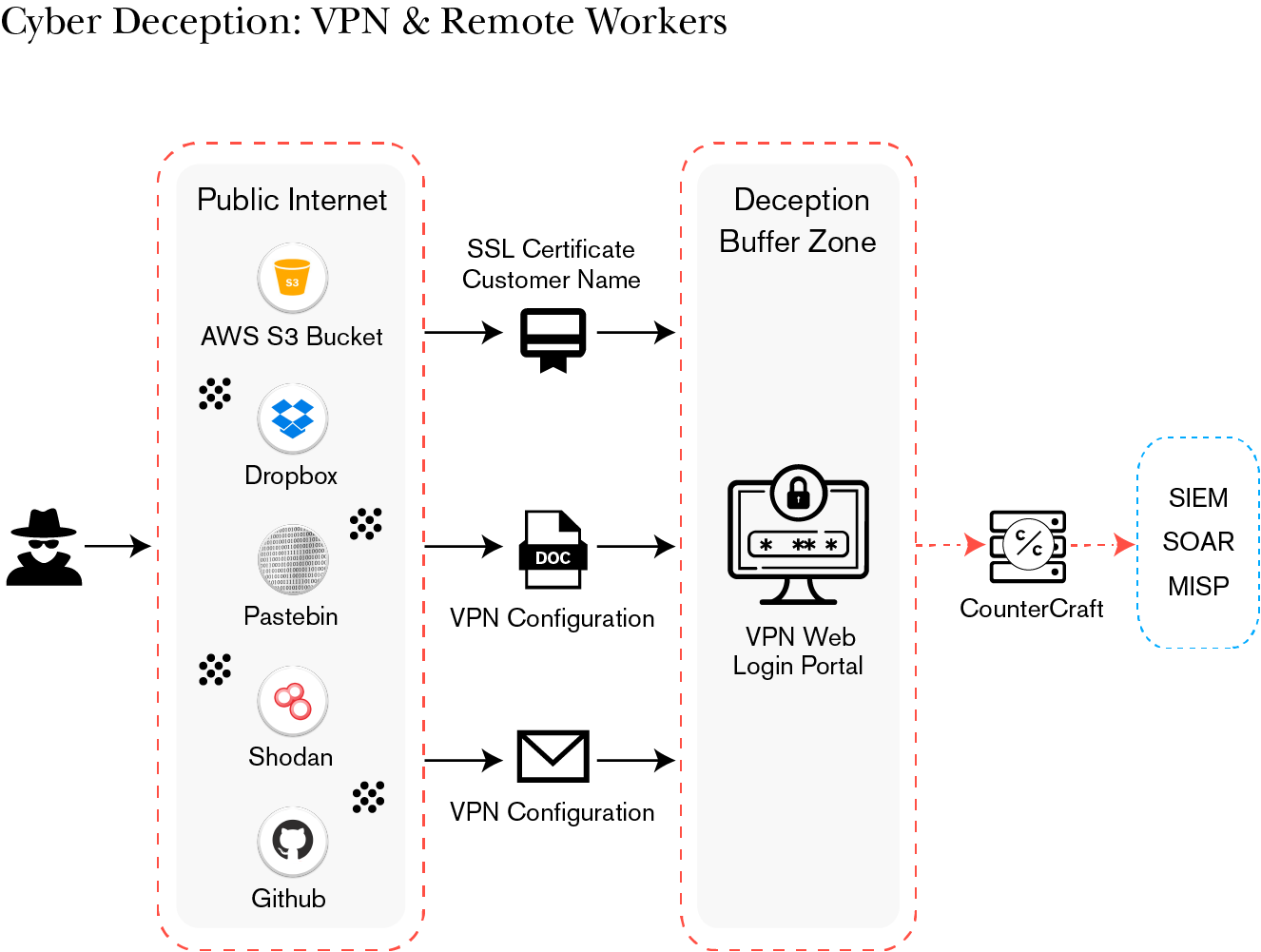
When an attacker interacts with the deception buffer zone, an alert is immediately sent from our console, and enterprise threat intelligence collection begins. The deliverables are actionable threat intelligence data with enrichments in the form of TTPs (MITRE ATT&CK) and IoCs including IP addresses, and credentials used by threat actors. The threat intel data can be sent to external security tools such as MISP, a SIEM or SOAR platforms.
This is how the CounterCraft Cyber Deception Platform can alleviate the associated risks of this situation in a simple, competitive and effective manner. The solution helps the organization get ahead of adversaries by detecting them, slowing them down and getting actionable intelligence to rapidly react to threats. Do you want to know how Cyber Deception can help organizations tackle remote access and VPN risks without business disruption and continuing day-to-day activities?
Join our 30-min On-Demand Webinar and to get started with your first deception campaign, email [email protected] to talk to one of the team about setup and implementation.

Author: Conrado Crespo, Senior Sales Engineer