Digital attacks are assaults, often anonymous, that have a global impact and a huge economic toll. Even so, behind every attack is not some super computer, but a person. Attackers are human, too.
Attackers’ human nature is a weakness to be exploited by defenders in the cybersecurity realm. In previous posts we talked about how knowledge about your assets and network, information your adversaries don’t have (at least, at first glance ), can be used to the defender’s benefit when building a more resilient security solution.
Taking the human nature of the attackers that we want to catch into account when building a defensive deception campaign is a strategic way to increase effectiveness. We could talk about How to Run and Adversary Engagement Operation by MITRE Engage or OODA loop, but we will take a humbler approach and talk about very specific examples on how to take advantage of a human being’s innate habits for incident analysis, cognitive security, and deception campaign design.

Force of Habit
After analyzing several incidents, it doesn’t take long to realize that there are some habits that people can’t easily avoid. Often, this is because they are not aware of the action or its consequences , which is quite useful when analyzing an incident.
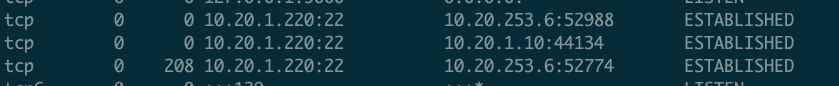
Take the very simple example regarding the habits of the user when dealing with a command line interface. There are patterns each person uses when executing command line utilities with arguments that can be meaningful when analyzing an incident, for example, to distinguish between people accessing the same compromised server. ls or ps are two good examples, but there are more subtle details that could help.
The speed with which the commands are run is different according to the user, and the subconscious act of hitting the return button to clean your display for easier reading of the output of the commands or to clear your mind while thinking on what you are going to write next is something personal. It is sometimes a random number of blank lines that are needed, but sometimes not, there are people that never do that, and people that subconsciously hit the enter button several times. And if this information is being logged by the system, it is a detail that could help to profile the attacker.

“Shell view” for a reverse shell, including blank lines

There are people that group the run commands based on the type of information they want to get, and there are people that just follow a guide, protocol, or have the habit of just running all the needed commands without any specific order (which could be also meaningful if it persists across incidents).

Applying Pressure
Human nature can be also exploited when engaging the actor, because we are prone to making mistakes under pressure. Deception helps create pressure by playing with the human reaction. For example, we might generate some excitement by inserting short-term achievable goals like access to an interesting (fake) host, and then upping the pressure by connecting as sysadmins that start doing live “cleaning”. We can even try to make them less cautious by creating a fictitious threat actor, which they will then attempt to avoid or remove from the equation, actions that expose the threat actor further.
There are more people at this party!

Human Behavior and Attack Trees
Finally, it is also interesting to take into account human nature when designing a fictitious network infrastructure and its attack tree. Humans, as a rule, are lazy and tend to use the low effort path. However, with deception it is important to avoid being too obvious by offering a path that is too easy. In order to keep the level of security similar to the net we are defending, we can play with the pieces of the puzzle needed to pass from one branch of the attack tree to the next.
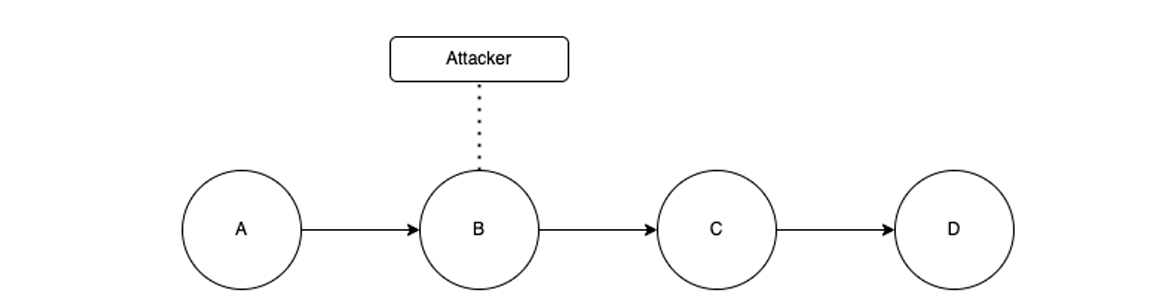
Basic attack path

When designing an attack path, sometimes there is a logical direction to look at. Image 3 represents a basic attack path design. The attacker lands in the B point, and even if the attacker looks around and tries to discover interesting paths, the most logical path (due to network topology, breadcrumbs, etc) directs the attacker to point C, and once that the attacker is looking into that direction, it is probable that the attacker goes for the information at point D before checking what is left at point A. Just think of a regular escape room game. You get a hint at the beginning of a game, but when you get to a more advanced phase of that game, you become stuck because you didn’t pay attention to the earlier hint.

The Complexity of Deception Design
With these basic examples, we realize that designing a deception campaign is not just about adding some assets into your environment. It is also about extending your infrastructure, taking advantage of your knowledge of it, and designing strategically in order to engage with the attacker. Reacting to an attacker’s human nature and leveraging it to push them to make mistakes is the name of the game, and with proper logging you can obtain the details that will allow you to properly analyze the attacker.



Mikel Gastesi, Threat Analyst at CounterCraft, combines his expertise in threat detection and analysis with the power of the Deception technology to get an explosive combination with the best of both worlds. You can find him on LinkedIn.