What is the definition of MTTD?
MTTD stands for Mean Time to Detection. It is the average time it takes to detect or discover a security incident. It is a very important KPI for security incident management. By tracking MTTD, security professionals can use proven metrics to track individual and team progress over an extended period of time.
Metrics are critical, particularly for security teams that want to perform their best. Yet integrating MTTD, MTTF, MTBF, MTTR (Mean time to: fix, between failures, and repair) and other service-level measurements into a company’s day-to-day operations can prove difficult.
How do you calculate MTTD?
To calculate MTTD, take a specific incident and calculate the difference between the start of the incident/interruption to the system and the time it took the team to detect the incident. When you do this with more than one incident, find the MTTD by adding up the times to detect and dividing by the number of incidents.
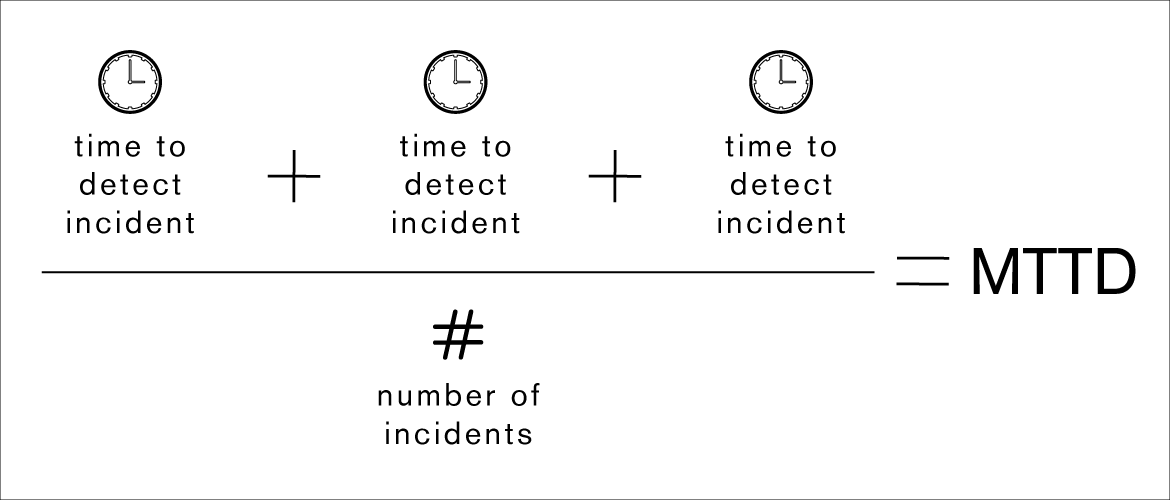
It is not always easy to calculate MTTD—lack of visibility can make it difficult to know when the incident started. However, it’s worth it! These KPIs should empower the security team with data and insights they can use to make meaningful business improvements.
Why is MTTD so important?
It’s a really important KPI for security departments. If they have a low, or very low, MTTD, that means the departments that are in charge of the detection of security incidents are working correctly. If the MTTD is long, the business has a visibility problem and lacks the capability to detect complex security incidents in a reasonable time.
This can affect the businesses’ ability to function, causing profit loss, information leaks, system failure, ransomware resilience, and so on.
Based on our experience, almost 50% of techniques and tactics used for lateral movements are missed. This means that the actual detection/protection techniques are not enough to detect new advanced persistent threats.
What is a good MTTD measurement?
A good MTTD is very relative to a specific organization, but as an example of what organizations should work toward, we can look at the Ryuk ransomware. The Ryuk threat actors went from a phishing email to domain-wide ransomware in 5 hours. They escalated privileges using Zerologon (CVE-2020-1472), less than 2 hours after the initial phishing. They used tools such as Cobalt Strike, AdFind, WMI, and PowerShell to accomplish their objective.
Regardless of the type of security breach that arises , MTTD should be a time close to zero. Unfortunately, that is often not the case. For example, the Solar Winds hack was discovered approximately 9 months after it started. This gives us a whopping nine-month time to detection (TTD). This 6500 hour TTD will pull anyone’s average up.
The Ponemon Institute provides the industry standard benchmark of MTTD. The average time to identify and contain a data breach was 280 days in the 2020 study, nearly identical to the average of 279 days in 2019—which is very close to the nine months recorded in the Solar Winds case.
Based on our experience, almost 50% of techniques and tactics used for lateral movements are missed. This means that the actual detection/protection techniques are not enough to detect new advanced persistent threats.
What steps can an organization take to lower MTTD?
Over the last five years of CounterCraft, we’ve seen our deception campaigns help lower our clients’ MTTD significantly, but deception techniques are just a part of the solution. When it comes to lowering the MTTD, it is important that everything is well coordinated between people, processes, and tools and that the organization has made an investment in security departments.
MTTD is a great metric for security teams that want to track the effectiveness of their incident management tools and processes. If these tools and processes work properly, a security team should have no trouble keeping its MTTD low.
How can deception technology lower MTTD?
Countercraft’s deception-powered threat intel technology, based on breadcrumbs (ActiveLures) and deception environments (ActiveSense), has shown to give great visibility of targeted attacks which are normally the most difficult to detect. We see over and over again with current clients that CounterCraft is the only tool capable of detecting these silent attacks, which are impossible to detect with other types of tools, such as those based on attack signatures or behavior baselines.
Are CounterCraft’s platform and Cloud™ services particularly good at lowering MTTD?
Yes, when a customer realizes, usually late in the game, that they have had a security incident, there has always been prior reconnaissance by the attacker. This preliminary phase of investigation and testing by the attacker is a crucial moment in which we can detect a potential attack and identify the attacker’s tactics, procedures and objectives, before a breach happens. This is where the Countercraft Cloud™ Pre-Breach service helps customers detect attacks at a very early stage, before any damage has been done. In fact, deception-based threat intel solutions are one of the only ways to effectively detect and defeat breach activity before the breach has taken place. It’s a game changer.
Is it better to invest in lowering your MTTR or your MTTD?
It’s important that businesses invest in lowering both MTTR and MTTD. When it comes to MTTR, or Mean Time To Recovery, IT teams have been working for decades to implement different systems that make it possible to recover from an attack.
There is a belief that investing in recovery tools is the only solution, since they will be unable to detect 100% of new attacks. This way of thinking usually leads to major disasters since the lack of visibility causes large security holes that are later more difficult to fix, such as the loss of critical information for the business, often impossible to remedy.
When it comes to MTTD, it is a relatively new term in the security space. It was something that wasn’t measured in the past, or it was simply a side thought. However, due to the increase in state-sponsored attacks on businesses (Solar Winds) and targeted ransomware (Ryuk), reducing MTTD times is more relevant than ever. Therefore, it is important that businesses today have different systems that can help reduce MTTD. Reducing MTTD is a greater focus now than before, and it is being invested in at a greater rate.
How can lowering your MTTD help to lower MTTR and MTTF?
To fix a failure or a crash, an incident must first occur. If we are able to detect incidents at a very early stage, we will significantly reduce MTTR and MTTF. The response teams will have less incidents to investigate, and will be able to dedicate more of their scarce resources to rectifying the incident quicker than before. So, investment in MTTD reduction (by, for example, buying Countercraft Cloud™ service) directly reduces MTTD, and the drop in both the number and severity of incidents brings down the MTTR and MTTF metrics. It’s a win for everyone.

Adversary-generated Threat Detection Powered by Deception
CounterCraft provides actionable threat intelligence in real time using deception technology. Unlike comparable technology, which takes up to 270 days to provide threat intelligence that requires an analyst to determine if it’s relevant or not, CounterCraft delivers intelligence generated by your adversaries, in real time, that enables you to implement remediation immediately. Active defense allows organizations to identify unknown risks and threats tailored to their external and internal attack surface and delivers detailed telemetry.
